Administratorzy Enterprise Server mogą skonfigurować i włączyć na serwerze funkcje Single Sign-On (SSO). System konfiguracji backendu umożliwia administratorom skonfigurowanie, przetestowanie, włączenie i wyłączenie funkcji SSO dla użytkowników serwera. Opcja SSO jest dostępna podczas logowania do interfejsu przeglądarkowego Enterprise Server. Po skonfigurowaniu dla użytkowników serwera SSO zapewnia wygodę dostępu do serwera przy użyciu tego samego zestawu poświadczeń, który obowiązuje w systemach firmowych.

-
Jeśli użycie SSO jest wymuszone (opcja Enforce SSO (not applied to access from localhost) jest włączona na stronie Admin – Settings – Authentication w interfejsie przeglądarkowym), użytkownicy zobaczą stronę logowania SSO bezpośrednio po wejściu na adres Enterprise Server.
-
Dostęp SSO można również wykorzystać podczas łączenia się z Workspace w Enterprise Server z poziomu Altium Designer. Więcej informacji znajduje się na stronie Accessing Your Workspace.
Więcej informacji o dostępie do interfejsu przeglądarkowego Enterprise Server znajduje się na stronie Exploring the Browser-based Interface.
W przypadku korzystania z wewnętrznego dostawcy tożsamości (Identity Provider) Enterprise Server musi ufać certyfikatowi HTTPS używanemu przez tego dostawcę. W przeciwnym razie podczas próby nawiązania z nim połączenia z poziomu Enterprise Server pojawi się błąd. Dostawcy tożsamości od głównych producentów (Okta, Entra ID itp.) domyślnie mają poprawne, zaufane certyfikaty.
SAML Single Sign-On
Po skonfigurowaniu i włączeniu w Enterprise Server system SSO ustanawia autoryzowane tożsamości z wybranego w firmie dostawcy tożsamości (IdP), na przykład Okta, OneLogin itd., przy czym komunikacja asercji tożsamości opiera się na ustandaryzowanym Security Assertion Markup Language (SAML 2.0). Interfejs logowania SSO w Twojej firmie, jeśli nie jest jeszcze wdrożony, zwykle bazuje na szablonie lub przykładzie dostarczonym przez IdP – inicjuje to wymianę asercji uwierzytelniania opartą o SAML i zapewnia dostęp do usług firmowych.
Gdy w polu rozwijanym SSO na stronie Admin – Settings – Authentication interfejsu przeglądarkowego zostanie wybrana opcja SAML, strona pokazuje wstępnie skonfigurowane adresy URL usługi SSO dla Enterprise Server (Altium Metadata Configuration) oraz możliwość przesłania lub ręcznego wprowadzenia danych połączenia autoryzacyjnego IdP (SAML Identity Provider Configuration).

Metadane konfiguracji IdP powinny być dostępne u dostawcy tożsamości po skonfigurowaniu integracji z usługami firmowymi – patrz przykłady integracji IdP poniżej. Aby skonfigurować system SAML SSO w Enterprise Server (jeśli nie zostało to jeszcze wykonane), użyj przycisku  , aby wskazać i przesłać plik XML konfiguracji SAML IdP wygenerowany przez firmowy IdP. Przesłany plik XML IdP jest analizowany przez system w celu wyodrębnienia głównych pól konfiguracji (X509 Certificate, adres URL Identity Provider Issuer oraz IdP Single Sign-On URL). Alternatywnie można ręcznie dodać poszczególne elementy (certyfikat bezpieczeństwa i adresy URL) konfiguracji do odpowiednich pól.
, aby wskazać i przesłać plik XML konfiguracji SAML IdP wygenerowany przez firmowy IdP. Przesłany plik XML IdP jest analizowany przez system w celu wyodrębnienia głównych pól konfiguracji (X509 Certificate, adres URL Identity Provider Issuer oraz IdP Single Sign-On URL). Alternatywnie można ręcznie dodać poszczególne elementy (certyfikat bezpieczeństwa i adresy URL) konfiguracji do odpowiednich pól.
SSO nie jest włączone, dopóki nie zostanie uruchomiony test integracji, wywoływany przyciskiem  . Weryfikuje to proces tożsamości SSO oraz firmowe logowanie SSO. Po pomyślnym przetestowaniu konfiguracji możesz zapisać ustawienia, klikając przycisk
. Weryfikuje to proces tożsamości SSO oraz firmowe logowanie SSO. Po pomyślnym przetestowaniu konfiguracji możesz zapisać ustawienia, klikając przycisk  (
( ), co skutecznie zastosuje je w Enterprise Server.
), co skutecznie zastosuje je w Enterprise Server.
Jeśli SSO zostanie później wyłączone, ręcznie lub w odpowiedzi na zmianę konfiguracji, dostępny stanie się przycisk  , aby można było powtórzyć proces testowania.
, aby można było powtórzyć proces testowania.
Przykłady integracji z dostawcą tożsamości
Rozwiń poniższą zwijaną sekcję, aby zobaczyć przykład krok po kroku procesu integracji dla OneLogin jako dostawcy tożsamości.
Integration with OneLogin
-
Zaloguj się do OneLogin jako administrator.
-
Wybierz Applications, a następnie Add Apps.
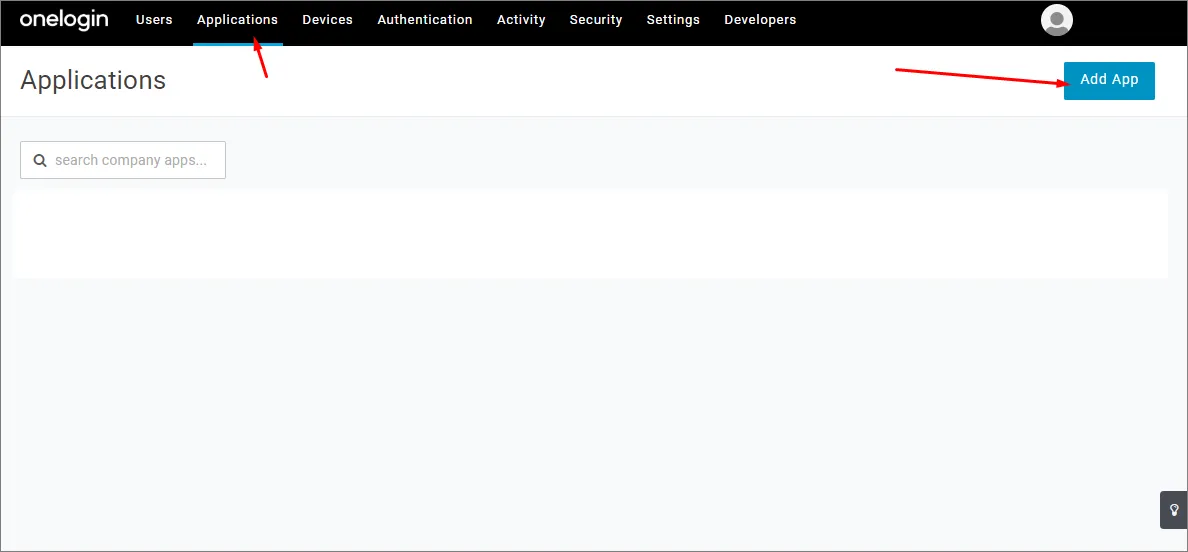
-
Wyszukaj „SAML” i wybierz opcję aplikacji IdP SAML Test Connector (Advanced).
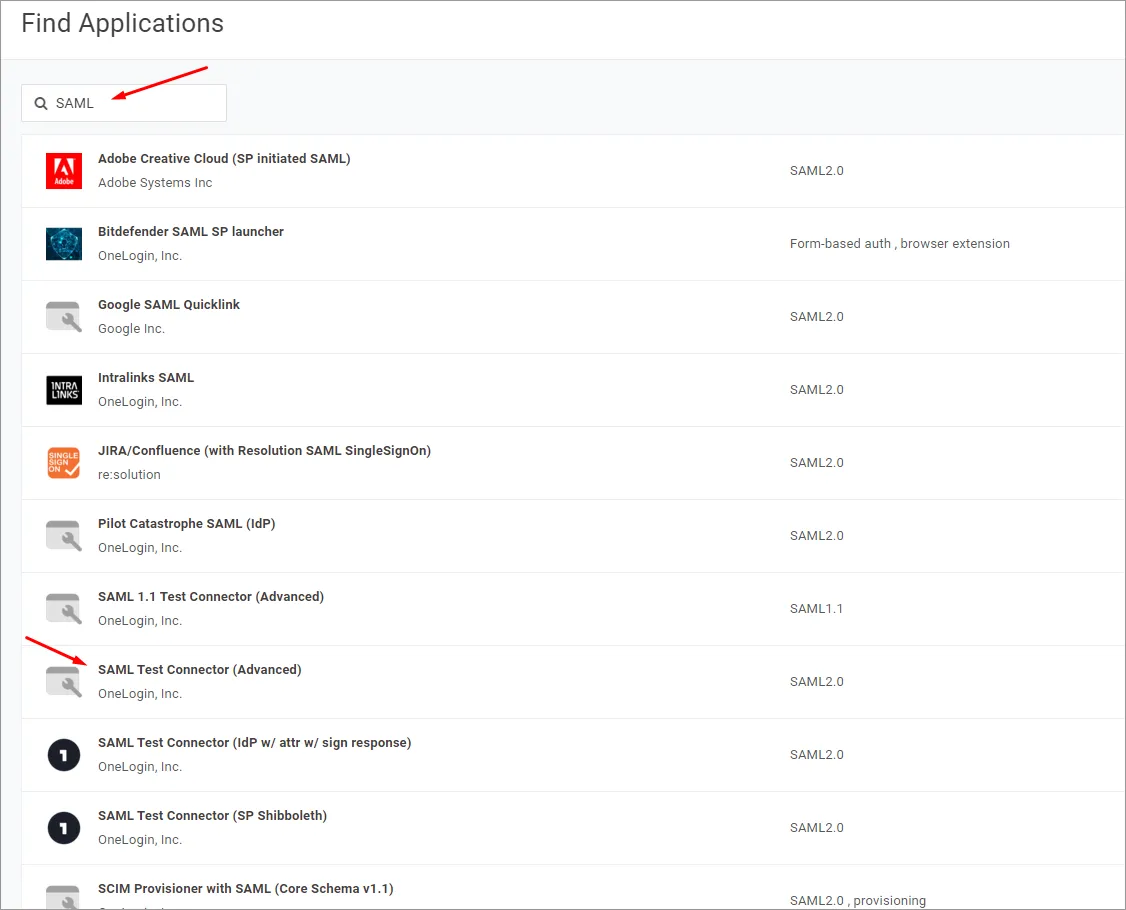
-
Podaj nazwę aplikacji (Display Name). Służy ona wyłącznie do celów wyświetlania.
-
Kliknij przycisk Save.
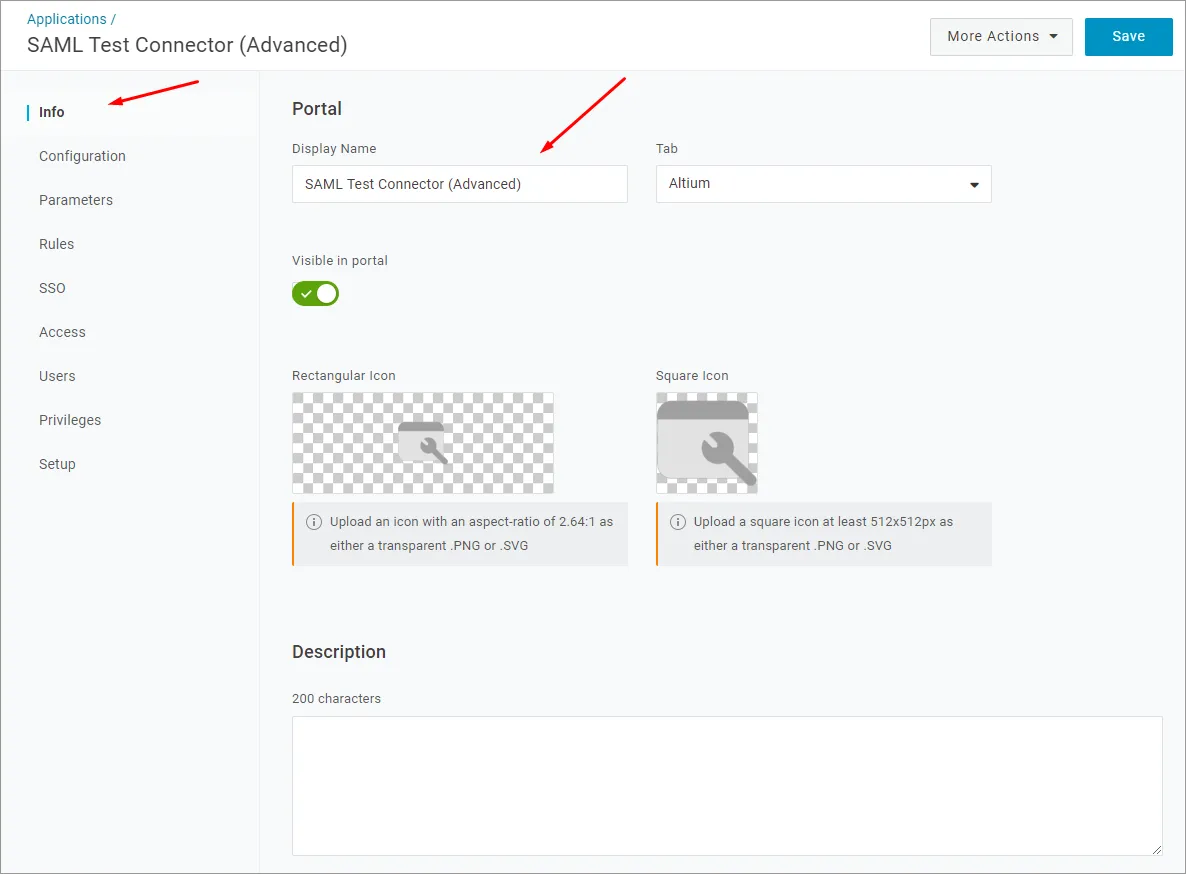
-
Skopiuj ( ) wpisy Entity ID oraz Single Sign-On URL (Assertion Consumer Service) ze strony Admin – Settings – Authentication interfejsu przeglądarkowego Enterprise Server do pól zgodnie z poniższą specyfikacją.
) wpisy Entity ID oraz Single Sign-On URL (Assertion Consumer Service) ze strony Admin – Settings – Authentication interfejsu przeglądarkowego Enterprise Server do pól zgodnie z poniższą specyfikacją.

W konfiguracji aplikacji OneLogin:
-
Wklej powyższy Entity ID (nazwa dostawcy usług) jako adres URL Audience (EntityID).
-
Wklej powyższy Single Sign-On URL (Assertion Consumer Service) jako ACS (Consumer) URL Validator.
-
Wklej także Single Sign-On URL (Assertion Consumer Service) jako ACS (Consumer) URL.
-
Pola RelayState, Recipient, Single Logout URL i Login URL można pozostawić puste.
-
Upewnij się, że opcja SAML nameID format jest ustawiona na Email, a SAML signature element jest ustawione na Both. Kliknij przycisk Save, aby potwierdzić ustawienia.
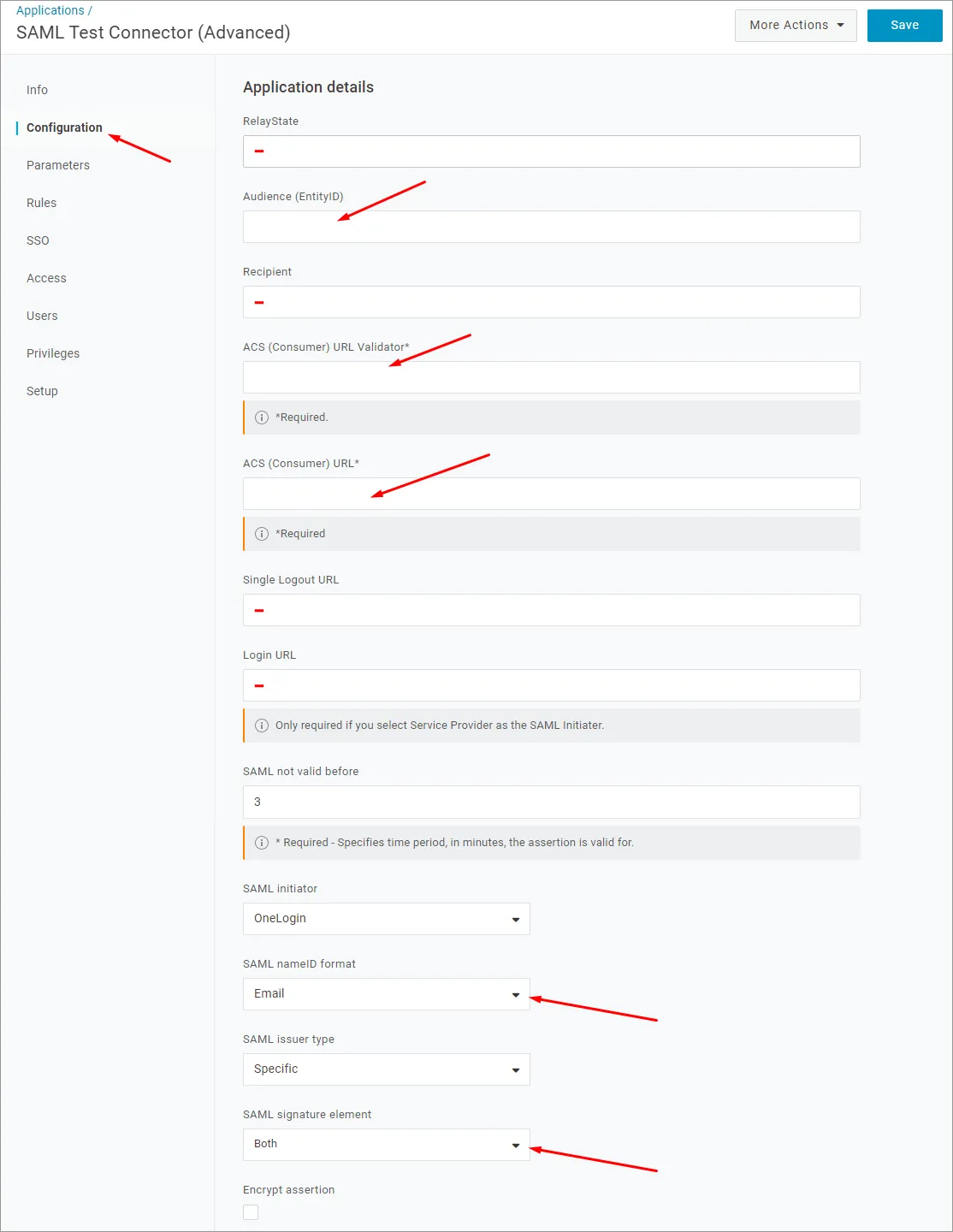
-
Kliknij przycisk More Actions, a następnie wybierz opcję menu SAML Metadata, aby pobrać metadane SAML dostawcy tożsamości jako plik XML.
