Enterprise Server の管理者は、サーバー向けの シングルサインオン(SSO)機能を設定して有効化できます。バックエンドの設定システムにより、管理者はサーバーユーザー向けに SSO 機能の確立、テスト、有効化、無効化を行えます。SSO オプションは、Enterprise Server のブラウザーインターフェースへのサインイン時に利用できます。サーバーユーザー向けに設定すると、SSO により、社内全体のシステムで使用しているのと同じ資格情報セットでサーバーにアクセスできる利便性が得られます。

-
SSO の使用が強制されている場合(ブラウザーインターフェースの Admin – Settings – Authentication ページで Enforce SSO (not applied to access from localhost) オプションが有効になっている場合)、ユーザーは Enterprise Server のアドレスにアクセスした直後に SSO サインインページが表示されます。
-
SSO アクセスは、Altium Designer から Enterprise Server Workspace に接続する際にも使用できます。詳細は Accessing Your Workspace ページを参照してください。
Enterprise Server のブラウザーインターフェースへのアクセス方法の詳細は、Exploring the Browser-based Interface ページを参照してください。
内部の Identity Provider を使用する場合、Enterprise Server はその Identity Provider が使用する HTTPS 証明書を信頼している必要があります。そうでない場合、Enterprise Server からその Identity Provider への接続を確立しようとするとエラーになります。主要ベンダー(Okta、Entra ID など)の Identity Provider は、既定で適切な信頼済み証明書を備えています。
SAML シングルサインオン
Enterprise Server で設定して有効化すると、SSO システムは、たとえば Okta、OneLogin など、会社が指定した Identity Provider(IdP)から承認済みの ID を確立します。ID アサーションの通信は、標準化された Security Assertion Markup Language(SAML 2.0)に基づきます。会社向けの SSO サインインインターフェースは、まだ用意されていない場合、通常は IdP が提供するテンプレートまたは例に基づいて構築されます。これにより、SAML ベースの認証アサーション交換が開始され、社内サービスへのアクセスが提供されます。
ブラウザーインターフェースの Admin – Settings – Authentication ページにある SSO ドロップダウンで SAML オプションを選択すると、このページには Enterprise Server の SSO サービス用に事前設定された URL(Altium Metadata Configuration)と、IdP の認可接続データ(SAML Identity Provider Configuration)をアップロードまたは手動入力するためのオプションが表示されます。

