
Sicurezza dei dati nel cloud
e conformità
per lo sviluppo
dell'elettronica
Proteggi e migliora
la progettazione elettronica con
strumenti avanzati di sicurezza e conformità
Proteggi e migliora
la progettazione elettronica con
strumenti avanzati di sicurezza e conformità
Summary
I team di progettazione elettronica dipendono da solide misure di sicurezza e strumenti di conformità che salvaguardano la proprietà intellettuale supportando al contempo una collaborazione efficiente.
Basic security measures are no longer enough to protect the full scope of today’s electronics design workflows. Cloud‑based security and compliance capabilities have grown into a system that connects teams, protects design data, and supports regulatory requirements from early design through production. These capabilities include advanced encryption, governed access controls, and real‑time monitoring that strengthen protection at every stage.
This resource gives IT security professionals and engineering managers a clear view of cloud‑based electronics design data protection, covering both foundational concepts and strategies for managing complex projects and cross‑team collaboration.
Cloud data protection is the starting point for controlling access, supporting collaboration, and maintaining design data integrity. It must be set up and managed throughout the entire product lifecycle. This overview also highlights how successful design teams apply cloud security and compliance practices, and how these choices influence productivity and regulatory readiness.
Qual è la differenza tra sicurezza e conformità dei dati?
Qual è la differenza tra sicurezza e conformità dei dati?
Security and compliance are distinct but closely related parts of protecting intellectual property in the electronics design process. Understanding the difference will help you safeguard your design data.
Security
Security focuses on the measures used to shield electronics design data from unauthorized access, breaches, theft, and other threats. It includes the tools, controls, and practices that protect intellectual property from both internal and external risks. At its core, security is about preventing unwanted access and maintaining data integrity throughout the design process.
Compliance
Compliance focuses on meeting established standards, regulations, and internal policies. It reflects whether an organization has the required controls in place to protect sensitive information and demonstrate accountability to regulators, customers, and partners.
La sicurezza è la protezione vera e propria, mentre la conformità è la dimostrazione e la documentazione della protezione.
The relationship between the two is closely linked:
- Strong security measures support compliance.
- Compliance frameworks provide structure for implementing security.
- Both are required for a complete approach to data protection.
For electronics design teams, this distinction matters because different industries have varying compliance requirements. Defense contractors may need to meet CMMC or ITAR compliance requirements, medical device manufacturers must comply with FDA and EMA regulations, and companies handling European customer data need to adhere to GDPR standards.
Cloud-based tools offer significant cloud security compliance advantages by providing built-in controls and documentation capabilities that streamline these compliance processes as they maintain strong security.
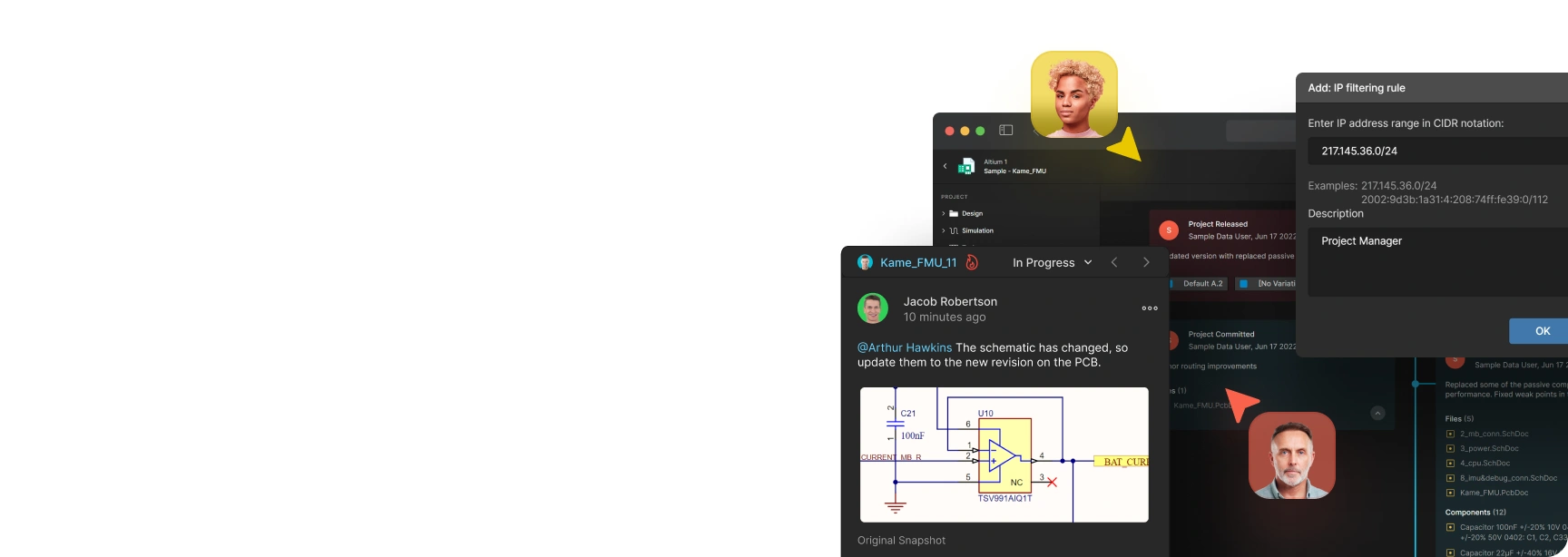
Mantenere la conformità con il governo degli Stati Uniti,
proteggere la proprietà intellettuale e
collaborare in modo sicuro
Cloud vs On-premises: qual è la soluzione giusta per te?