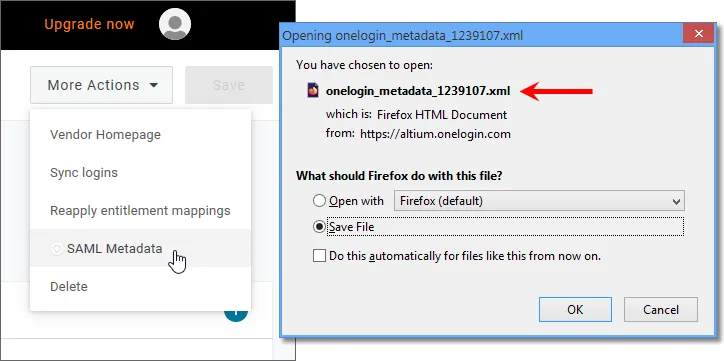
-
Ten plik metadanych zostanie przesłany na stronie Admin – Settings – Authentication interfejsu przeglądarkowego Enterprise Server w celu skonfigurowania usługi OneLogin SSO – patrz poniżej.
-
Jeśli preferowana jest ręczna konfiguracja usługi OneLogin SSO w Enterprise Server, wymagane parametry można znaleźć, wybierając opcję menu SSO w interfejsie aplikacji OneLogin.
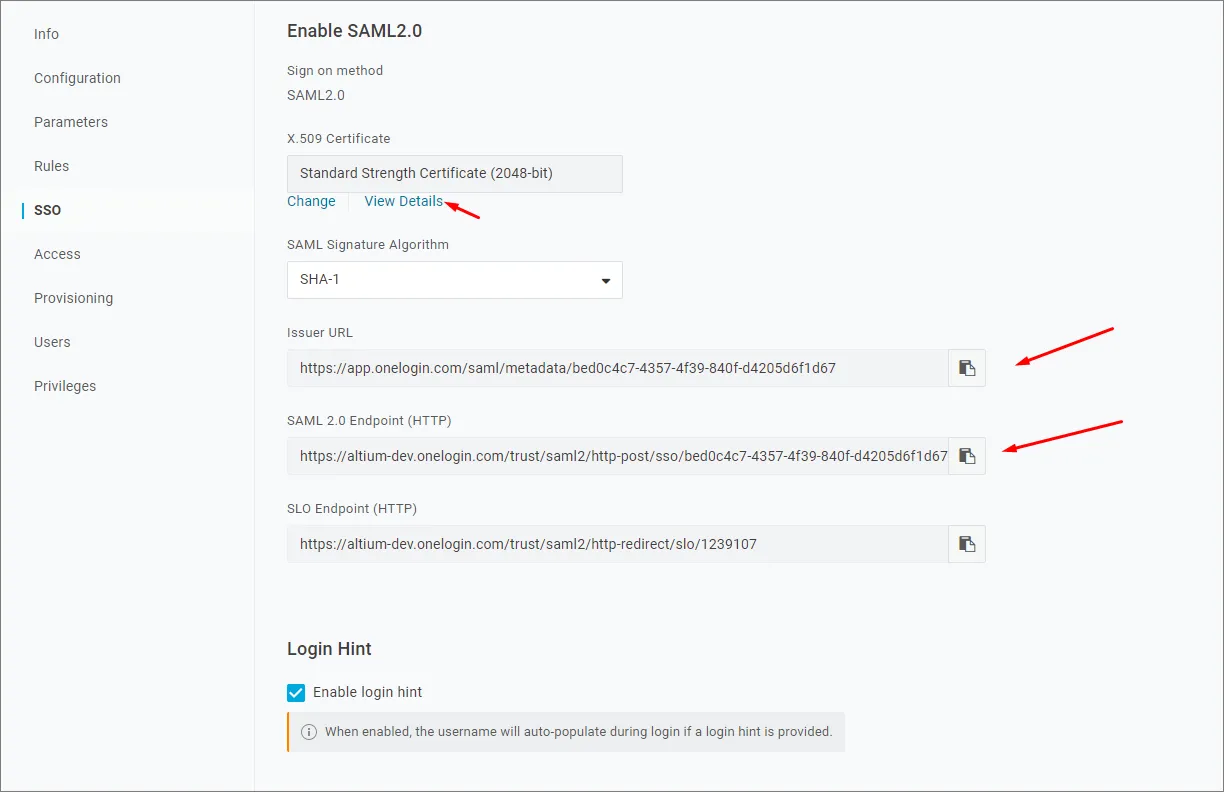
-
Kolejne kroki to dodanie użytkowników i przypisanie aplikacji do tych użytkowników.
Rozwiń poniższą zwijaną sekcję, aby zobaczyć przykład krok po kroku procesu integracji dla Okta jako dostawcy tożsamości.
Integration with Okta
-
Zaloguj się do Okta jako administrator.
-
Kliknij łącze/przycisk Admin, a następnie przycisk Add Application w obszarze firmowym Applications.
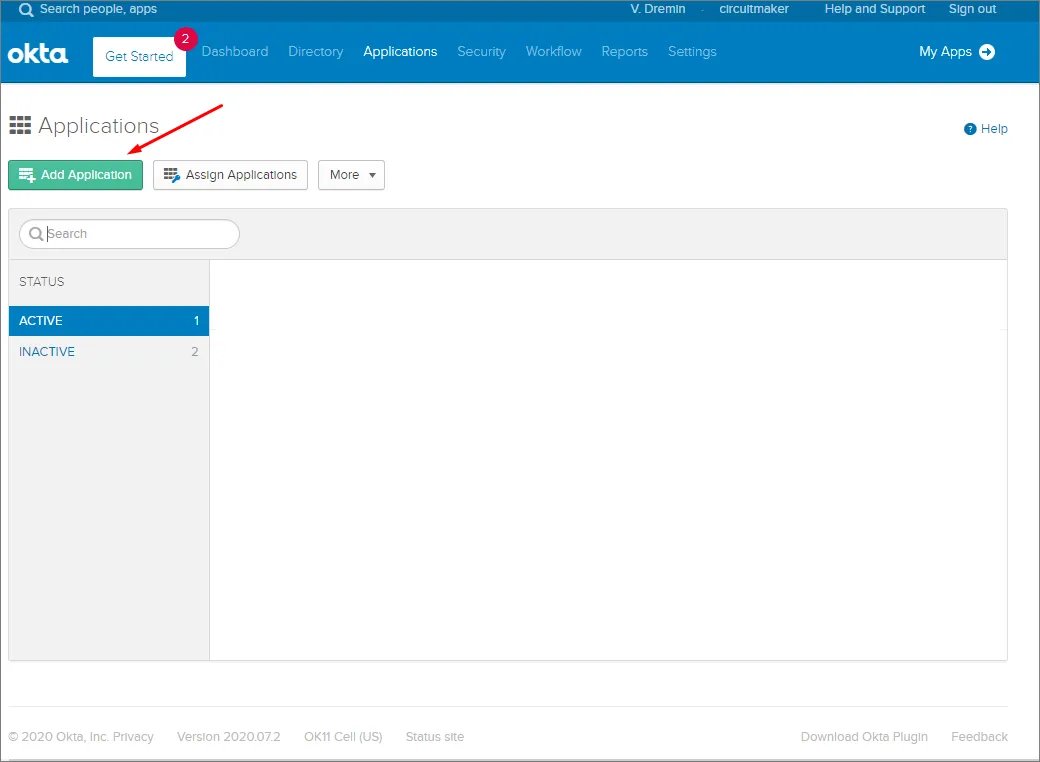
-
Kliknij przycisk Create New App.

-
Wybierz SAML 2.0 jako Sign-on method.
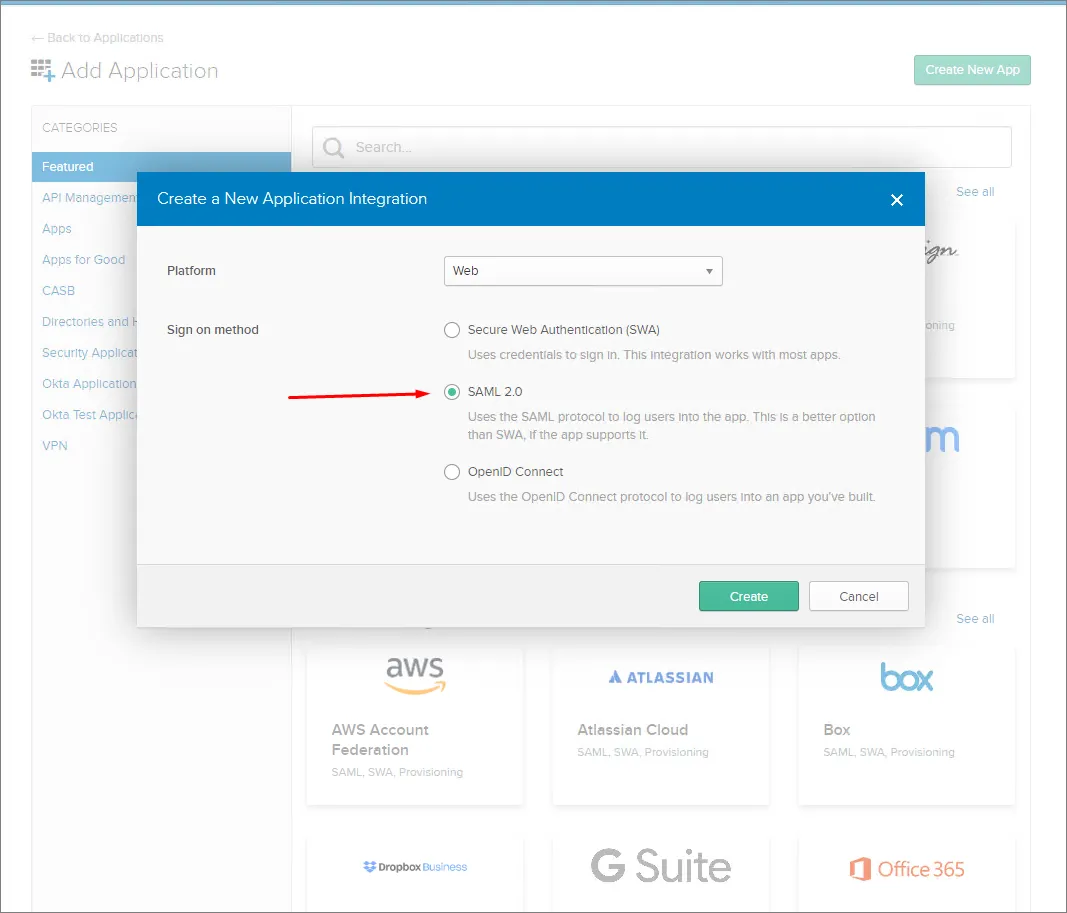
-
Podaj App name. Służy to wyłącznie do celów wyświetlania.
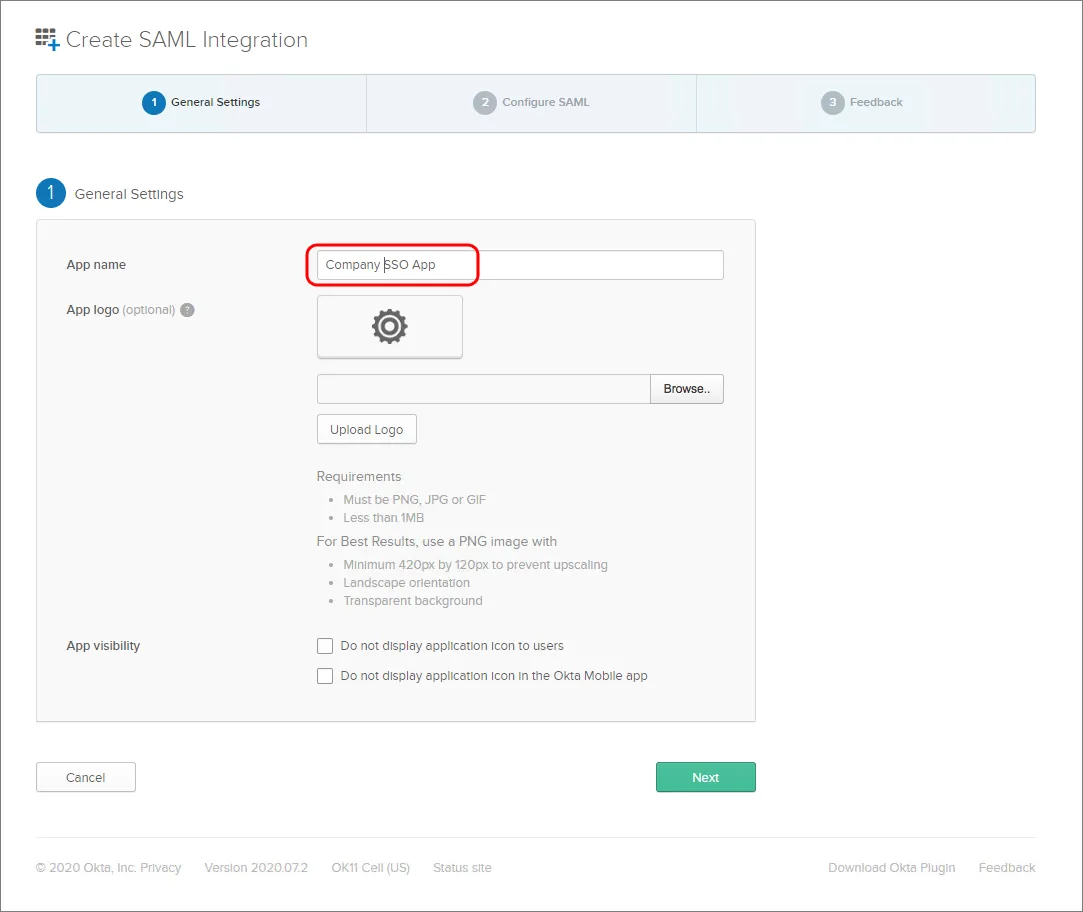
-
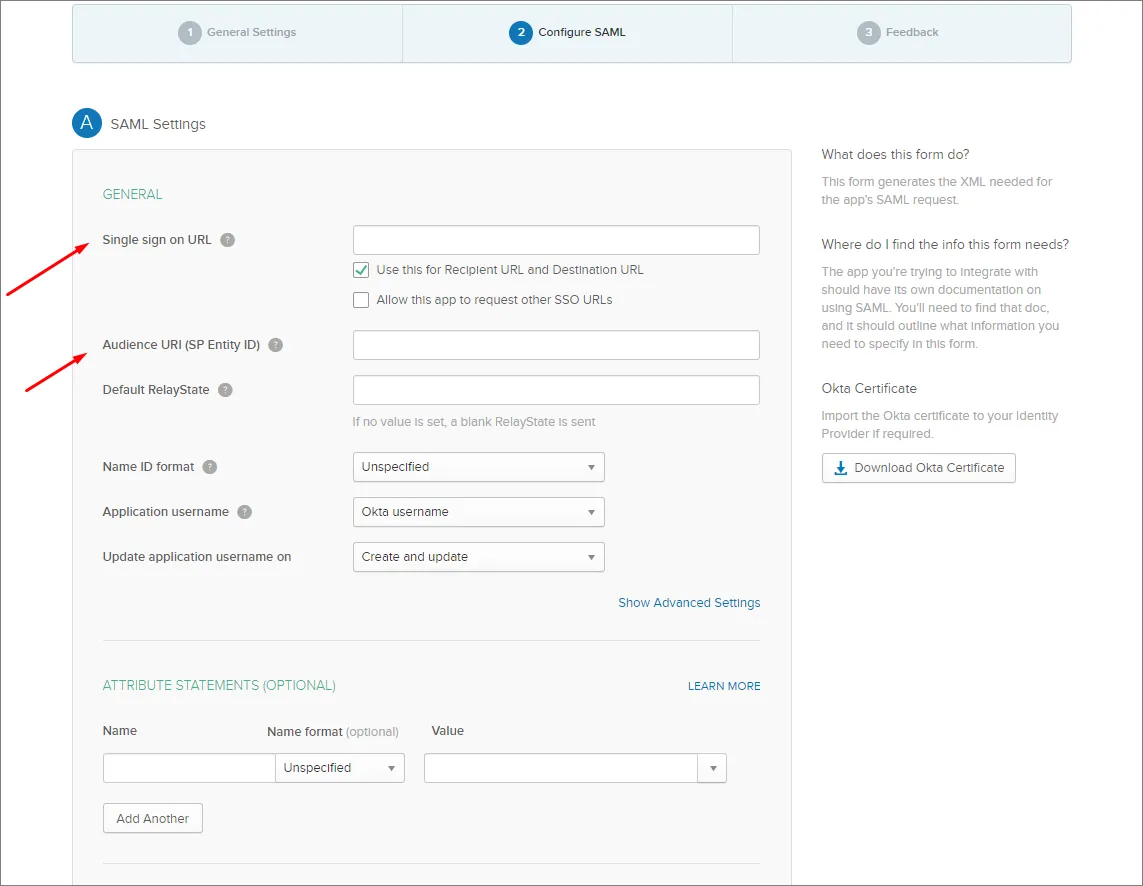
Zanotuj wpisy Single Sign On URL (Assertion Consumer Service) oraz Entity ID na stronie Admin – Settings – Authentication interfejsu przeglądarkowego Enterprise Server.