IdP の設定メタデータは、会社のサービスと連携するよう Identity Provider 側の設定が完了すると入手できるはずです。以下の IdP 連携例を参照してください。Enterprise Server で SAML SSO システムを設定するには(未完了の場合)、 ボタンを使用して、会社の IdP が生成した SAML IdP 設定 XML ファイルを選択してアップロードします。アップロードされた IdP XML ファイルはシステムによって解析され、主要な設定フィールド(X509 Certificate、Identity Provider Issuer URL、IdP Single Sign-On URL)が抽出されます。代替として、設定の各要素(セキュリティ証明書と URL)を対応するフィールドに手動で追加することもできます。
ボタンを使用して、会社の IdP が生成した SAML IdP 設定 XML ファイルを選択してアップロードします。アップロードされた IdP XML ファイルはシステムによって解析され、主要な設定フィールド(X509 Certificate、Identity Provider Issuer URL、IdP Single Sign-On URL)が抽出されます。代替として、設定の各要素(セキュリティ証明書と URL)を対応するフィールドに手動で追加することもできます。
SSO は、 ボタンで呼び出される統合テストを実行するまで有効になりません。これにより、SSO の ID プロセスと会社の SSO サインインが検証されます。設定のテストが成功したら、
ボタンで呼び出される統合テストを実行するまで有効になりません。これにより、SSO の ID プロセスと会社の SSO サインインが検証されます。設定のテストが成功したら、 ボタン(
ボタン( )をクリックして設定を保存し、Enterprise Server に適用します。