Cloud vs On-premises: qual è la soluzione giusta per te?
Choosing how to secure your electronics design data starts with deciding between cloud‑based and on‑premises security solutions. Each option brings its own strengths and trade‑offs that influence your team’s productivity, security posture, and compliance capabilities.
On-Premises Security: Traditional Control
On-premises security puts your data and security infrastructure entirely within your organization's physical control. Your team manages dedicated servers, hardware security modules, and all associated security infrastructure within your facilities.
Advantages:
- Physical control over all IT infrastructure containing your design data
- No reliance on internet connectivity for access to local files
- Full customization of security configurations
- Useful for compliance scenarios with strict data residency requirements
Challenges:
- Significant investment in hardware and security infrastructure
- Requires specialized in‑house security expertise for maintenance and updates
- Limited geographic redundancy increases vulnerability to localized disasters
- Scaling is limited as teams and projects grow
- Security updates must be applied manually, often causing delays
- Remote collaboration typically depends on complex VPN setups
Cloud Data Security: Advanced Protection
Cloud-based data security leverages specialized providers' expertise and infrastructure to protect your design data, typically delivering enterprise-grade security at a fraction of the cost of building equivalent systems in-house.
Advantages:
- Advanced encryption methods with state-of-the-art protection protocols
- Geographic redundancy across multiple secure data centers
- Centralized security management with comprehensive access controls
- Automated updates and security patches without disruption
- Detailed activity logs and audit trails for tracking access
- Simplified secure collaboration for distributed teams
- Lower total cost of ownership for most organizations
- Rapid scalability to accommodate growing teams and projects
- Superior disaster recovery and business continuity capabilities
Challenges:
- Internet connectivity is required for access to cloud‑hosted data
- Provides less direct physical control over infrastructure
- Requires careful vendor evaluation to meet compliance needs
- Some industries may have strict requirements for data residency or export controls
Making the Right Choice
For modern electronics design teams, the switch to cloud solutions increasingly depends on specific requirements:
Team Distribution
Globally distributed teams benefit significantly from cloud solutions that support secure collaboration without complex networking.
Budget Constraints
Cloud solutions typically offer enterprise-grade security with predictable subscription costs rather than large, uneven capital expenditures.
Compliance Requirements
While both solutions can address compliance needs, cloud providers increasingly offer specialized compliance certifications and documentation.
Technical Resources
Organizations without dedicated security specialists often achieve better security outcomes with cloud solutions that provide managed security services.
Many organizations are finding that a cloud‑based approach to security delivers the right balance of protection, cost efficiency, and collaboration for electronics design teams. It also provides purpose‑built capabilities that address the unique requirements of PCB design data and multi‑team workflows.
For others, a hybrid approach — combining cloud‑based security with selective offline capabilities — delivers the best results. This allows teams to continue working during internet disruptions while maintaining strong security controls.
I vantaggi degli strumenti di collaborazione cloud rispetto al vecchio metodo
I vantaggi degli strumenti di collaborazione cloud rispetto al vecchio metodo
For years, electronics design teams have worked around siloed systems and clunky file‑sharing just to stay secure. It’s a model that protects data but slows everything else. Cloud collaboration tools flip that script, giving teams stronger security and smoother collaboration in the same environment.