-
Skopiuj ( ) i wklej wpis Enterprise Server Single Sign-On URL do pola Single sign on URL w ustawieniach Okta SAML.
) i wklej wpis Enterprise Server Single Sign-On URL do pola Single sign on URL w ustawieniach Okta SAML.
-
Skopiuj ( ) i wklej wpis Enterprise Server Entity ID do pola Audience URI w ustawieniach Okta SAML.
) i wklej wpis Enterprise Server Entity ID do pola Audience URI w ustawieniach Okta SAML.
Wpis Default RelayState nie jest wymagany.
-
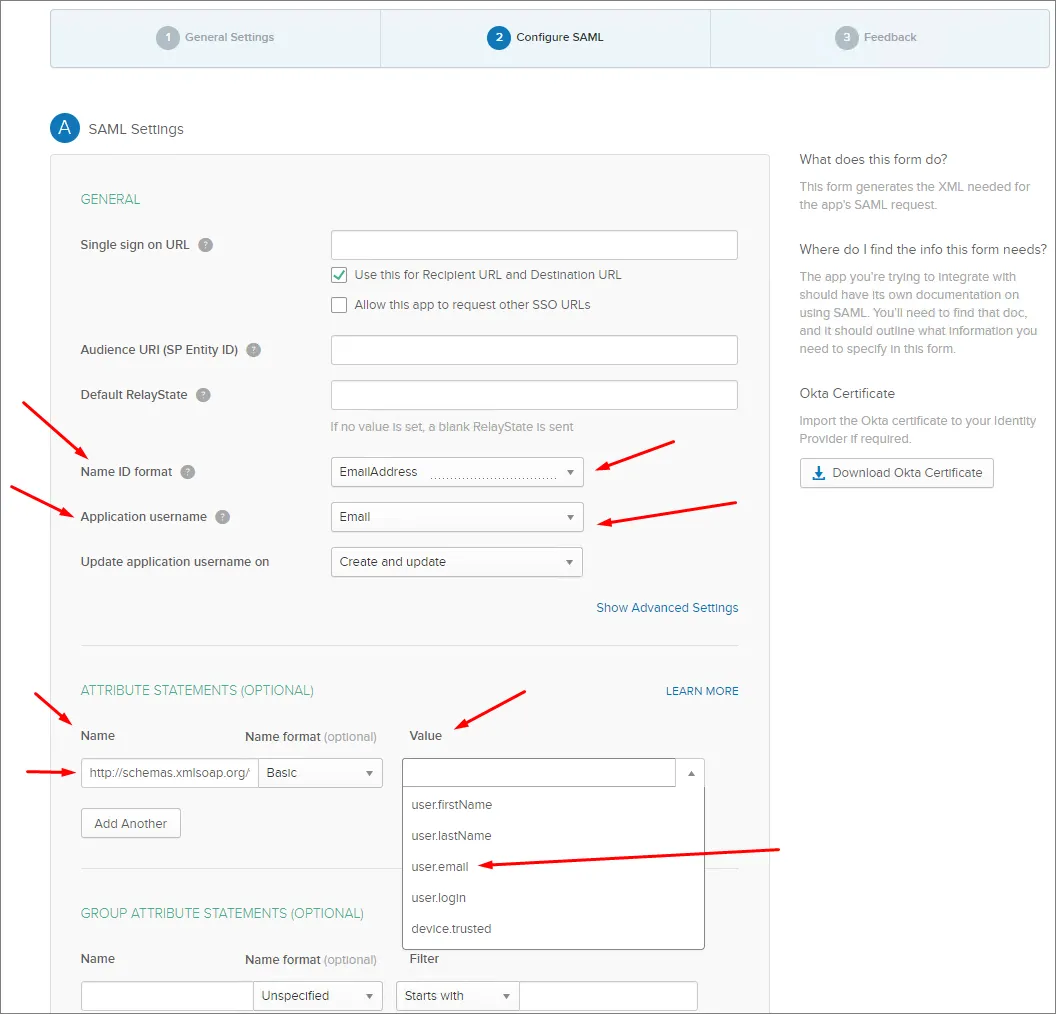
Ustaw pozostałe pola w następujący sposób:
-
Name ID format to EmailAddress.
-
Application username to (Okta) Email.
-
W sekcji ATTRIBUTE STATEMENTS ustaw pole Name na: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress, a Value na: user.email
-
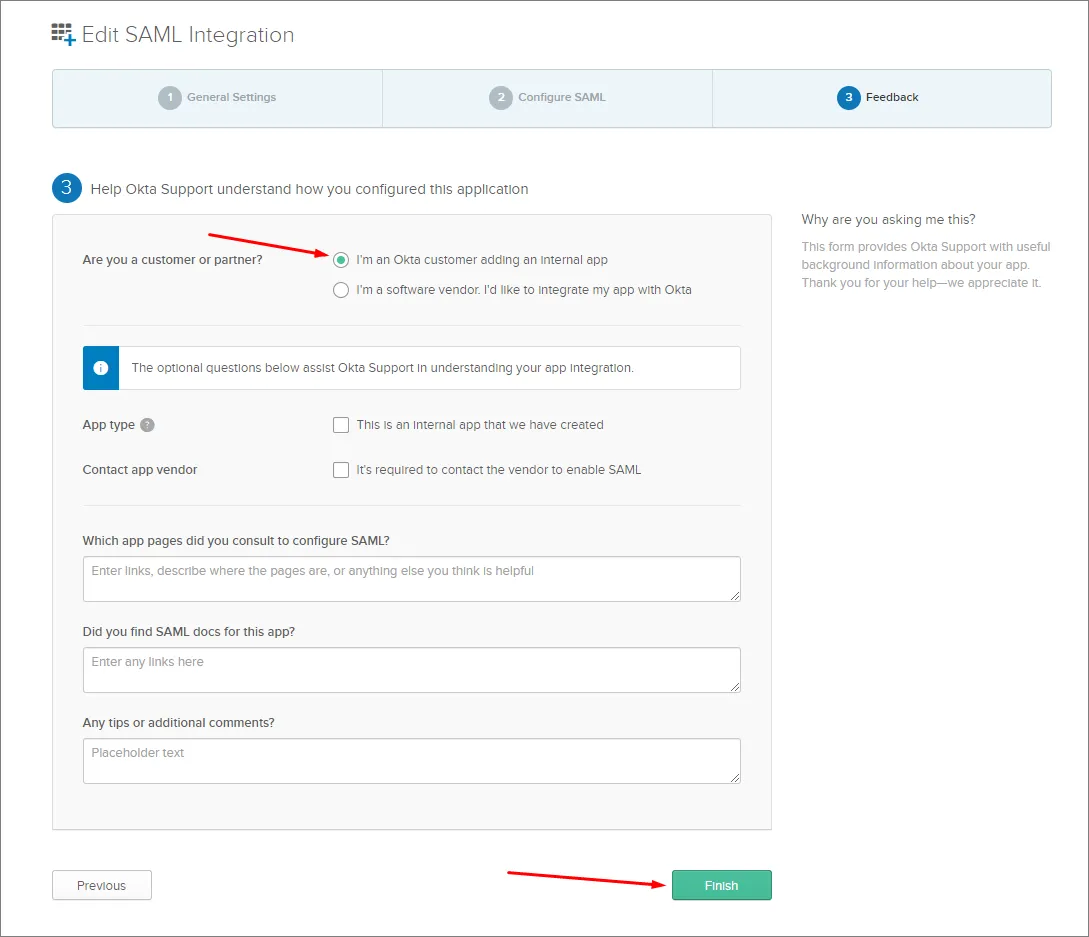
Kliknij przycisk Next i wybierz opcję ..Okta customer adding an internal app.
-
Kliknij przycisk Finish.
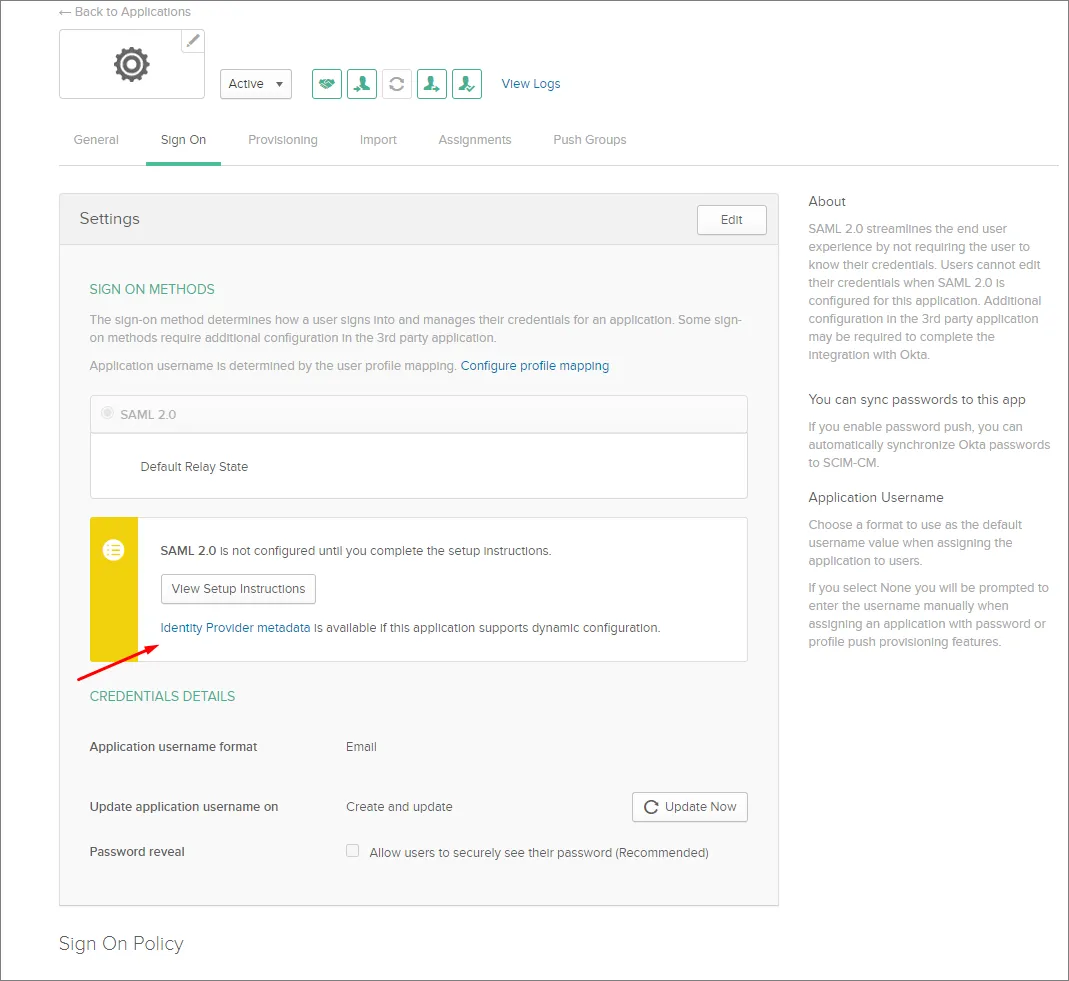
-
Kliknij łącze Identity Provider metadata i zapisz metadane XML na komputerze lub kliknij przycisk View Setup Instructions, aby uzyskać opcje konfiguracji ręcznej.
-
W sekcji SAML Identity Provider configuration na stronie Admin – Settings – Authentication interfejsu przeglądarkowego Enterprise Server prześlij zapisany plik XML metadanych lub skonfiguruj poszczególne sekcje ręcznie – patrz wyżej.
Rozwiń poniższą zwijaną sekcję, aby zobaczyć przykład krok po kroku procesu integracji dla Microsoft Entra ID jako dostawcy tożsamości.
Integration with Microsoft Entra ID
-
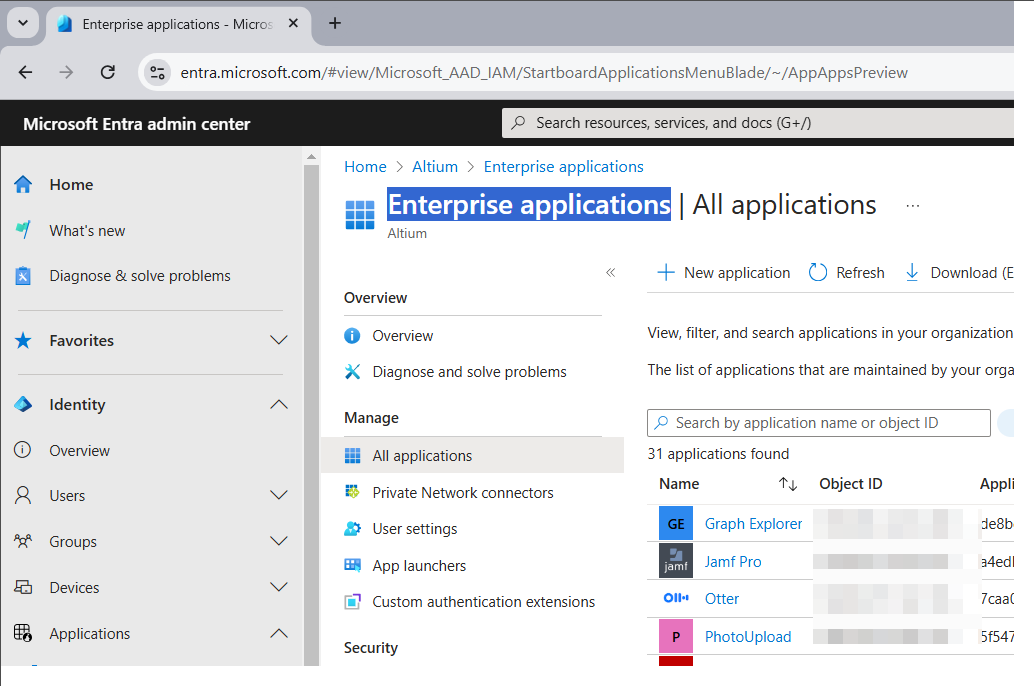
Zaloguj się do Microsoft Entra admin center.
-
Wybierz Identity, a następnie opcję Enterprise applications.
-
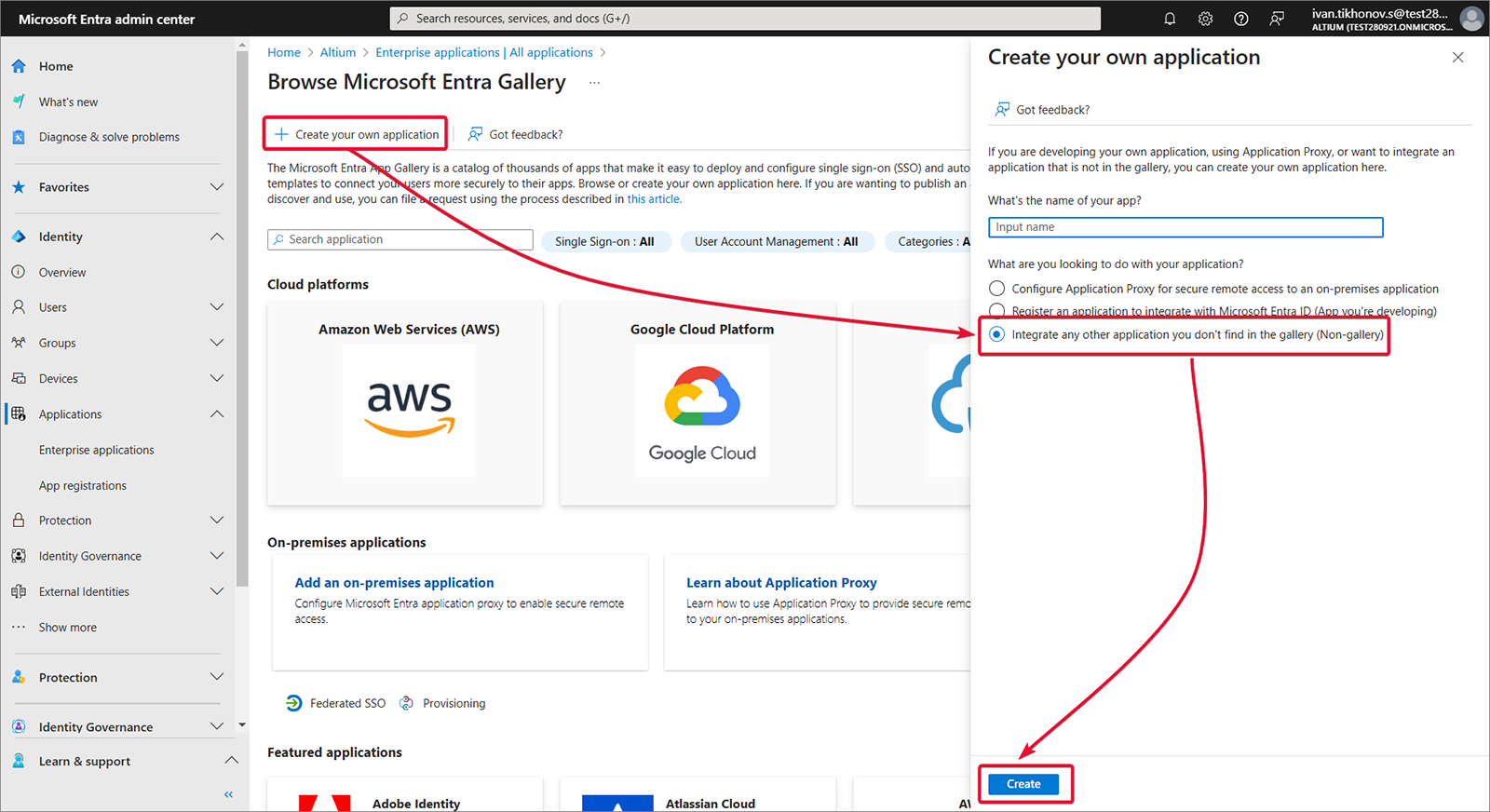
Utwórz własną aplikację.