)をクリックして設定を保存し、Enterprise Server に適用します。
その後、手動操作または設定変更により SSO が無効化された場合は、 ボタンが利用可能になり、テストプロセスを再実行できます。
ボタンが利用可能になり、テストプロセスを再実行できます。
Identity Provider 連携例
以下の折りたたみセクションを展開すると、Identity Provider として OneLogin を連携する手順例を確認できます。
Integration with OneLogin
-
管理者として OneLogin にログインします。
-
Applications を選択し、次に Add Apps を選択します。
-
「SAML」を検索し、SAML Test Connector (Advanced) IdP アプリケーションオプションを選択します。
-
アプリケーション名(Display Name)を指定します。これは表示目的のみに使用されます。
-
Save ボタンをクリックします。
-
Enterprise Server のブラウザーインターフェースの Admin – Settings – Authentication ページから、Entity ID および Single Sign-On URL(Assertion Consumer Service)の項目をコピー( )し、以下の指定どおりに各フィールドへ貼り付けます。
)し、以下の指定どおりに各フィールドへ貼り付けます。

OneLogin のアプリケーション設定で:
-
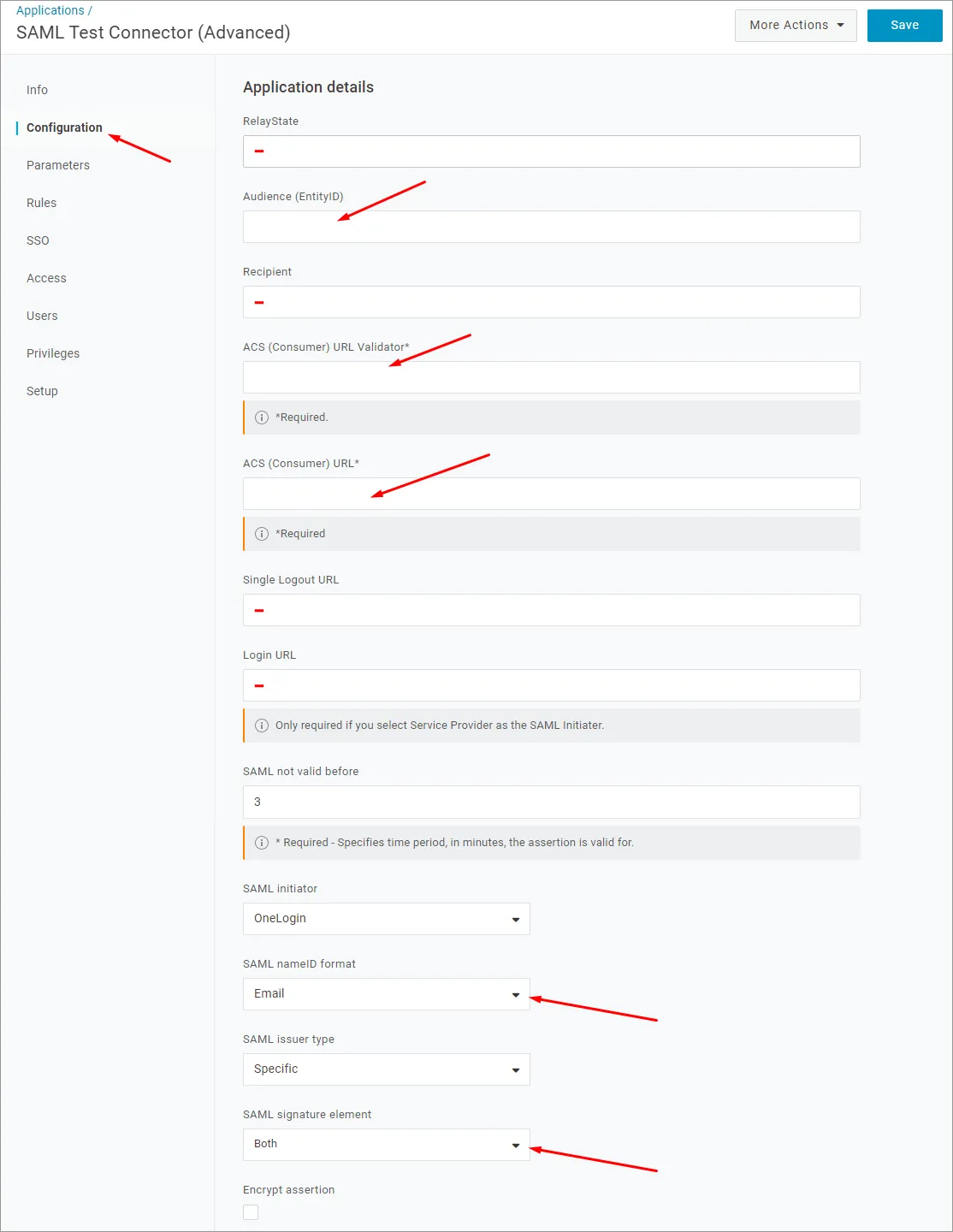
上記の Entity ID (サービスプロバイダー名)を Audience (EntityID) URL として貼り付けます。