Centralized Cloud Data Security
Traditional design environments spread data across local machines, shared drives, and email attachments, creating a wide surface area to protect. Cloud collaboration platforms bring everything into one secure place, with:
- Encryption applied in transit and at rest
- Consistent access controls across all design assets
- Real‑time monitoring for unusual or unauthorized activity
- Controlled sharing that stays secure when working with partners
- Clear audit trails showing who accessed or changed what
This centralization significantly reduces vulnerabilities compared to traditional file-sharing methods and enables security teams to implement stronger protections around a single controlled environment.
Mitigating Growing Cyber Threats
Cyber threats continue to accelerate, and electronics design teams are navigating a more complex landscape than ever. Projections show global cybercrime costs climbing sharply, with estimates reaching up to $23 trillion by 2027 as attacks become more automated and more frequent. Manufacturing remains one of the most targeted sectors, and ransomware activity continues to rise year over year.
Recent incidents across the industry show how disruptive these attacks can be. Communications & Power Industries (CPI), a supplier to the U.S. Department of Defense and DARPA, was hit by ransomware that encrypted critical data and shut down thousands of systems. CPI ultimately paid $500,000 to regain access.
Semikron, a German power electronics manufacturer with operations across 24 global subsidiaries, suffered a similar attack that partially encrypted its IT systems and files. These cases highlight how even well‑established companies can be exposed — and how costly recovery becomes once an attack is underway.
Cloud security platforms help address these threats through:
- Continuous security updates and patches without disrupting workflows
- Advanced threat detection utilizing artificial intelligence and pattern recognition
- Automated backups enabling rapid recovery from ransomware attacks
- Geographic redundancy that protects business continuity even during localized disasters
- 24/7 expert security monitoring for emerging threats
Streamlined Compliance Management
Regulatory compliance requirements continue to evolve and expand, creating significant administrative burdens for electronics design teams. Cloud collaboration tools simplify compliance through built-in controls aligned with major regulatory frameworks and automated documentation capabilities. They ensure consistent application of security policies across all design data while providing simplified auditing with comprehensive activity logs, ultimately reducing the administrative overhead needed to maintain compliance.
Enabling Secure Collaboration Without Boundaries
Cloud collaboration tools transform productivity by removing barriers while upholding strong security protections. They allow teams to access designs securely from anywhere, simplify onboarding processes, and enable controlled sharing with external partners. Teams benefit from real-time design reviews with managed stakeholder access and robust version control that prevents conflicts and protects data integrity throughout the collaborative process.
Cost Optimization Through Shared Resources
Data security in the cloud delivers significant cost advantages over traditional approaches by offering:
- Elimination of expensive on-premise security infrastructure
- Reduced need for specialized security personnel
- Predictable subscription-based pricing aligned with actual usage
- Minimized downtime and business disruption from security incidents
- Lower environmental impact through shared resources
Real-World Impact
The move to cloud collaboration tools delivers measurable benefits for electronics design teams. Improved collaboration reduces design cycle times, while significantly reducing the risk of intellectual property theft. Teams gain improved visibility into design progress and project status, enhance their adaptability to evolving security threats, and build greater resilience against disruptions ranging from cyber attacks to natural disasters.
Best practice per la protezione degli ambienti di sviluppo basati su cloud
Best practice per la protezione degli ambienti di sviluppo basati su cloud
Transitioning a design team to a cloud-based development environment requires thoughtful implementation. The following best practices will help your organization protect your intellectual property while promoting efficient collaboration.
Establish Robust Cloud Data Protection Measures
Cloud security ultimately centers on protecting your valuable intellectual design property.
- Ensure data encryption at rest and in transit using industry-standard methods
- Implement secure file-sharing processes for collaboration with external partners
- Establish version control and backup procedures to prevent data loss
- Create data retention and deletion policies aligned with business requirements
Monitor and Respond to Security Events
Effective security requires constant vigilance and the ability to respond quickly to potential threats.
- Implement comprehensive logging of all system and user activities
- Integrate with Security Information and Event Management (SIEM) tools
- Establish automated alerts for suspicious activities
- Create and test incident response procedures for potential security breaches
- Conduct regular security reviews to identify and address emerging risks
Manage Third-Party Risk
Cloud environments often involve multiple providers, each requiring appropriate security scrutiny.