-
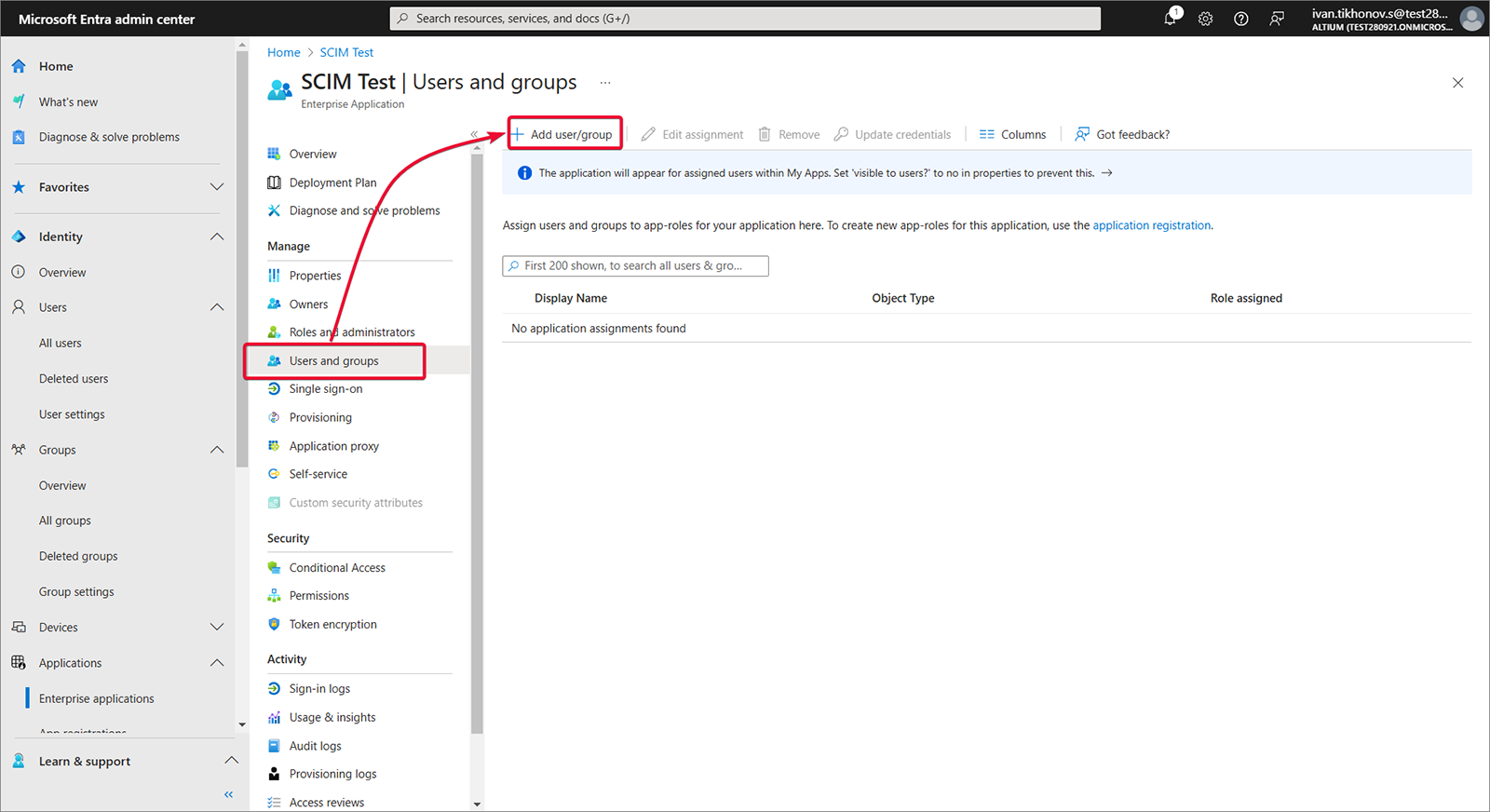
Wybierz Users and groups, a następnie Add user/group.
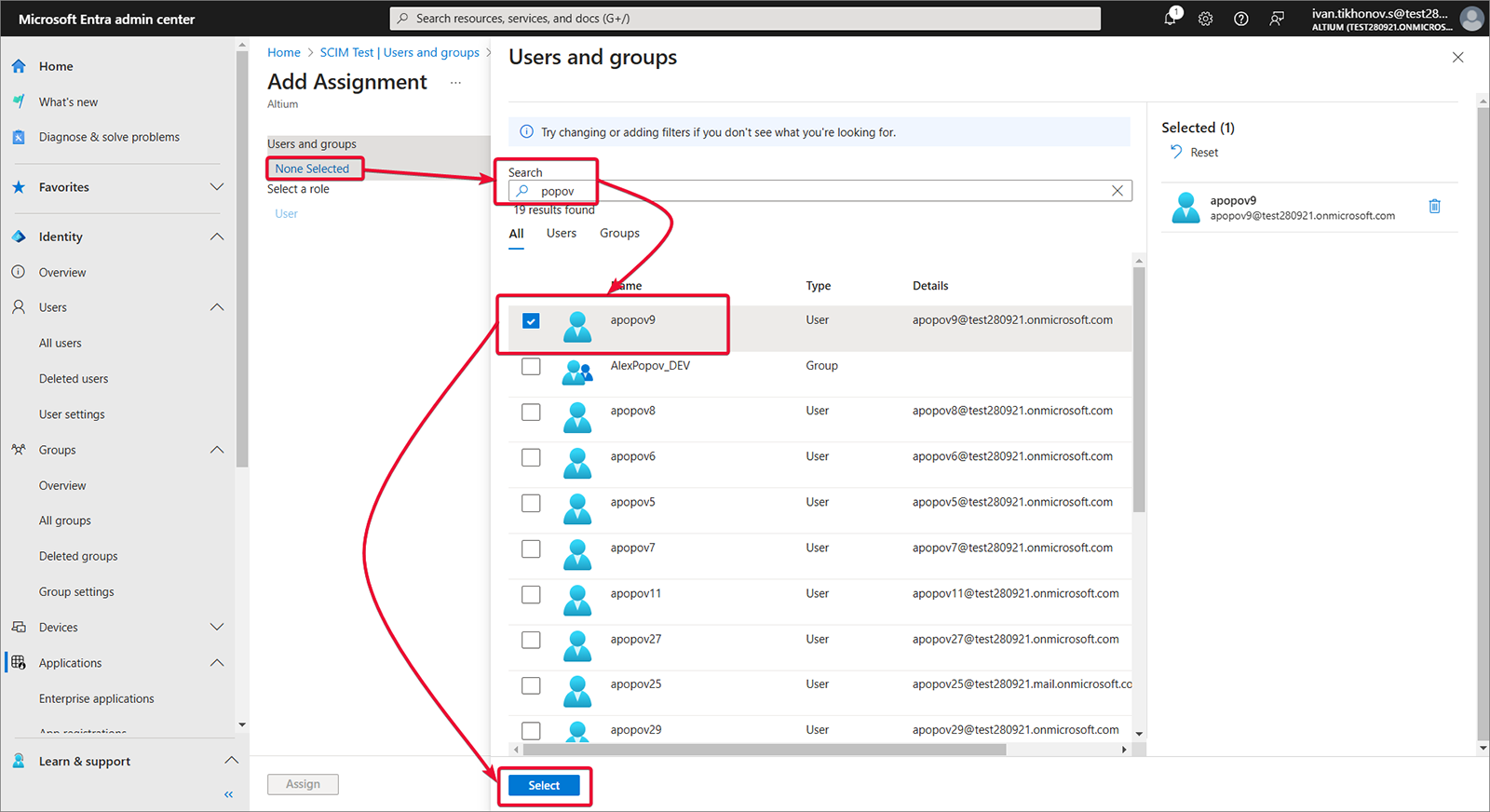
-
Wybierz Single sign-on, Step 1, a następnie Edit.
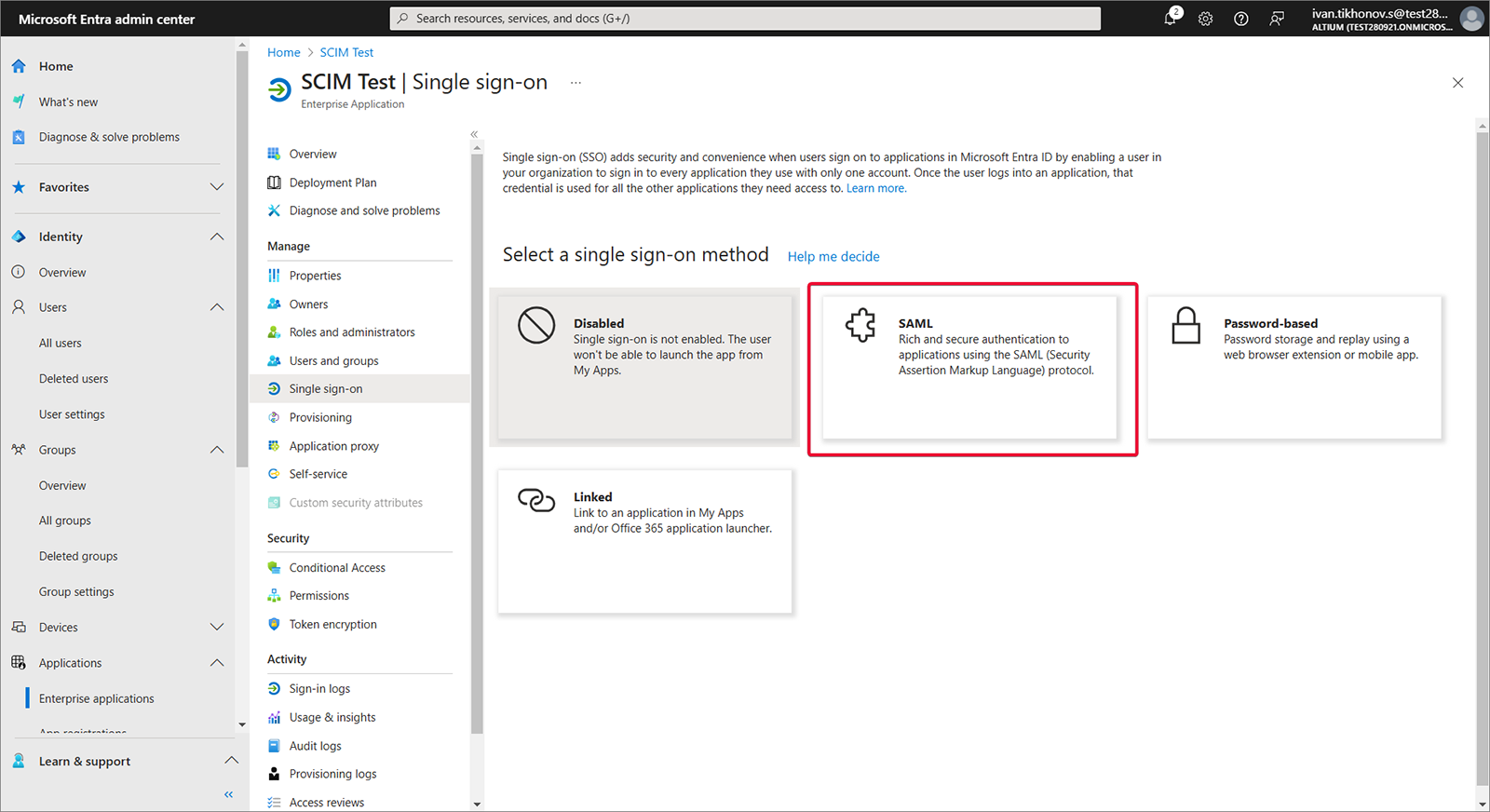
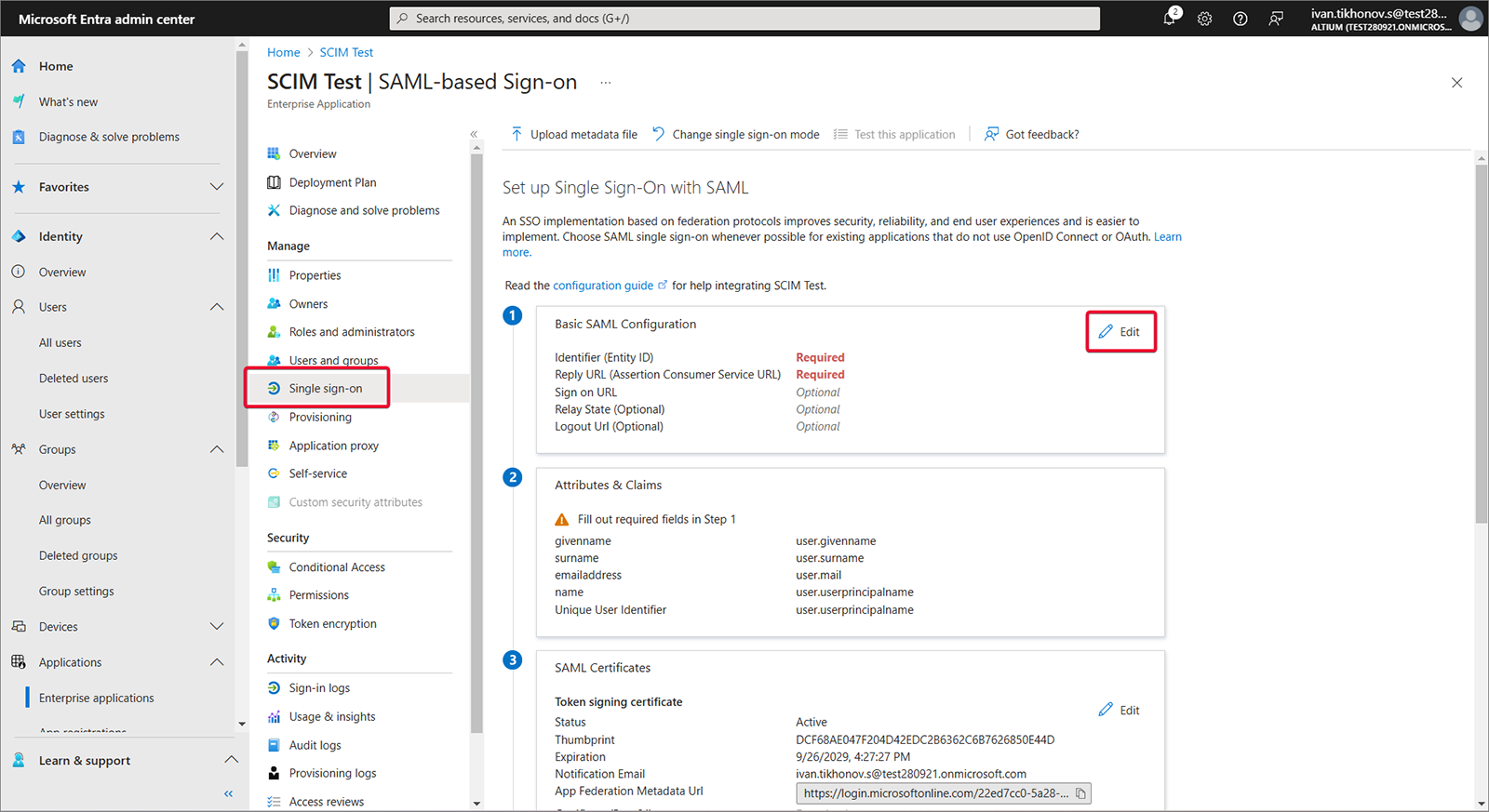
-
Skopiuj ( ) Entity ID oraz Single Sign-On URL ze strony Admin – Settings – Authentication interfejsu przeglądarkowego Enterprise Server. Wklej skopiowane ciągi do pól Entity ID i Assertion Consumer Service URL w obszarze konfiguracji SAML aplikacji Microsoft Entra. Upewnij się, że pola wyboru Default są zaznaczone dla tych pól, a następnie zapisz konfigurację.
) Entity ID oraz Single Sign-On URL ze strony Admin – Settings – Authentication interfejsu przeglądarkowego Enterprise Server. Wklej skopiowane ciągi do pól Entity ID i Assertion Consumer Service URL w obszarze konfiguracji SAML aplikacji Microsoft Entra. Upewnij się, że pola wyboru Default są zaznaczone dla tych pól, a następnie zapisz konfigurację.

-
Pobierz utworzony plik Federation Metadata XML.