-
上記の Single Sign-On URL(Assertion Consumer Service)を ACS (Consumer) URL Validator として貼り付けます。
-
また、Single Sign-On URL(Assertion Consumer Service)を ACS (Consumer) URL として貼り付けます。
-
RelayState、Recipient、Single Logout URL、Login URL の各フィールドは空欄のままでも構いません。
-
SAML nameID format オプションが Email に設定され、SAML signature element が Both に設定されていることを確認します。Save ボタンをクリックして設定を確定します。
-
More Actions ボタンをクリックし、次に SAML Metadata メニューオプションを選択して、Identity Provider の SAML メタデータを XML ファイルとしてダウンロードします。
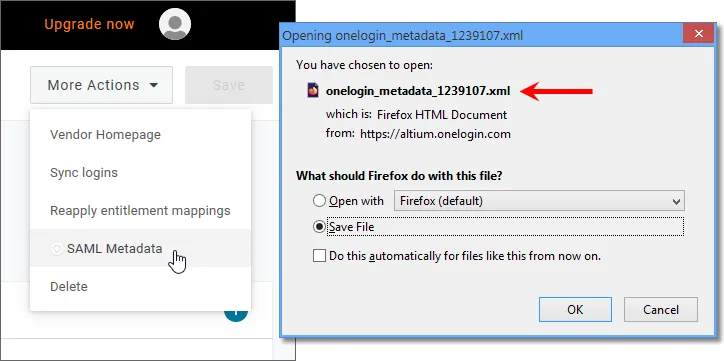
-
このメタデータファイルは、Enterprise Server のブラウザーインターフェースの Admin – Settings – Authentication ページでアップロードして OneLogin SSO サービスを設定します。以下を参照。
-
Enterprise Server 側で OneLogin SSO サービスを手動設定したい場合は、OneLogin アプリケーションインターフェースで SSO メニューオプションを選択すると必要なパラメータを確認できます。