- Conduct thorough vendor security assessments before implementation
- Review vendor compliance certifications relevant to your industry
- Establish security requirements in vendor contracts with clear responsibilities
- Perform periodic reassessments of vendor security practices
- Develop contingency plans for potential vendor security incidents
Plan for Business Continuity
Cloud environments offer superior resilience but still require robust continuity planning.
- Test backup and restoration capabilities regularly
- Create disaster recovery procedures specific to cloud environments
- Establish alternate access methods for critical operations during outages
- Document recovery time objectives for different systems and data
- Conduct periodic tabletop exercises to validate continuity plans
With thoughtful implementation of these best practices, electronics design teams can create comprehensive and collaborative cloud development environments that deliver superior security and align controls with specific business requirements and risk profiles.
Dai un'occhiata al nostro hub educativo!
Webinar gratuiti, corsi approfonditi e molto altro ancora a tua disposizione.
Letture consigliate

Whitepaper
Approccio e pratiche di sicurezza di Altium 365
Dai un'occhiata approfondita all'architettura di sicurezza di Altium 365.

Webinar
L'anatomia della conformità IT
Esplora le strategie pratiche per salvaguardare la proprietà intellettuale.

articolo
Perché dare priorità alla sicurezza dei dati nel cloud
Scopri perché la sicurezza del cloud offre una protezione superiore nel panorama odierno delle minacce.
Domande frequenti
La sicurezza del cloud sfrutta l'infrastruttura di fornitori specializzati per offrire una protezione avanzata, tra cui ridondanza geografica, aggiornamenti continui e gestione centralizzata. La sicurezza on-premise si basa su hardware e software gestiti on-premises, che fornisce un controllo fisico ma richiede maggiori investimenti in infrastrutture e competenze. La maggior parte delle organizzazioni ora scopre che la sicurezza del cloud offre una protezione superiore con un costo totale di proprietà inferiore.
Le piattaforme di sicurezza cloud in genere includono controlli di conformità integrati, documentazione automatizzata e registrazione di controllo completa. Queste funzionalità semplificano l'aderenza agli standard di settore e ai requisiti normativi fornendo un'applicazione coerente delle policy di sicurezza e una reportistica semplificata per gli audit. Le principali piattaforme cloud mantengono le certificazioni per i principali framework di conformità, riducendo l'onere amministrativo della documentazione.
A seconda del settore, le certificazioni importanti includono SOC 2 Type 2 per le pratiche di sicurezza generali, ISO 27001 per la gestione della sicurezza delle informazioni, la conformità al GDPR per la gestione dei dati europei e certificazioni specifiche del settore come l'HIPAA per l'assistenza sanitaria o l'ITAR per i progetti di elettronica per la difesa. Verifica se il fornitore possiede le certificazioni correnti pertinenti all'ambiente normativo.
Le piattaforme di sicurezza cloud consentono una collaborazione esterna sicura attraverso la condivisione controllata con autorizzazioni precise, la registrazione di audit completa di tutti gli accessi, la crittografia dei dati condivisi e la possibilità di revocare immediatamente l'accesso quando non è più necessario. La sicurezza delle soluzioni di storage e collaborazione su cloud offre una protezione significativamente migliore rispetto ai tradizionali metodi di condivisione di file quando si lavora con produttori a contratto, clienti o altre parti interessate esterne.
Le piattaforme di sicurezza cloud in genere implementano la ridondanza geografica su più data center, sistemi di backup automatici con funzionalità di ripristino point-in-time e protocolli completi di disaster recovery. Queste misure garantiscono la continuità aziendale anche in caso di interruzioni significative, con tempi di ripristino di gran lunga superiori ai tradizionali approcci on-premises.
Sì, le moderne soluzioni di sicurezza e conformità dei dati nel cloud includono integrazioni sicure tra piattaforme di progettazione e strumenti di gestione progetti come Jira. Queste integrazioni mantengono la sicurezza attraverso connessioni API autenticate e controlli di accesso coerenti, garantendo che le attività, i problemi e i commenti rimangano aggiornati in entrambi i sistemi senza compromettere la sicurezza.
Molte piattaforme di sicurezza cloud offrono funzionalità offline che mantengono i controlli di sicurezza durante le interruzioni di internet. Copie locali salvate nei computer mantengono i controlli di sicurezza appropriati e, quando viene ripristinata la connettività, le modifiche si sincronizzano nel cloud con un'adeguata convalida della sicurezza.