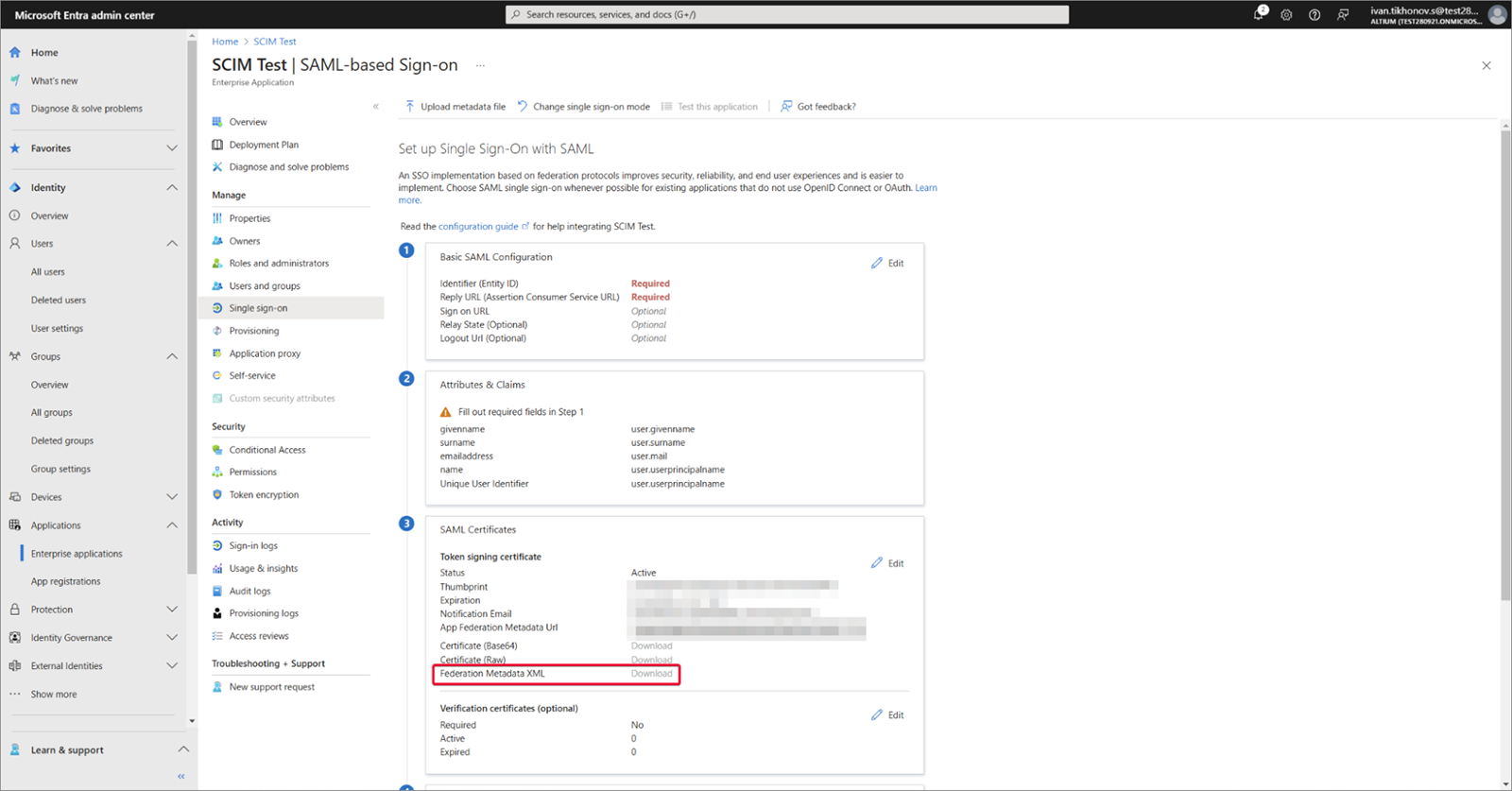
-
Prześlij plik Federation Metadata XML na stronę Admin – Settings – Authentication interfejsu przeglądarkowego Enterprise Server, a następnie przetestuj połączenie integracji SAML – patrz wyżej.
Rozwiń poniższą zwijaną sekcję, aby zobaczyć przykład krok po kroku procesu integracji dla JumpCloud jako dostawcy tożsamości.
Integration with JumpCloud
-
W interfejsie JumpCloud wybierz SSO z drzewa nawigacji, a następnie przycisk Add New Application na stronie SSO.
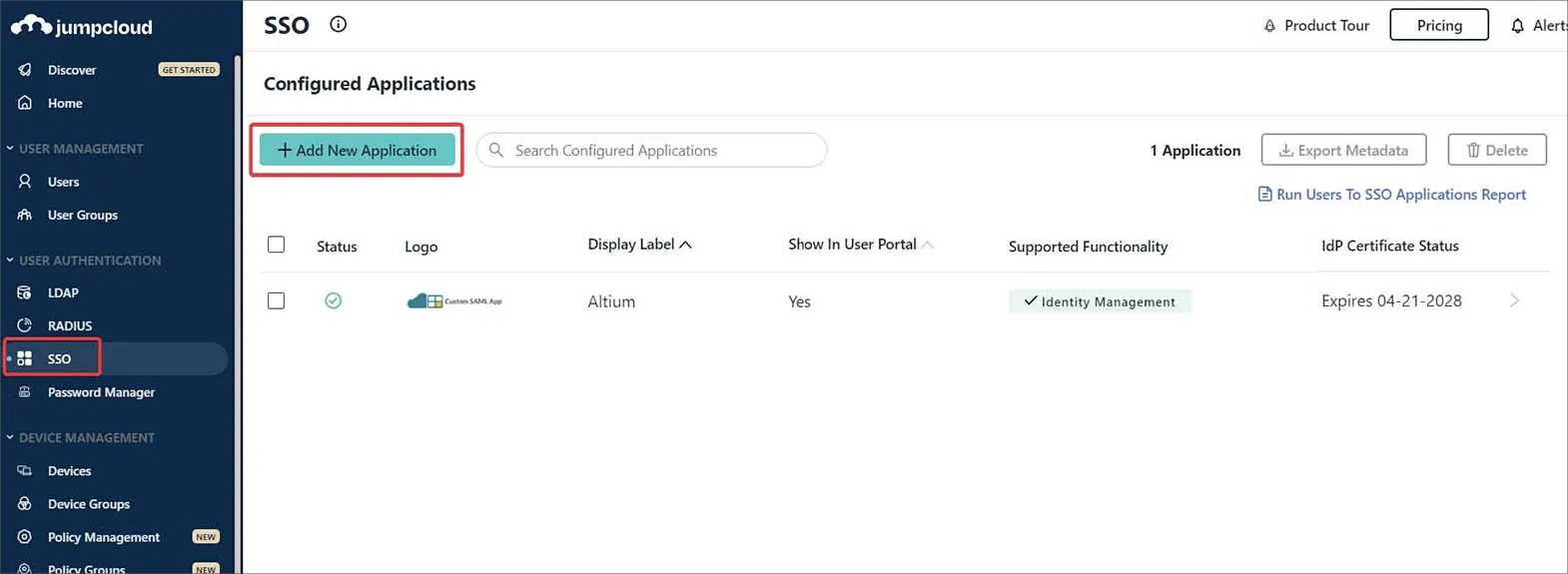
-
Wpisz „saml” w polu Search w oknie konfiguracji, aby zlokalizować, a następnie zainstalować Custom SAML App.
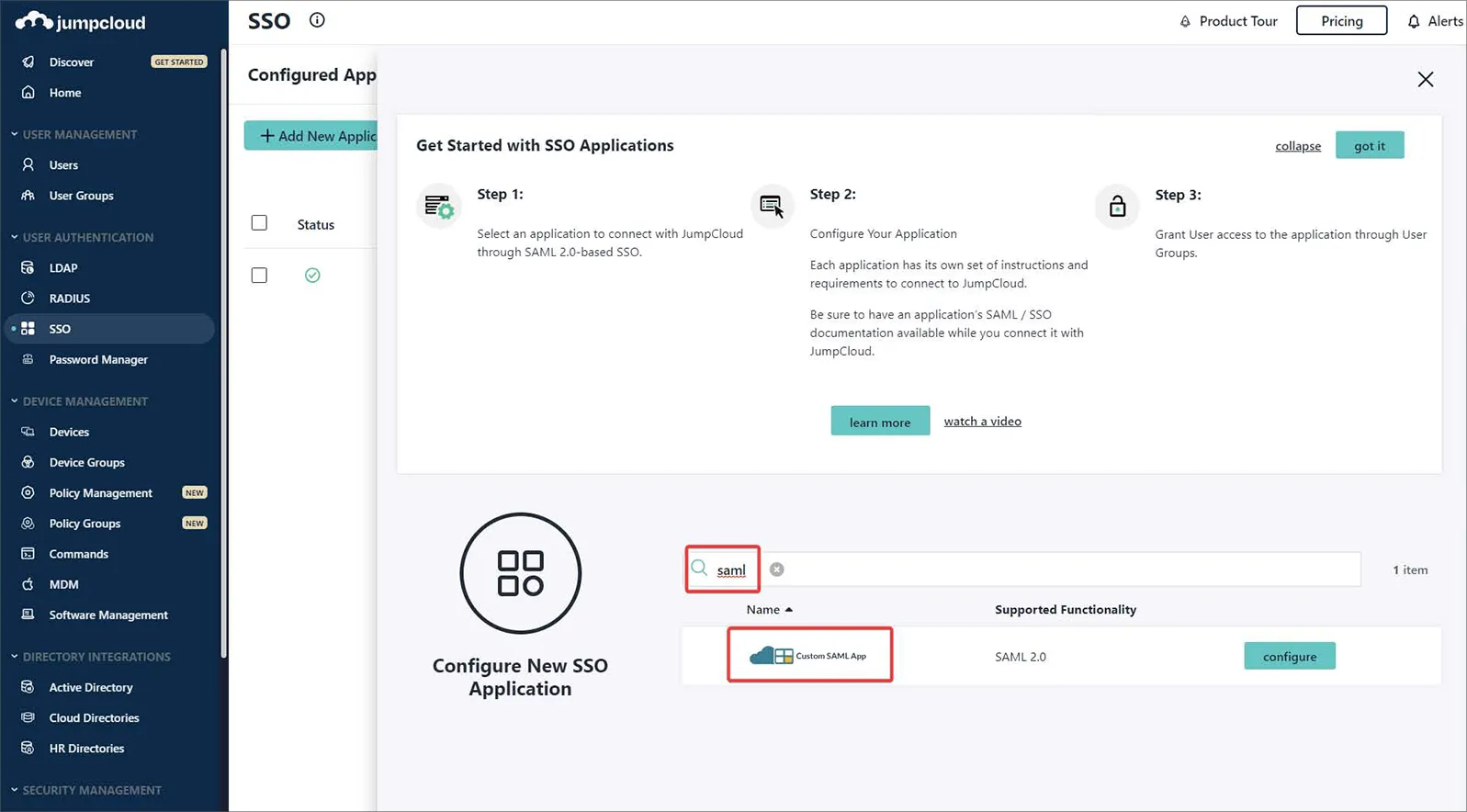
-
Nazwij swoją instancję Custom SAML App – w tym przykładzie etykieta to Altium.
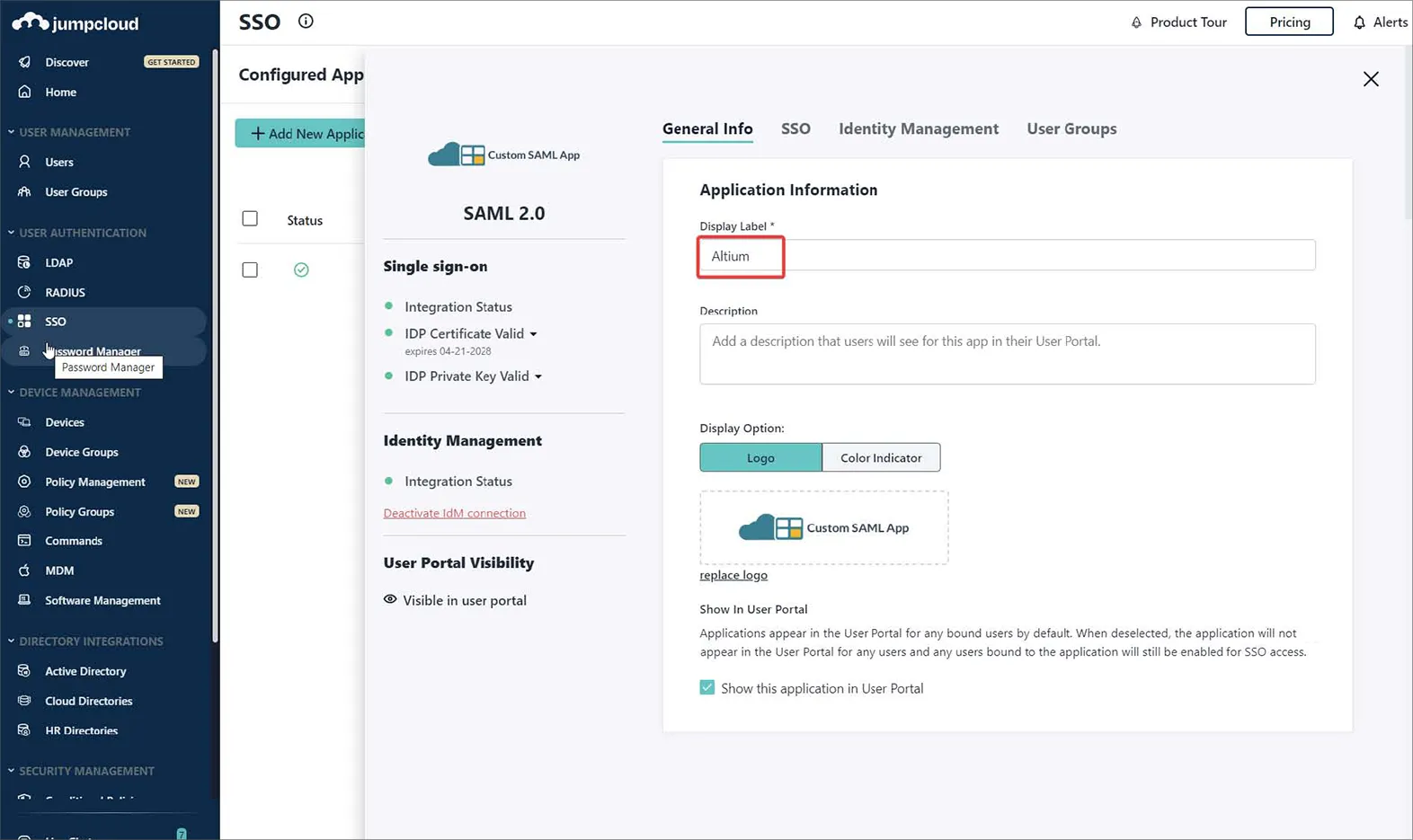
-
Przejdź do karty SSO w interfejsie konfiguracji JumpCloud i wprowadź ustawienia Entity/URL ze strony Admin – Settings – Authentication interfejsu przeglądarkowego Enterprise Server, jak pokazano.

-
Wprowadź punkt końcowy JumpCloud IDP URL i włącz opcję Declare Redirect Endpoint.
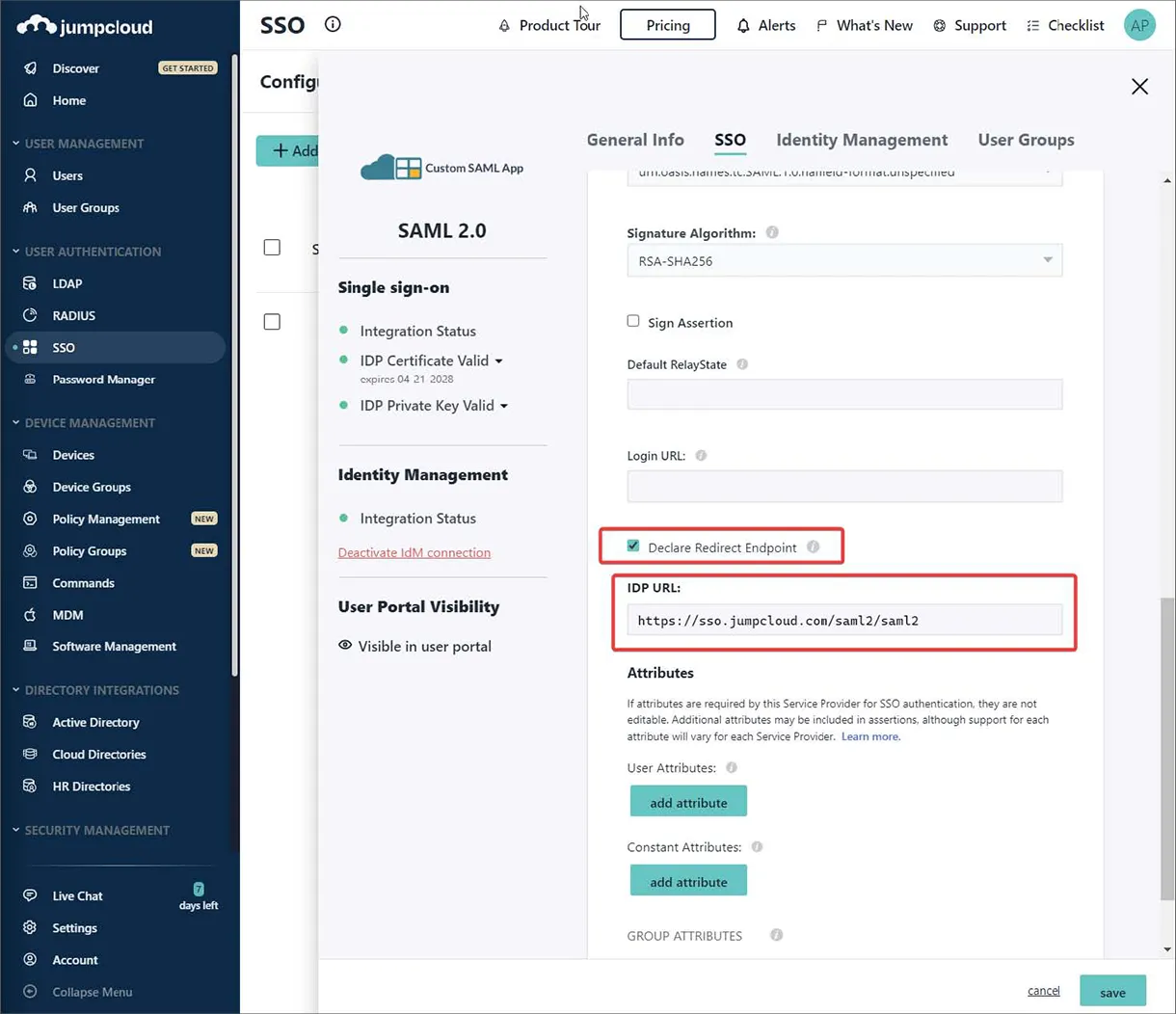
-
Użyj opcji Export Metadata, aby pobrać wynikowy plik XML metadanych SAML.