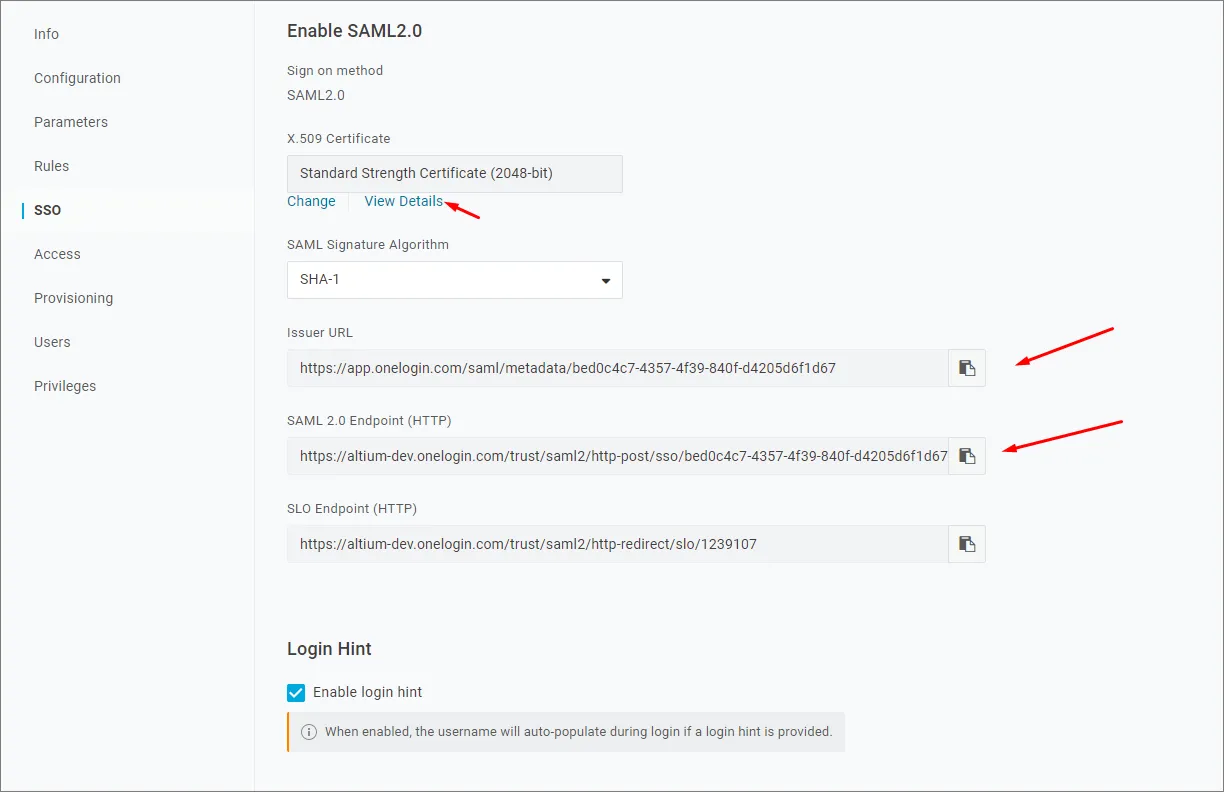
-
続く手順として、ユーザーを追加し、それらのユーザーにアプリケーションを割り当てます。
以下の折りたたみセクションを展開すると、Identity Provider として Okta を連携する手順例を確認できます。
Integration with Okta
-
管理者として Okta にサインインします。
-
Admin リンク/ボタンをクリックし、次に会社の Applications の下にある Add Application ボタンをクリックします。
-
Create New App ボタンをクリックします。

-
Sign-on method として SAML 2.0 を選択します。
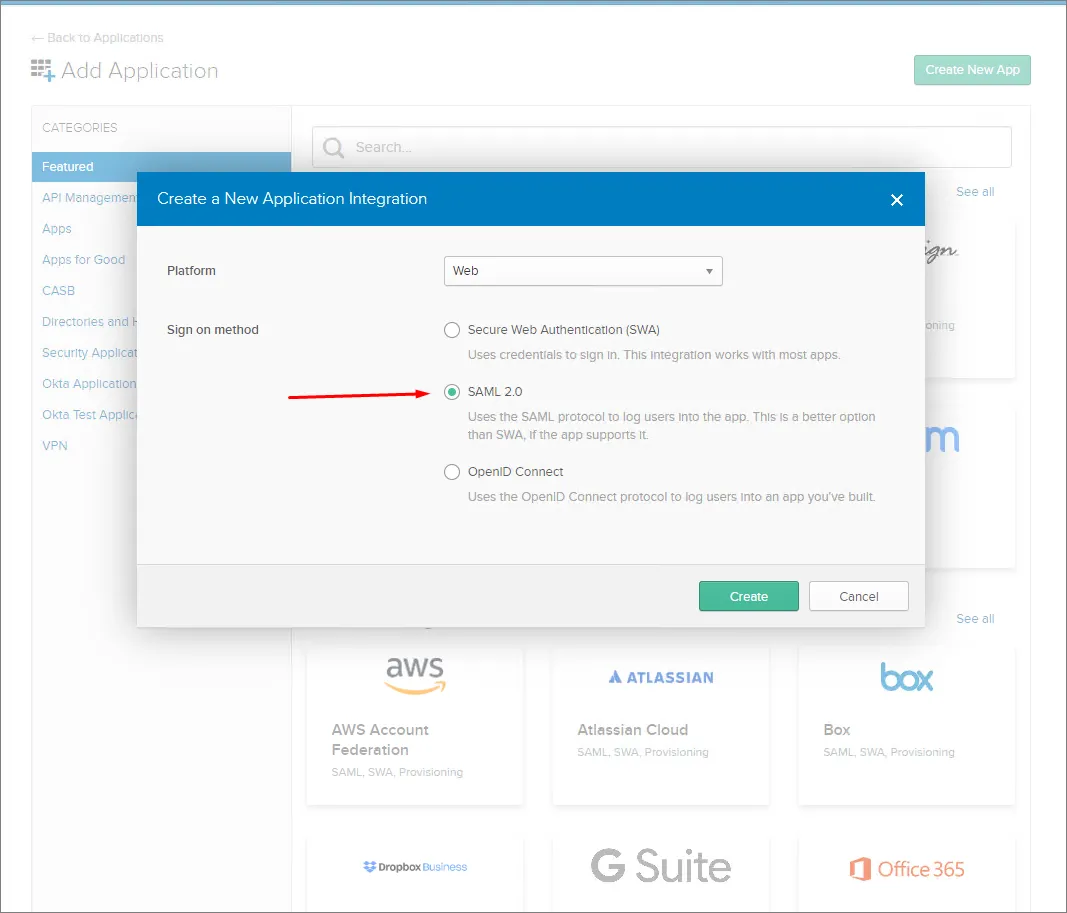
-
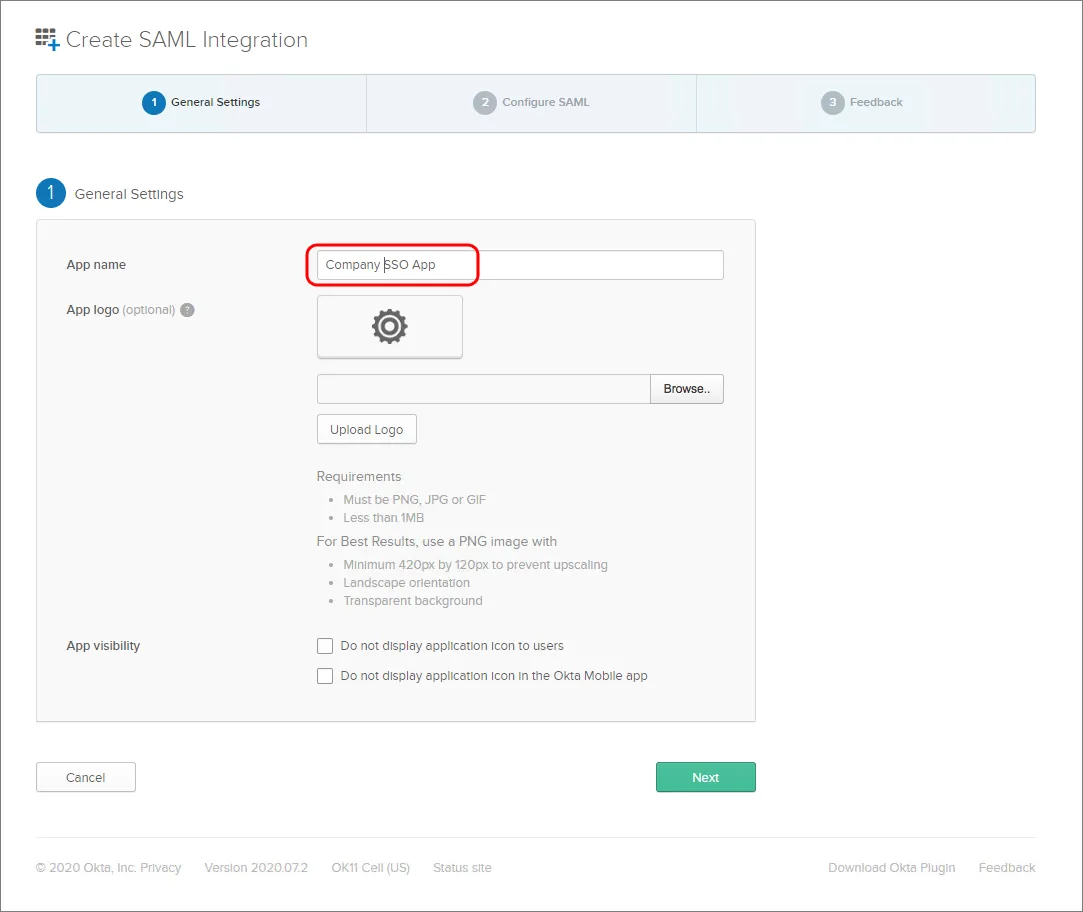
App name を指定します。これは表示目的のみに使用されます。
-
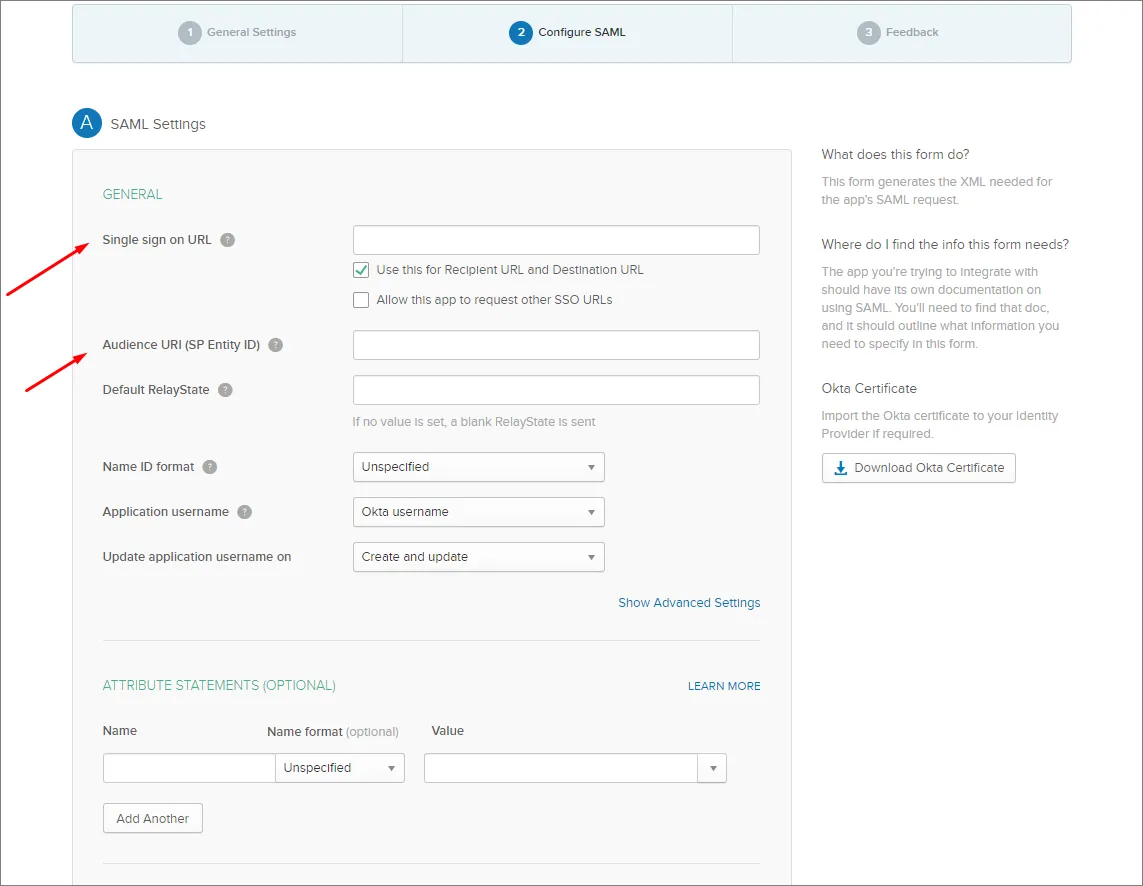
Enterprise Server のブラウザーインターフェースの Admin – Settings – Authentication ページにある Single Sign On URL(Assertion Consumer Service)および Entity ID の項目を確認します。

-
Enterprise Server の Single Sign-On URL 項目をコピー( )して、Okta の SAML Settings の Single sign on URL フィールドに貼り付けます。