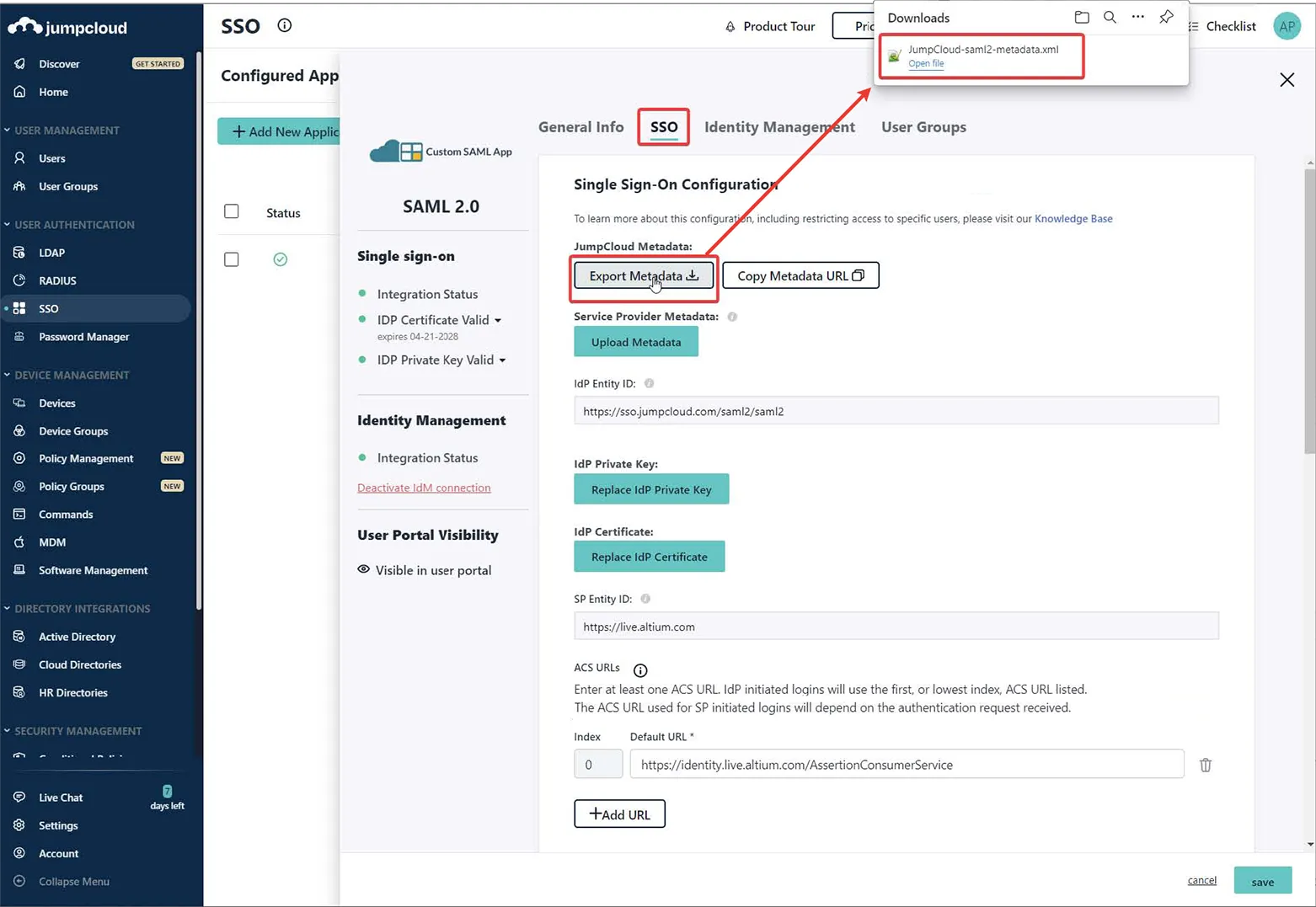
-
Prześlij plik XML metadanych na stronę Admin – Settings – Authentication w interfejsie przeglądarkowym Enterprise Server, a następnie przetestuj połączenie integracji SAML – patrz wyżej.
Rozwiń poniższą sekcję zwijaną, aby zobaczyć przykład krok po kroku procesu integracji dla Microsoft Administrative Domain Federated Services (AD FS) jako dostawcy tożsamości.
Integration with Microsoft AD FS
Musisz mieć dostęp administracyjny do instancji AD FS.
-
Otwórz aplikację AD FS Management (zwykle Start → Windows Administrative Tools → AD FS Management).
-
Przejdź do Relying Party Trusts i kliknij opcję Add Relying Party Trust... (1).
-
W oknie podręcznym upewnij się, że wybrano Claims aware (2), i kliknij Start (3).
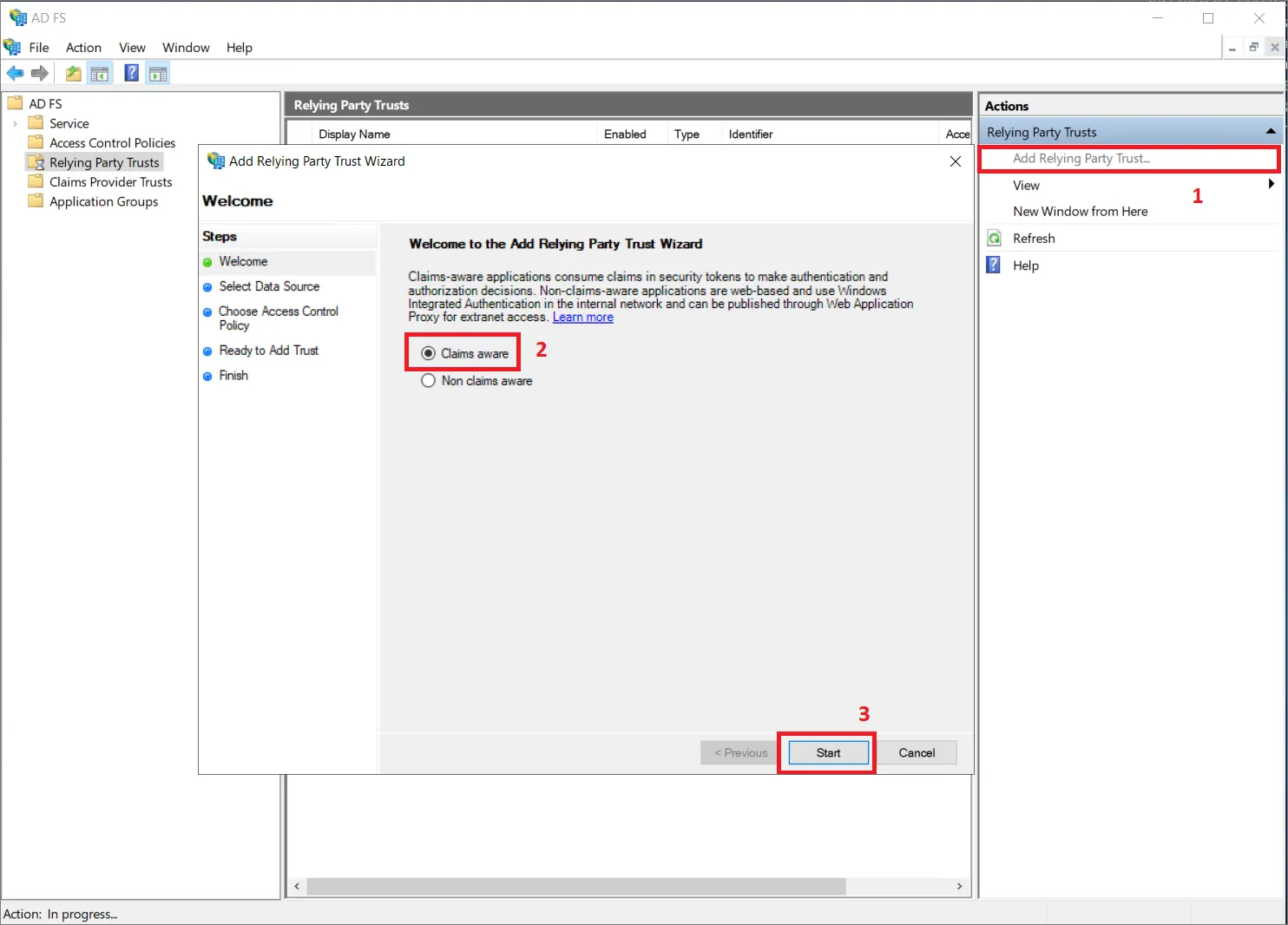
-
W kroku Select Data Source wybierz Enter data about the relying party manually (1) i kliknij Next (2).
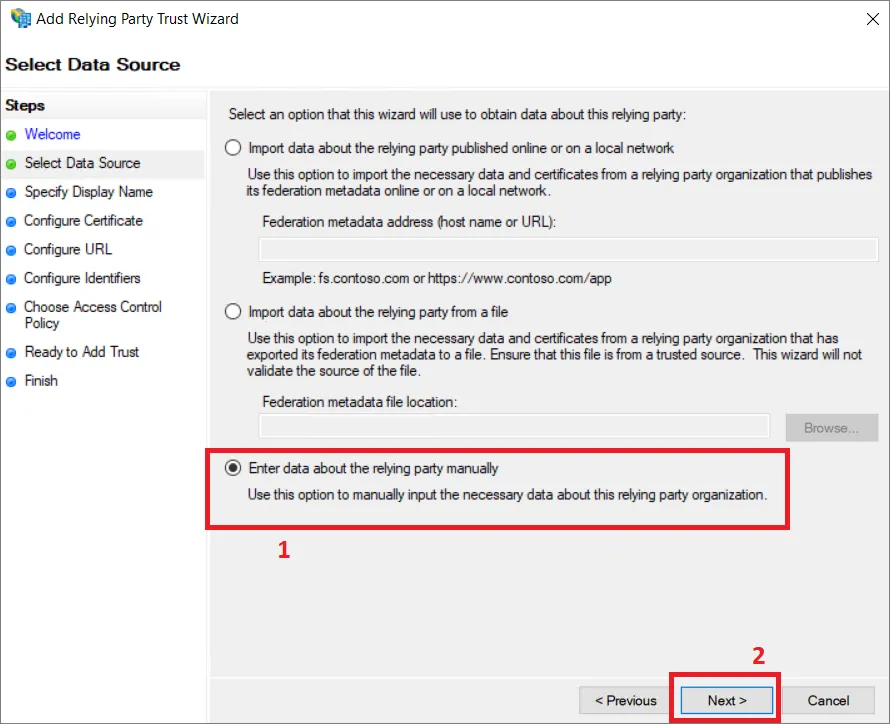
-
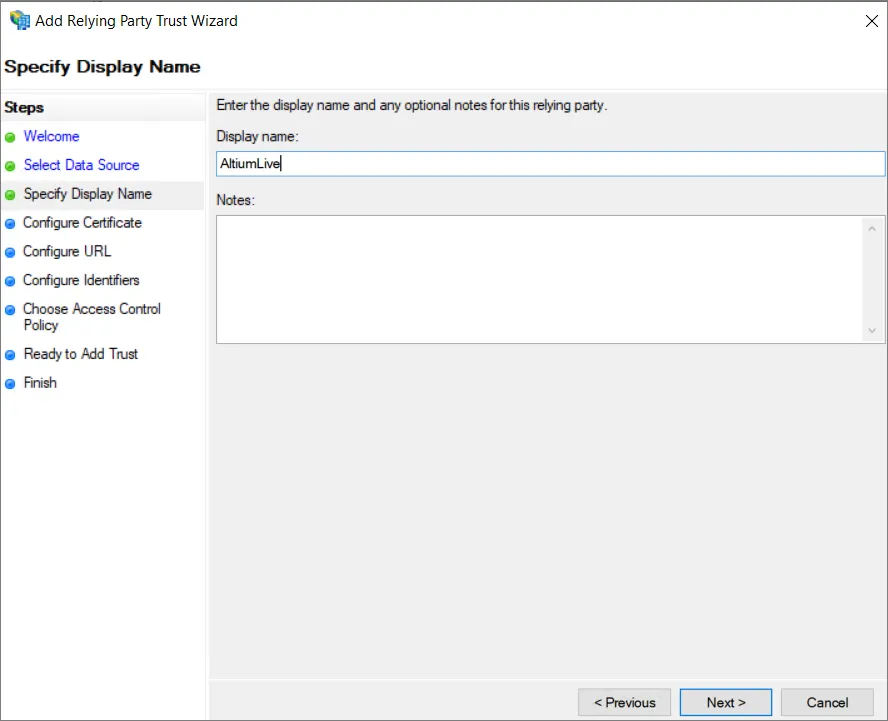
Podaj nazwę wyświetlaną dla relacji zaufania. W tym przykładzie jako nazwę wyświetlaną użyto AltiumLive.
-
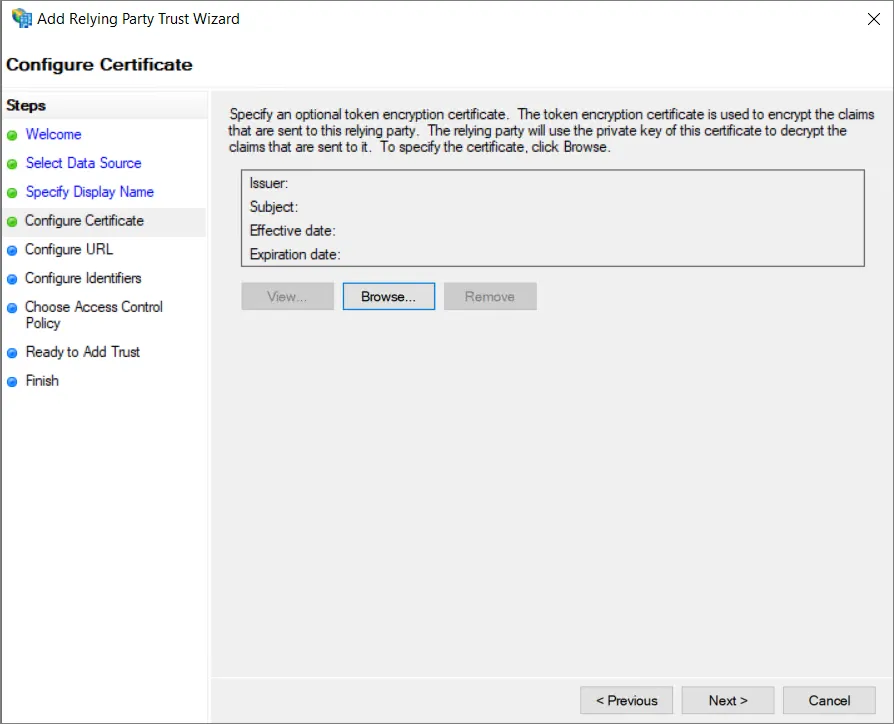
W zależności od konfiguracji zabezpieczeń możesz wskazać opcjonalny certyfikat szyfrowania tokenu. Na potrzeby tego przewodnika nie będziemy go używać.
-
W kroku Configure URL upewnij się, że wybrano opcję Enable support for the SAML 2.0 WebSSO protocol (1), i wprowadź Single Sign-On URL skopiowane ze strony Admin – Settings – Authentication w interfejsie przeglądarkowym Enterprise Server do pola Relying party SAML 2.0 SSO service URL: (2). Kliknij Next (3).

-
W kroku Configure Identifiers podaj identyfikator dla tej relacji zaufania w polu wejściowym (1). Identyfikator musi zostać pobrany z wpisu Entity ID znajdującego się w obszarze Altium Metadata Configuration na stronie Admin – Settings – Authentication w interfejsie przeglądarkowym Enterprise Server. Upewnij się, że klikniesz przycisk Add (2).

Wynik powinien wyglądać jak poniżej. Kliknij Next.

-
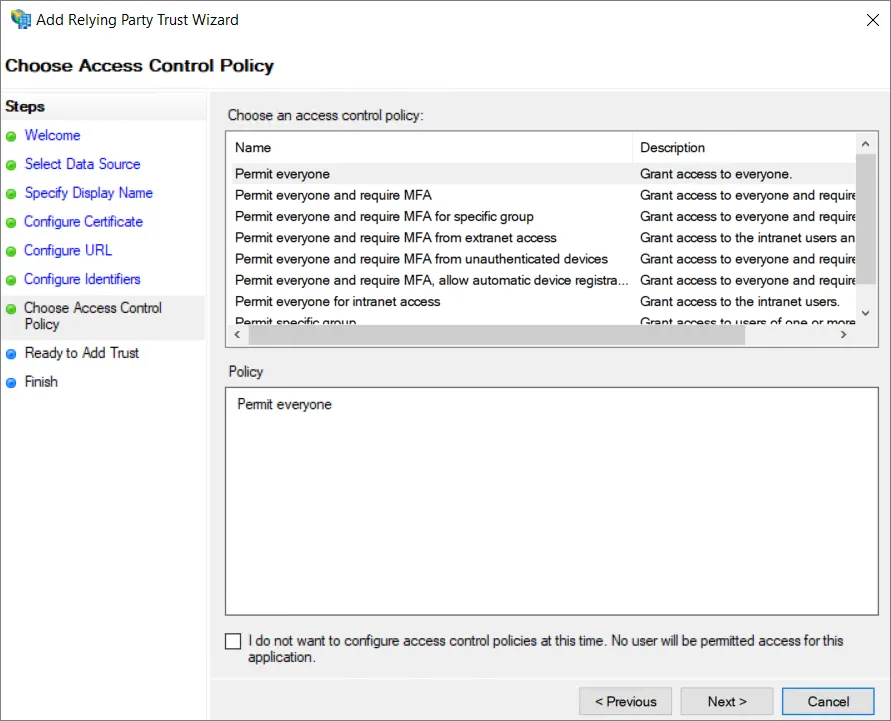
W zależności od konfiguracji zabezpieczeń w następnym kroku możesz wybrać opcjonalne zasady kontroli dostępu. W tym przykładzie nie wybierzemy żadnych dodatkowych zasad i przejdziemy dalej, wybierając opcję Permit everyone.