)して、Okta の SAML Settings の Single sign on URL フィールドに貼り付けます。
-
Enterprise Server の Entity ID 項目をコピー( )して、Okta の SAML Settings の Audience URI フィールドに貼り付けます。
)して、Okta の SAML Settings の Audience URI フィールドに貼り付けます。
Default RelayState の項目は不要です。
-
残りのフィールドを次のように設定します:
-
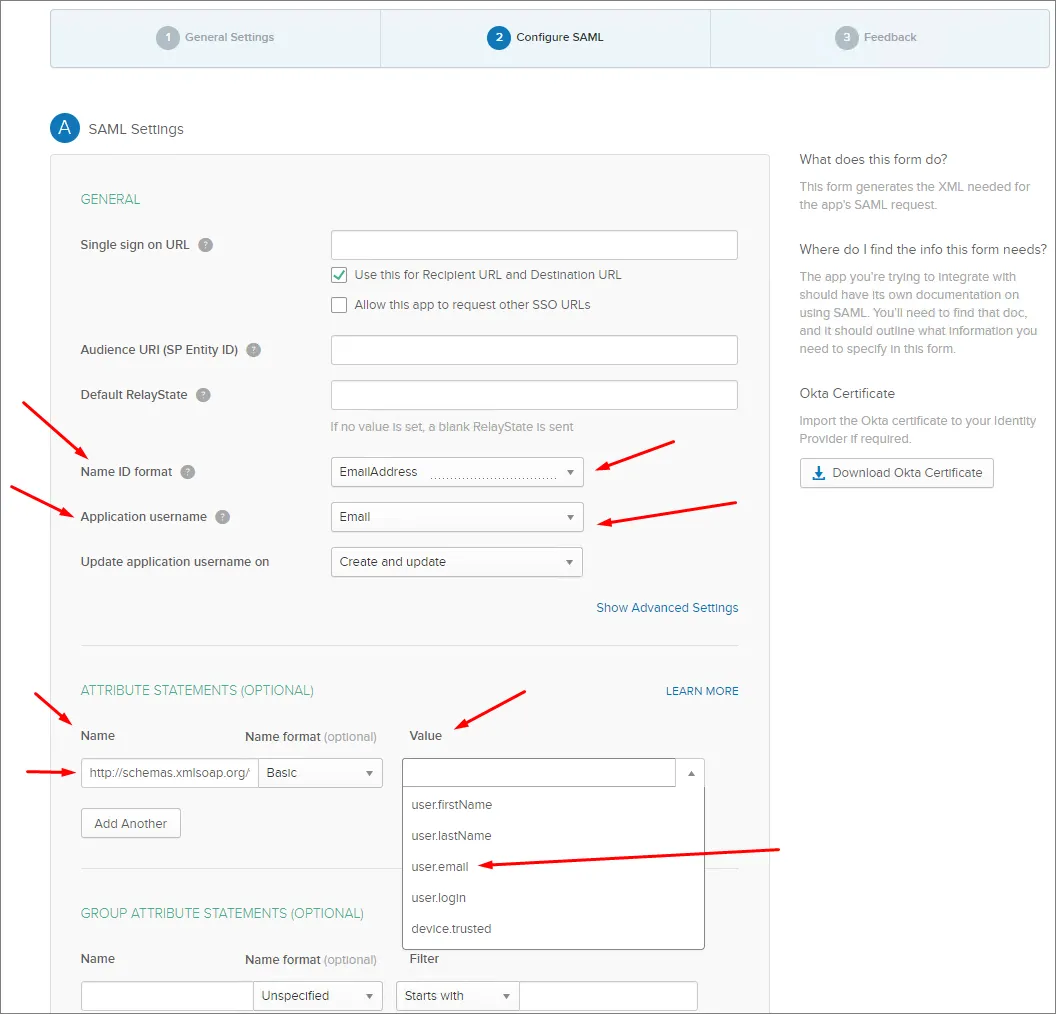
Name ID format は EmailAddress です。
-
Application username は(Okta)Email です。
-
ATTRIBUTE STATEMENTS セクションで、Name フィールドを http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress に、Value を user.email
-
に設定します。user.email

-
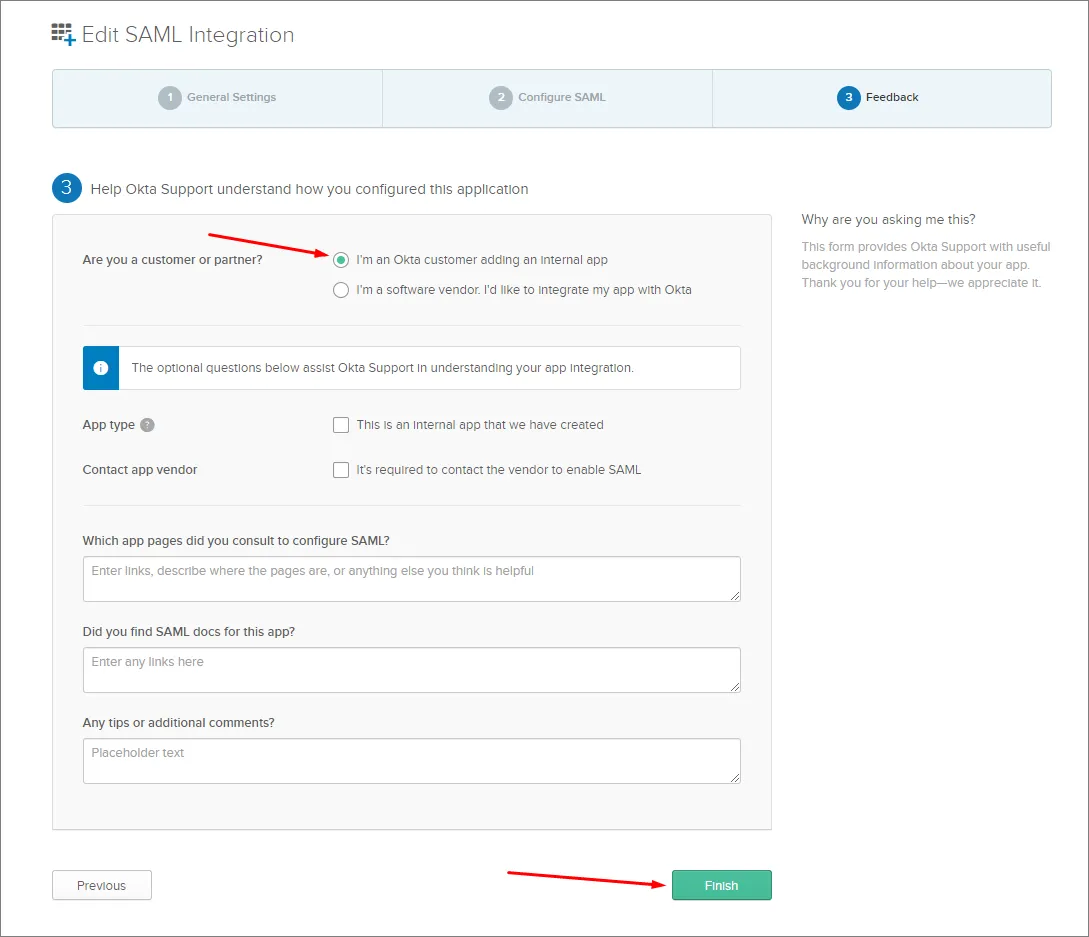
Next ボタンをクリックし、..Okta customer adding an internal app オプションを選択します。
-
Finish ボタンをクリックします。
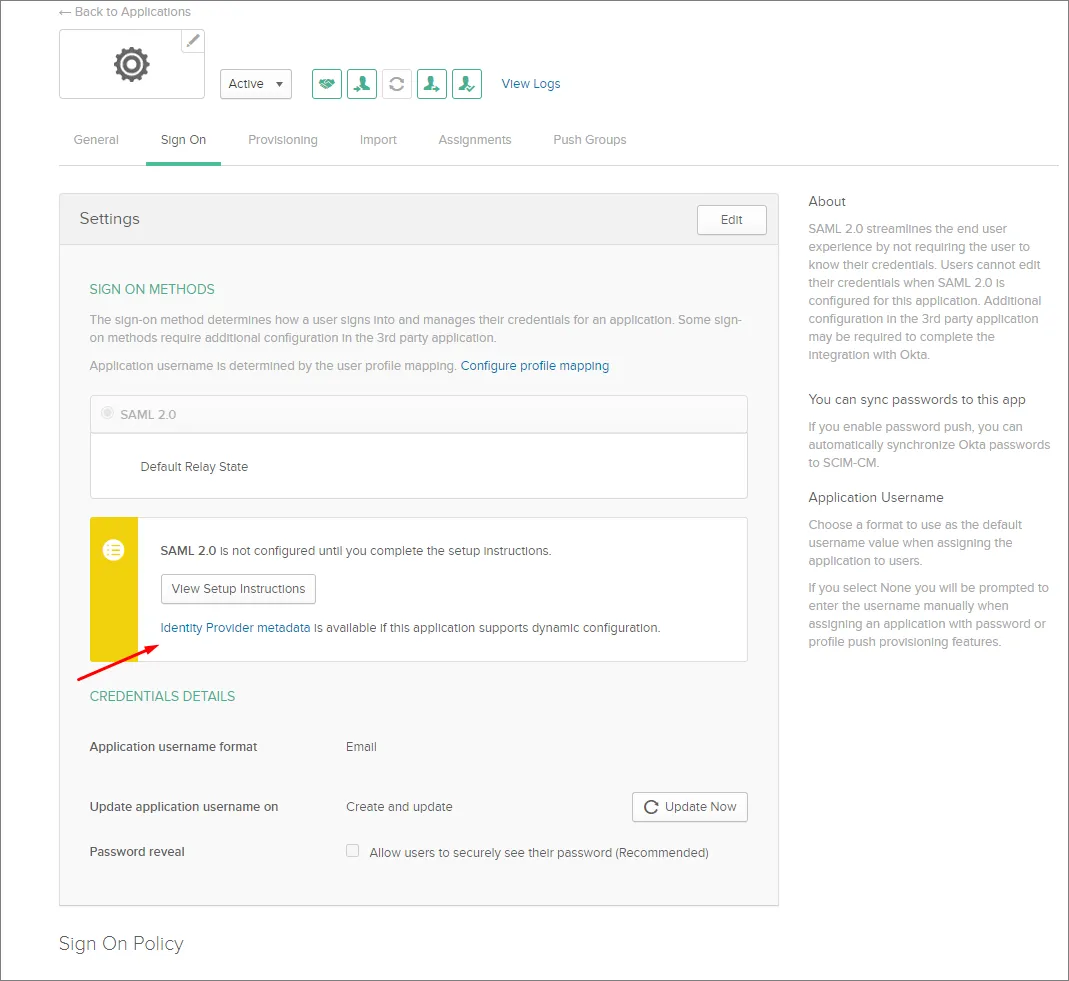
-
Identity Provider metadata リンクをクリックしてメタデータ XML をコンピューターに保存するか、手動設定オプションとして View Setup Instructions ボタンをクリックします。