-
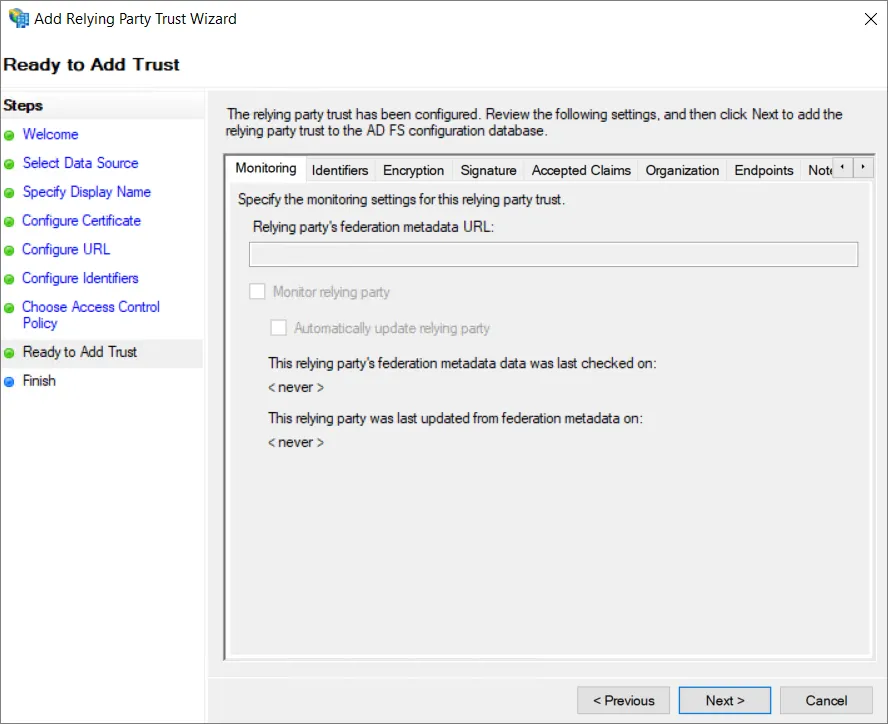
Sprawdź konfigurację i wybierz Next.
-
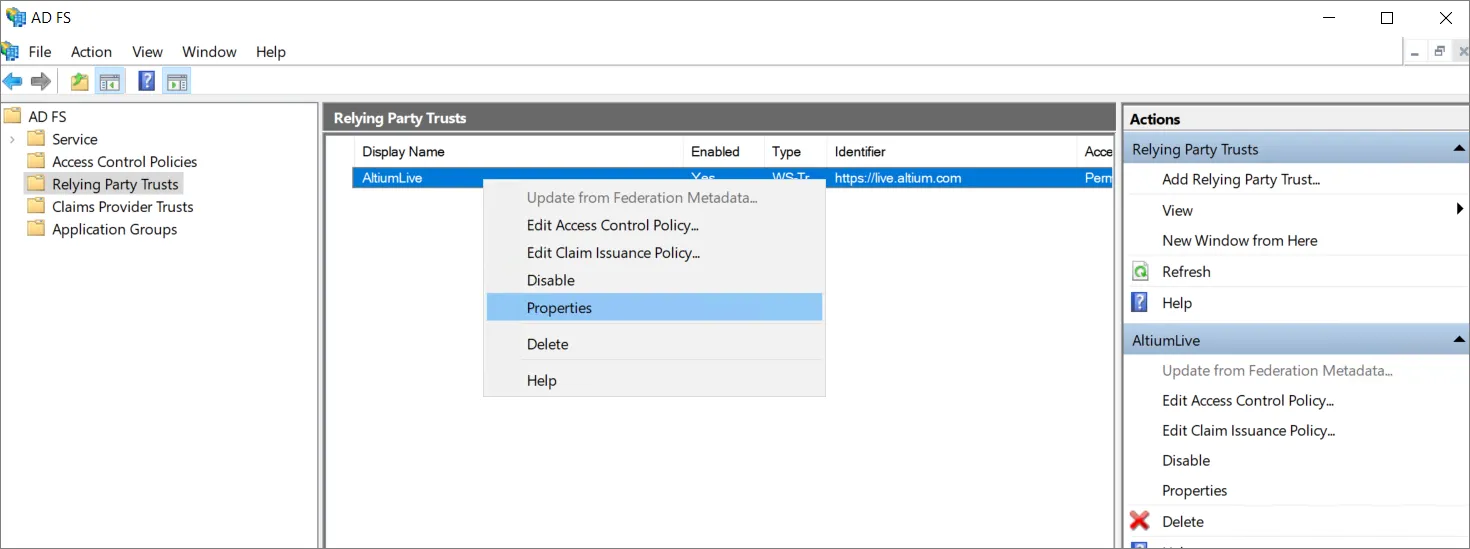
Nie wszystkie ustawienia są dostępne podczas konfigurowania relacji zaufania. Aby umożliwić użycie SHA-1 jako bezpiecznego algorytmu skrótu, kliknij prawym przyciskiem myszy nazwę Relying Party Trust, którą właśnie dodałeś(-aś), i wybierz Properties.
-
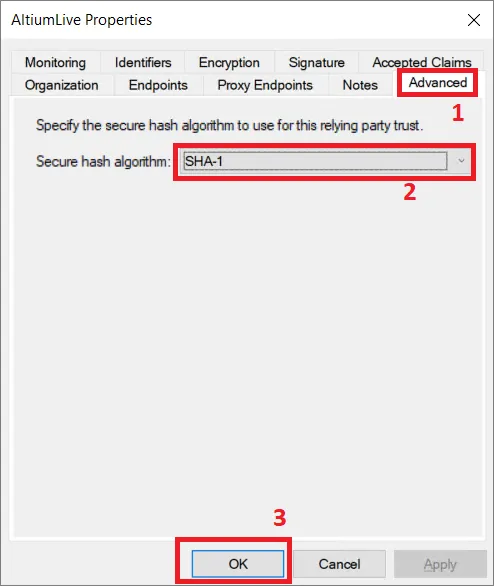
W oknie właściwości wybierz kartę Advanced (1) i ustaw SHA-1 jako bezpieczny algorytm skrótu (2). Kliknij OK, aby zapisać zmiany.
-
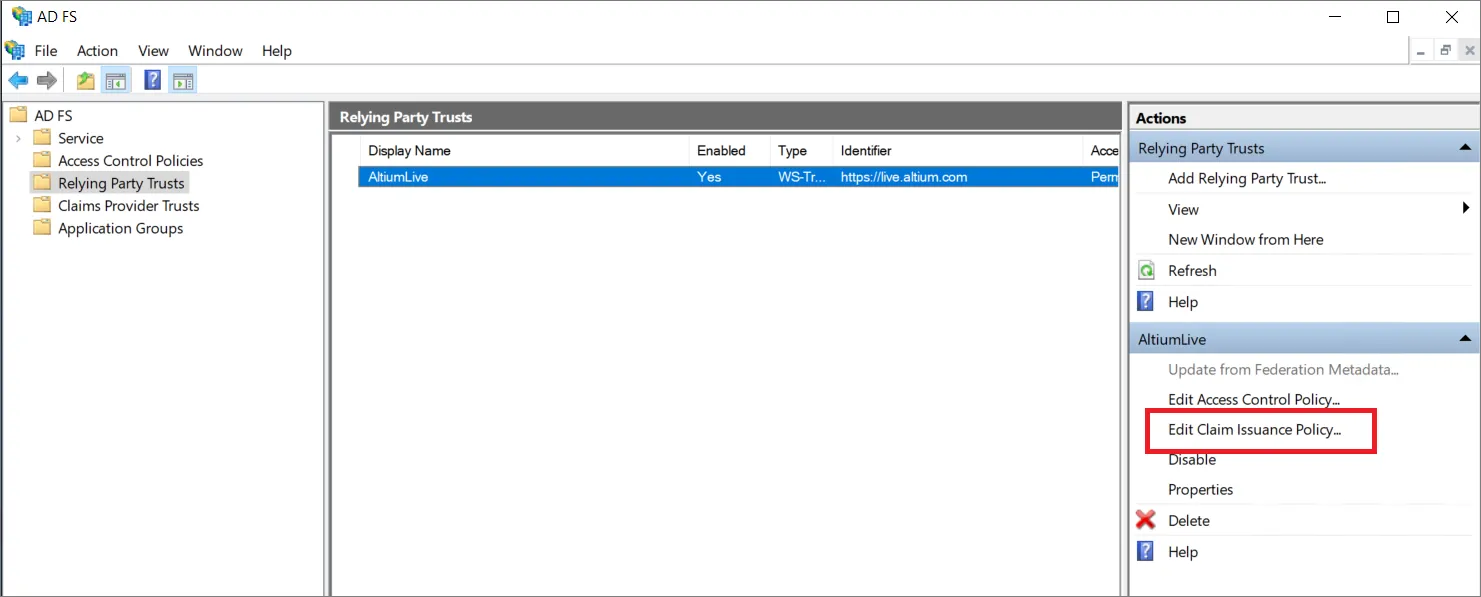
Po powrocie do okna AD FS Management wybierz dodaną relację zaufania strony ufającej (Relaying Party Trust) i wybierz opcję Edit Claim Issuance Policy....
-
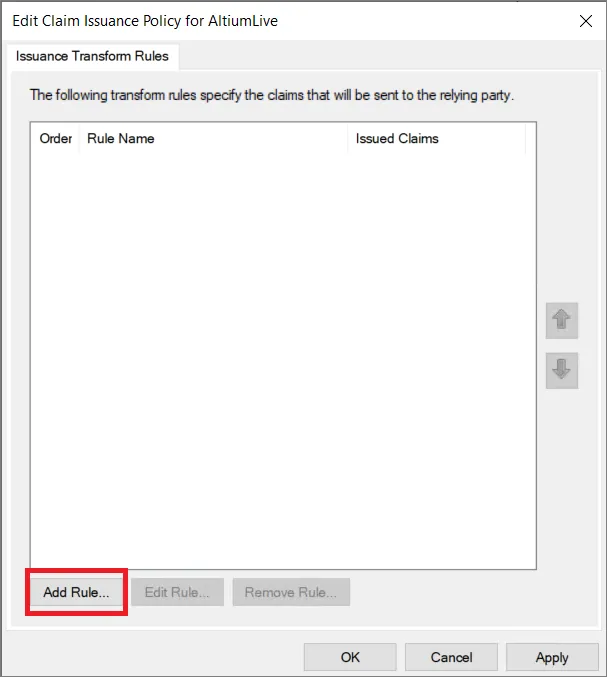
W oknie Edit Claim Issuance Policy wybierz Add Rule...
-
W kroku Choose Rule Type kreatora upewnij się, że wybrano Send LDAP Attributes as Claims, a następnie kliknij Next.
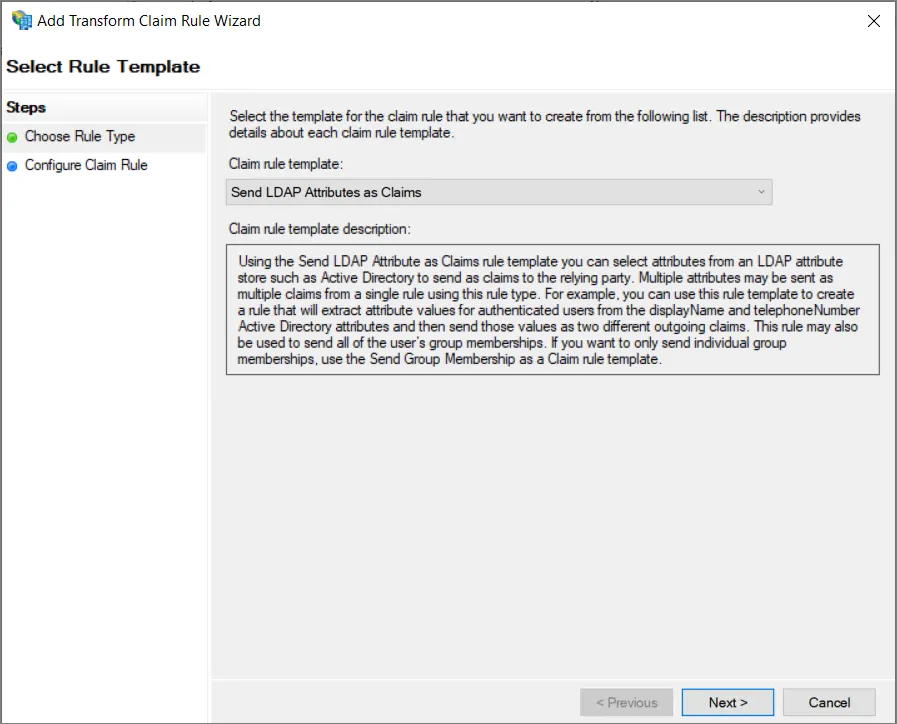
-
Podaj Claim rule name (1), wybierz Active Directory jako Attribute store (2) oraz wybierz LDAP Attribute (3) z identyfikatora (ID), który zawiera nazwę użytkownika dla użytkownika Enterprise Server. Ten atrybut musi zostać zmapowany na Name ID w Outgoing Claim Type (3). Kliknij Finish (4).
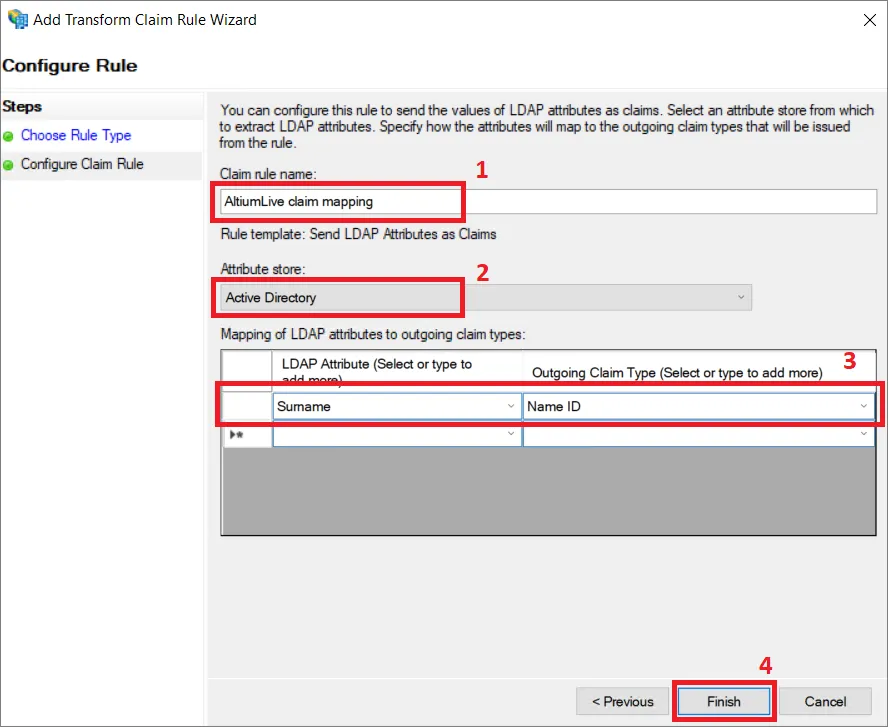
Important Note: W tym przykładzie zmapowaliśmy Surname lub Last name, aby zawierały wymaganą wartość. Twoja konfiguracja może się różnić.
-
Upewnij się, że zasada wydawania oświadczeń (claim issuance policy) została zapisana, klikając OK.
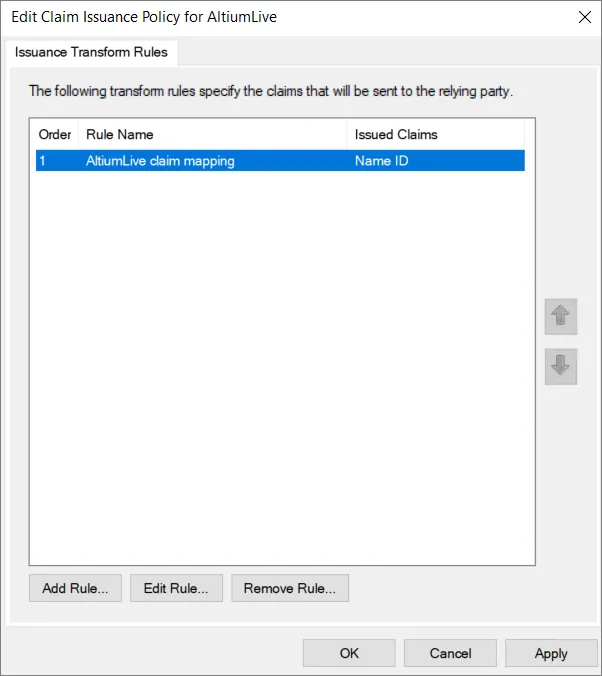
-
Pobierz plik FederationMetadata.xml z odpowiedniego serwera.
-
Prześlij plik XML metadanych na stronę Admin – Settings – Authentication w interfejsie przeglądarkowym Enterprise Server, a następnie przetestuj połączenie integracji SAML – patrz wyżej.
Rozwiń poniższą sekcję zwijaną, aby zobaczyć przykład krok po kroku procesu integracji dla AWS IAM Identity Center jako dostawcy tożsamości:
Integration with AWS IAM Identity Center
-
Przejdź do IAM Identity Center i dodaj niestandardową aplikację SAML 2.0 (Add Application).
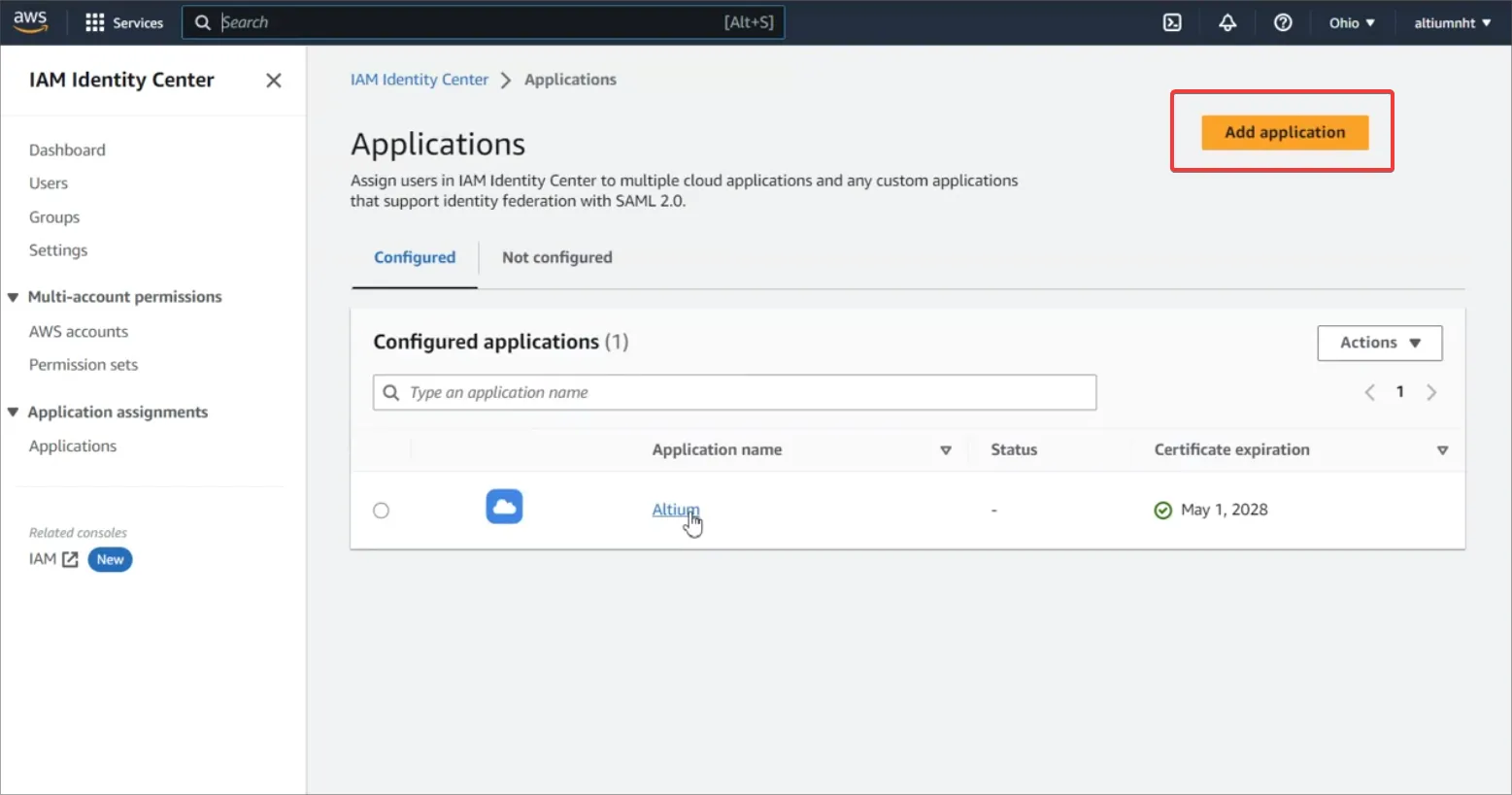
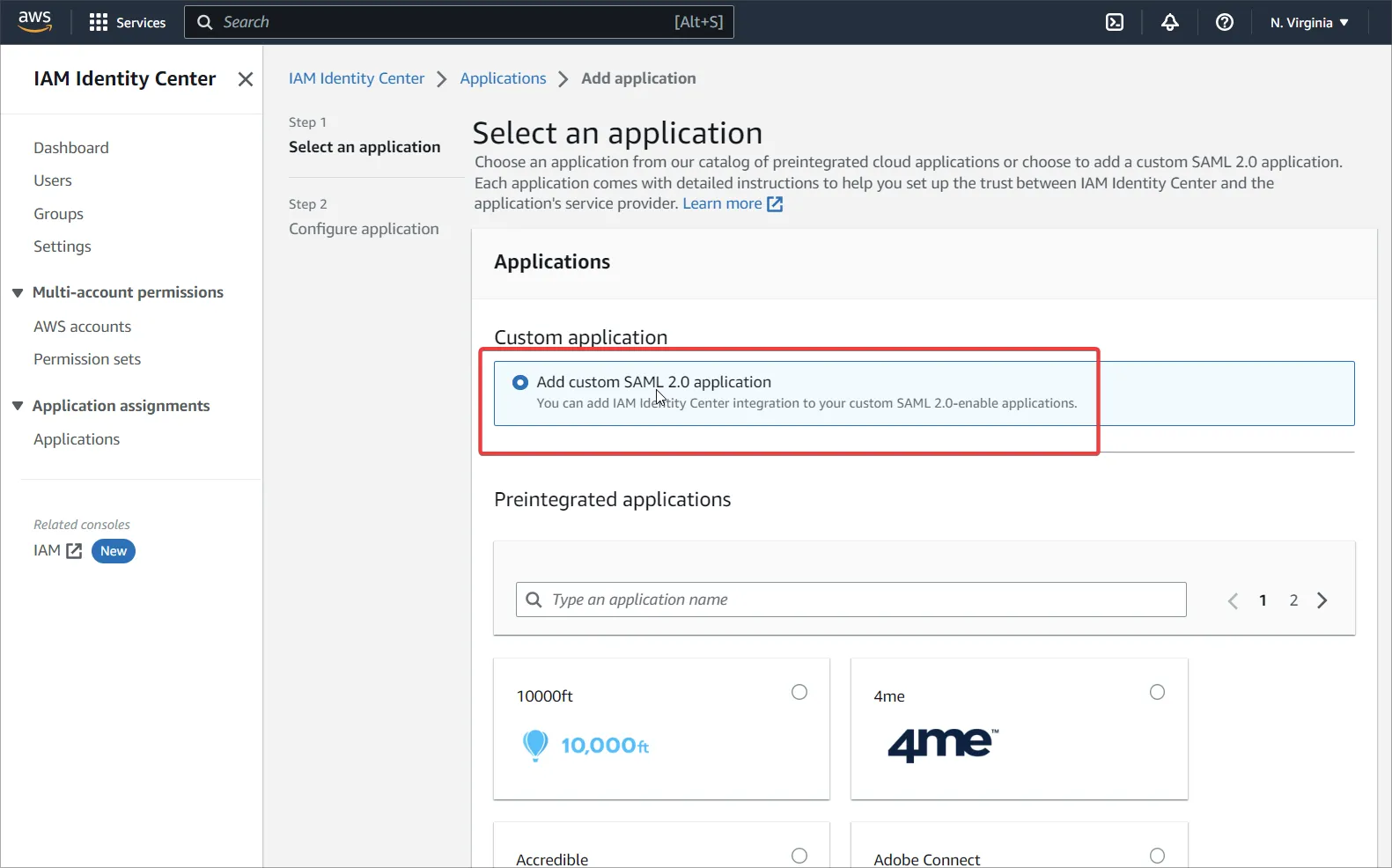
-
Uzupełnij ustawienia adresu URL metadanych AWS na podstawie danych z Twojej strony Altium SSO. Potwierdź ustawienia przyciskiem Submit.

-
Pobierz plik metadanych z obszaru IAM Identity Center metadata.
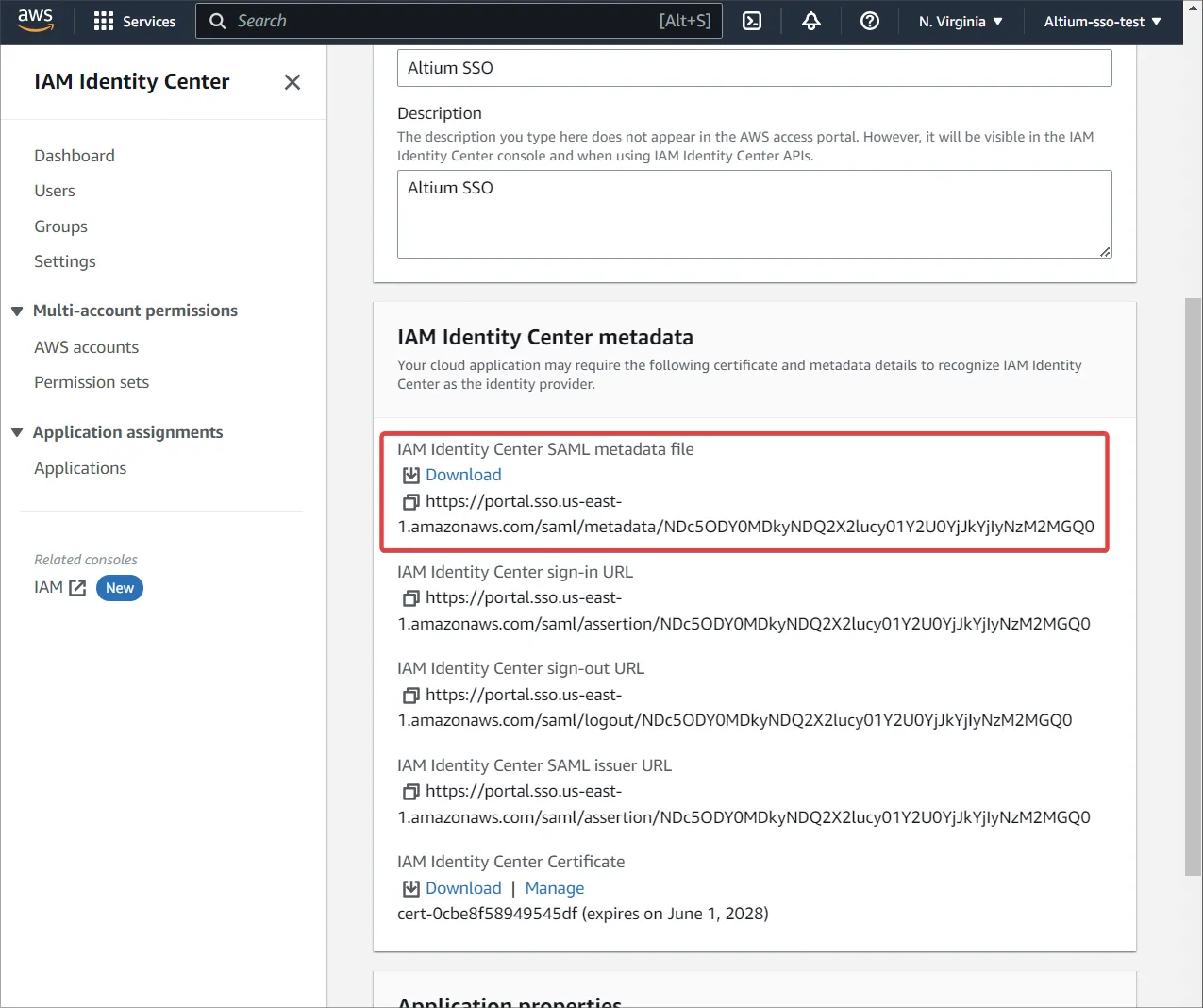
-
Przejdź do Edit attribute mappings.
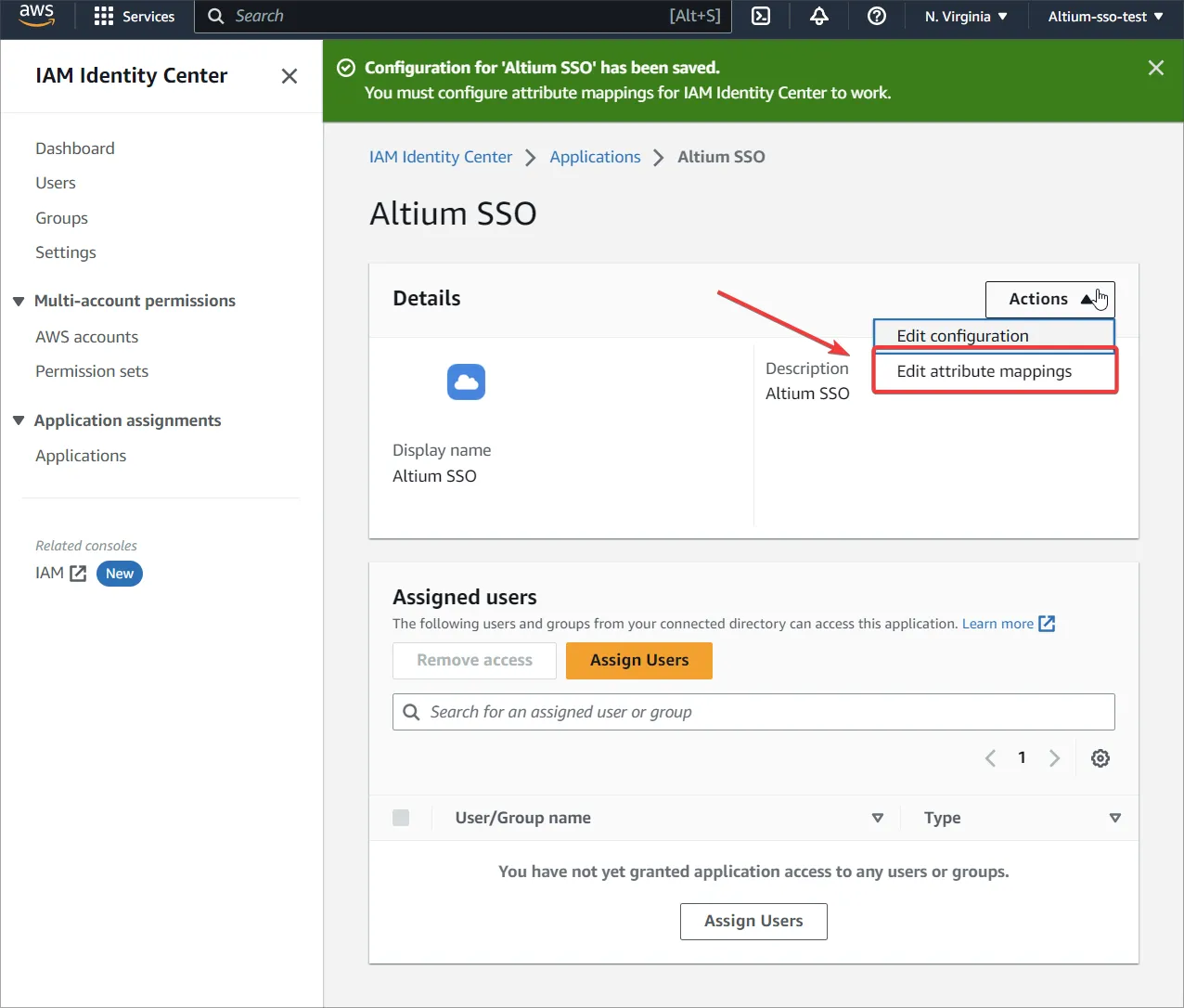
-
Podaj atrybut, który będzie zawierał nazwę użytkownika dla użytkownika Enterprise Server, i wybierz unspecified dla Format.
-
Utwórz nowych użytkowników w AWS i przypisz aplikację do utworzonych użytkowników lub do grupy.
-
Upewnij się, że ci sami użytkownicy istnieją zarówno po stronie Altium, jak i IAM.
-
Prześlij plik XML metadanych na stronę Admin – Settings – Authentication w interfejsie przeglądarkowym Enterprise Server, a następnie przetestuj połączenie integracji SAML – patrz wyżej.
Logowanie jednokrotne OAuth / OIDC
Funkcję SSO dla Twojego Enterprise Server można również skonfigurować przy użyciu standardu OAuth / OIDC. Gdy w menu rozwijanym SSO na stronie Admin – Settings – Authentication interfejsu przeglądarkowego zostanie wybrana opcja OAuth / OIDC, strona umożliwia wprowadzenie danych dostarczonych przez wybranego dostawcę tożsamości (IdP).

SSO nie jest włączone, dopóki nie zostanie uruchomiony test integracji, wywoływany przyciskiem  . Weryfikuje to proces tożsamości SSO oraz logowanie SSO w Twojej firmie. Po pomyślnym przetestowaniu konfiguracji możesz zapisać ustawienia, klikając przycisk
. Weryfikuje to proces tożsamości SSO oraz logowanie SSO w Twojej firmie. Po pomyślnym przetestowaniu konfiguracji możesz zapisać ustawienia, klikając przycisk  (
( ), co skutecznie zastosuje je w Enterprise Server.
), co skutecznie zastosuje je w Enterprise Server.
Jeśli SSO zostanie później wyłączone, ręcznie lub w odpowiedzi na zmianę konfiguracji, dostępny stanie się przycisk  , aby można było powtórzyć proces testowania.
, aby można było powtórzyć proces testowania.
Podczas korzystania z Entra ID pamiętaj, że udostępnia ono dwie wersje API dla punktów końcowych OAuth:
Musisz pobrać właściwy zestaw punktów końcowych (token/authorize/userinfo) z jednego z tych wariantów. Mieszanie ich spowoduje błąd podczas próby nawiązania połączenia z Entra ID z poziomu Enterprise Server.