-
Enterprise Server のブラウザーインターフェースの Admin – Settings – Authentication ページにある SAML Identity Provider configuration セクションで、保存したメタデータ XML ファイルをアップロードするか、各セクションを手動で設定します。上記を参照。
以下の折りたたみセクションを展開すると、Identity Provider として Microsoft Entra ID を連携する手順例を確認できます。
Integration with Microsoft Entra ID
-
Microsoft Entra admin center にサインインします。
-
Identity を選択し、次に Enterprise applications オプションを選択します。
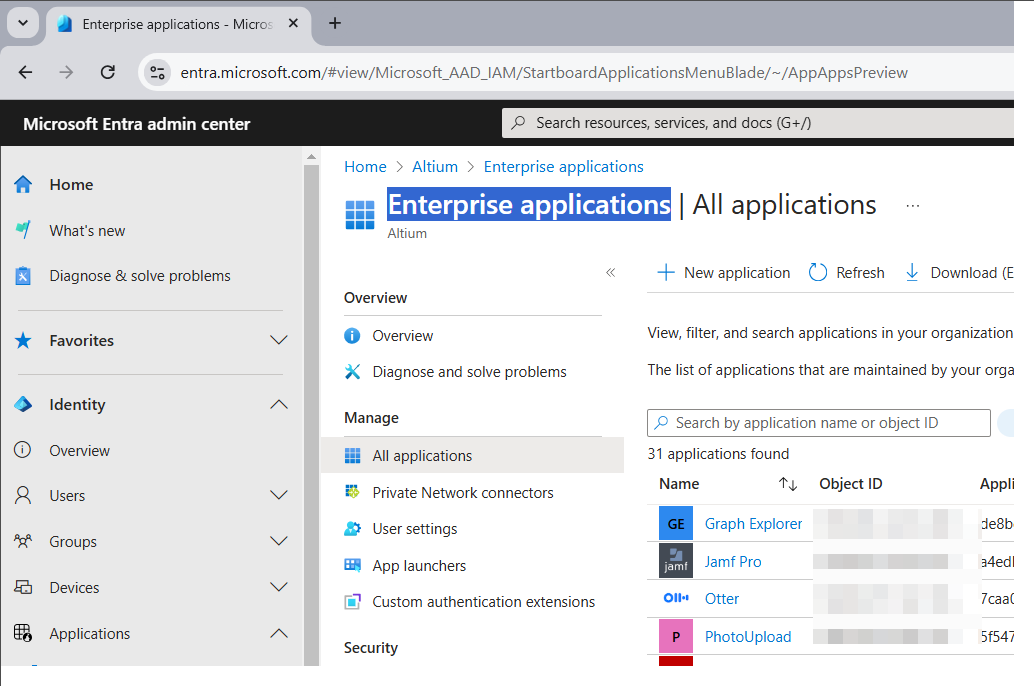
-
独自のアプリケーションを作成します。
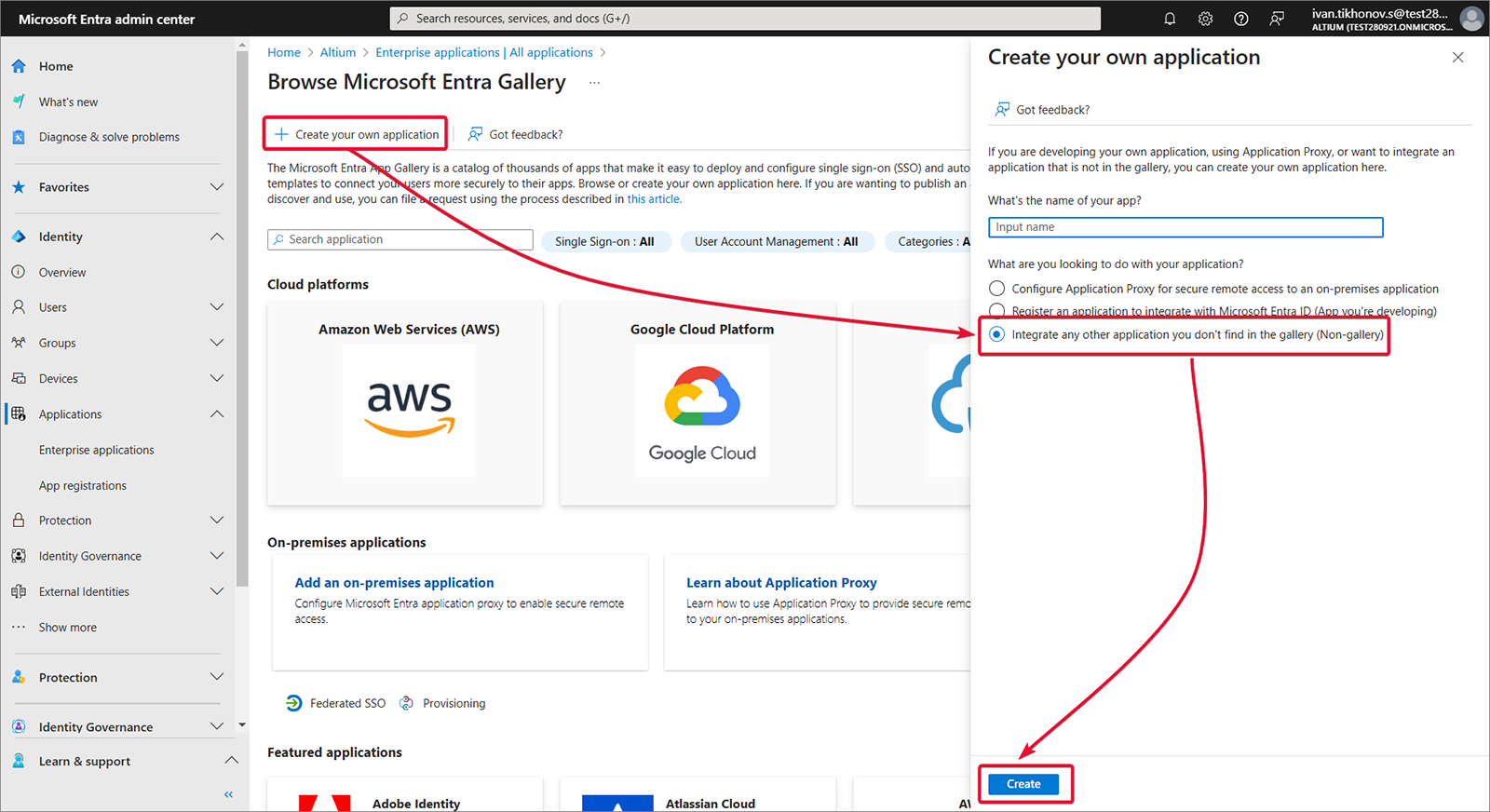
-
Users and groups を選択し、次に Add user/group を選択します。
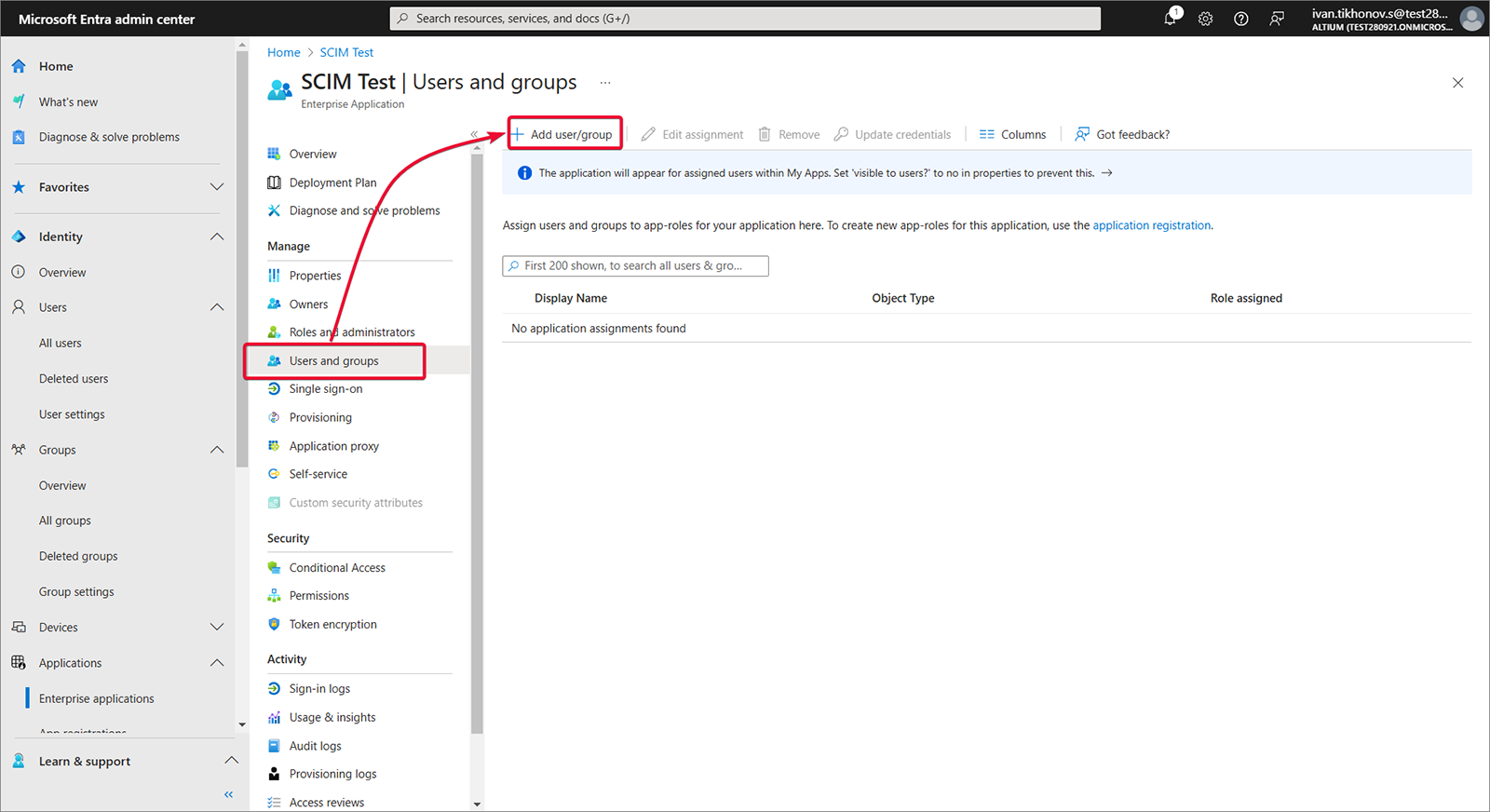
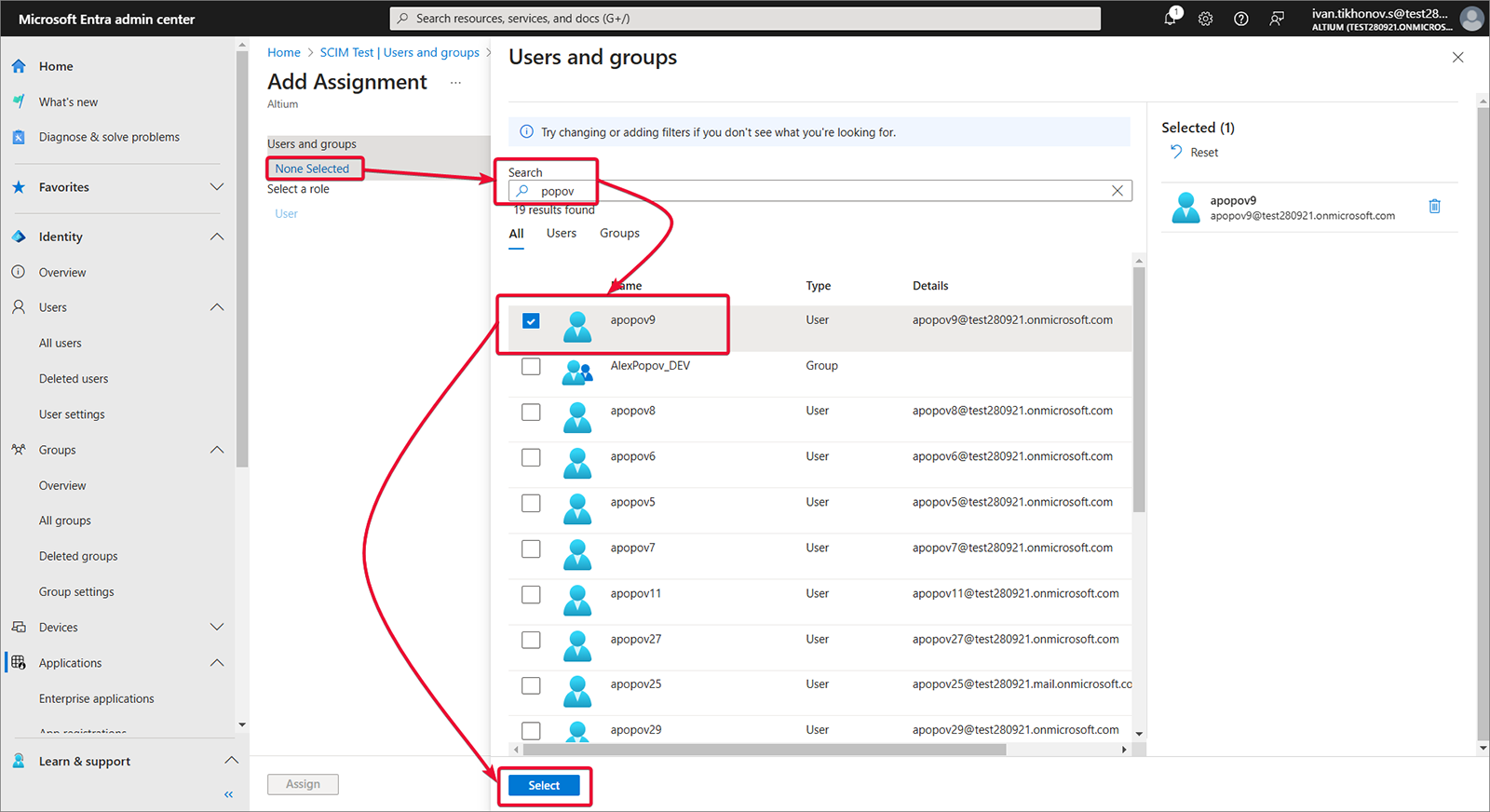
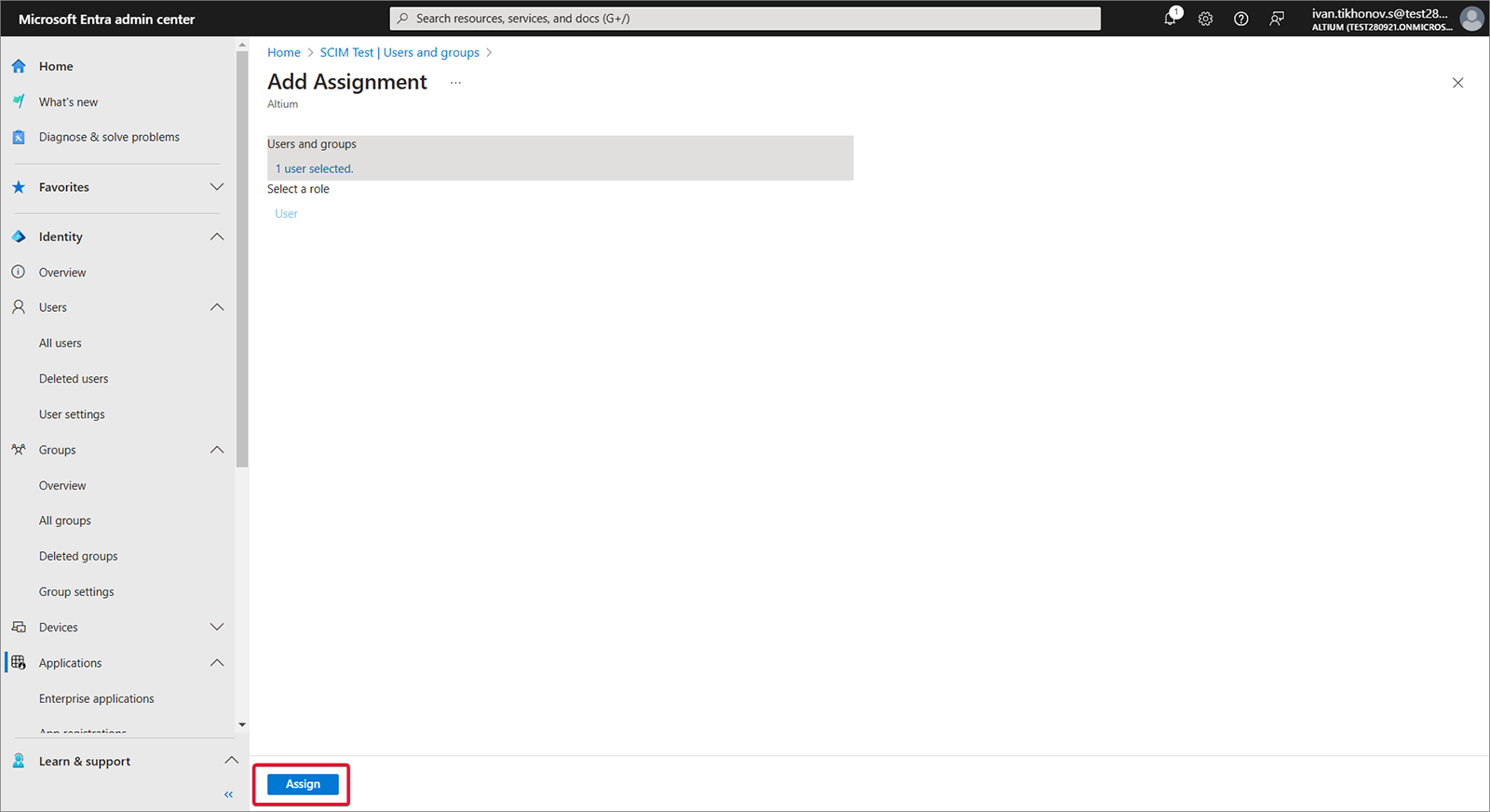
-
Single sign-on、Step 1、次に Edit を選択します。
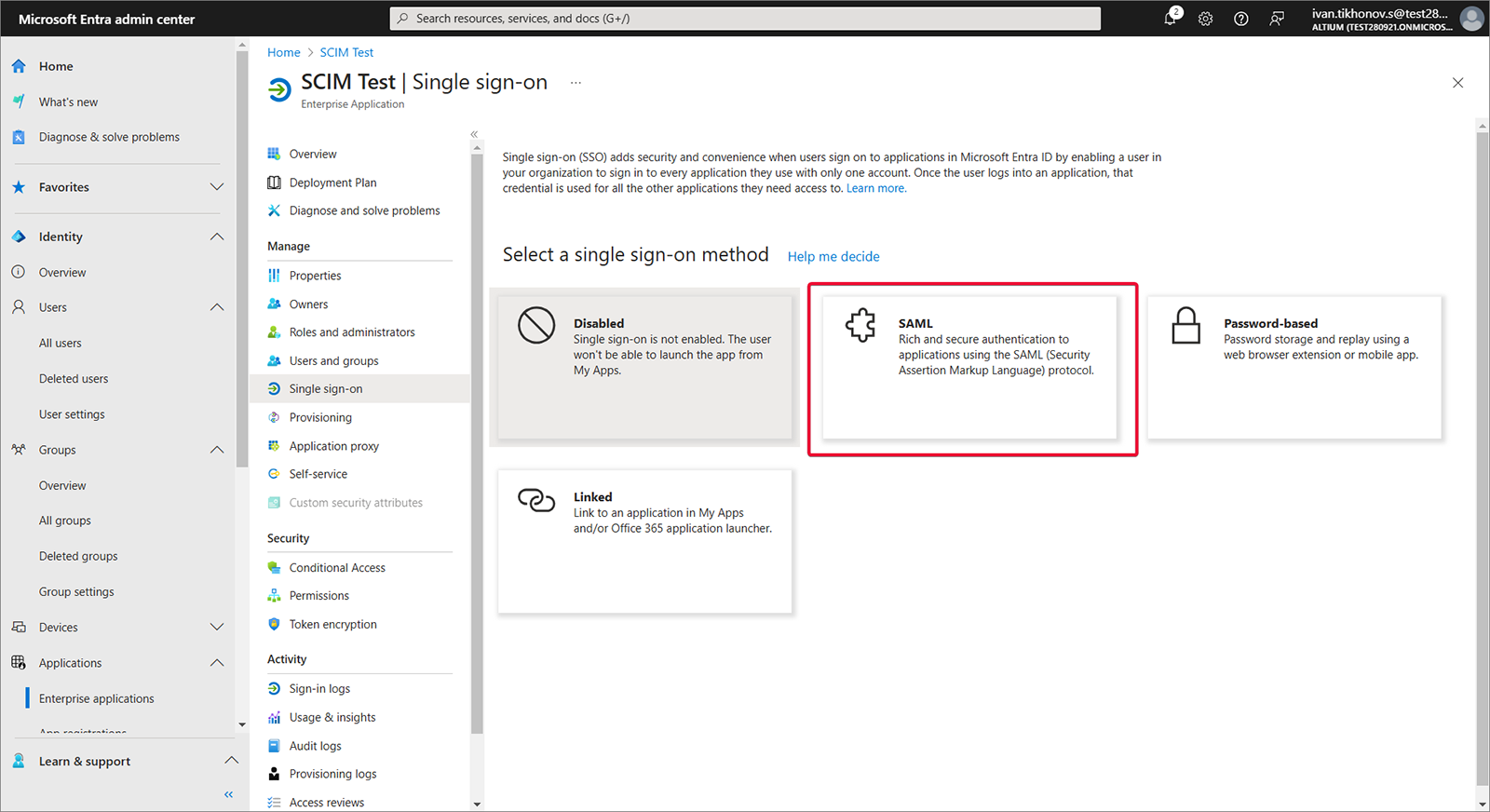
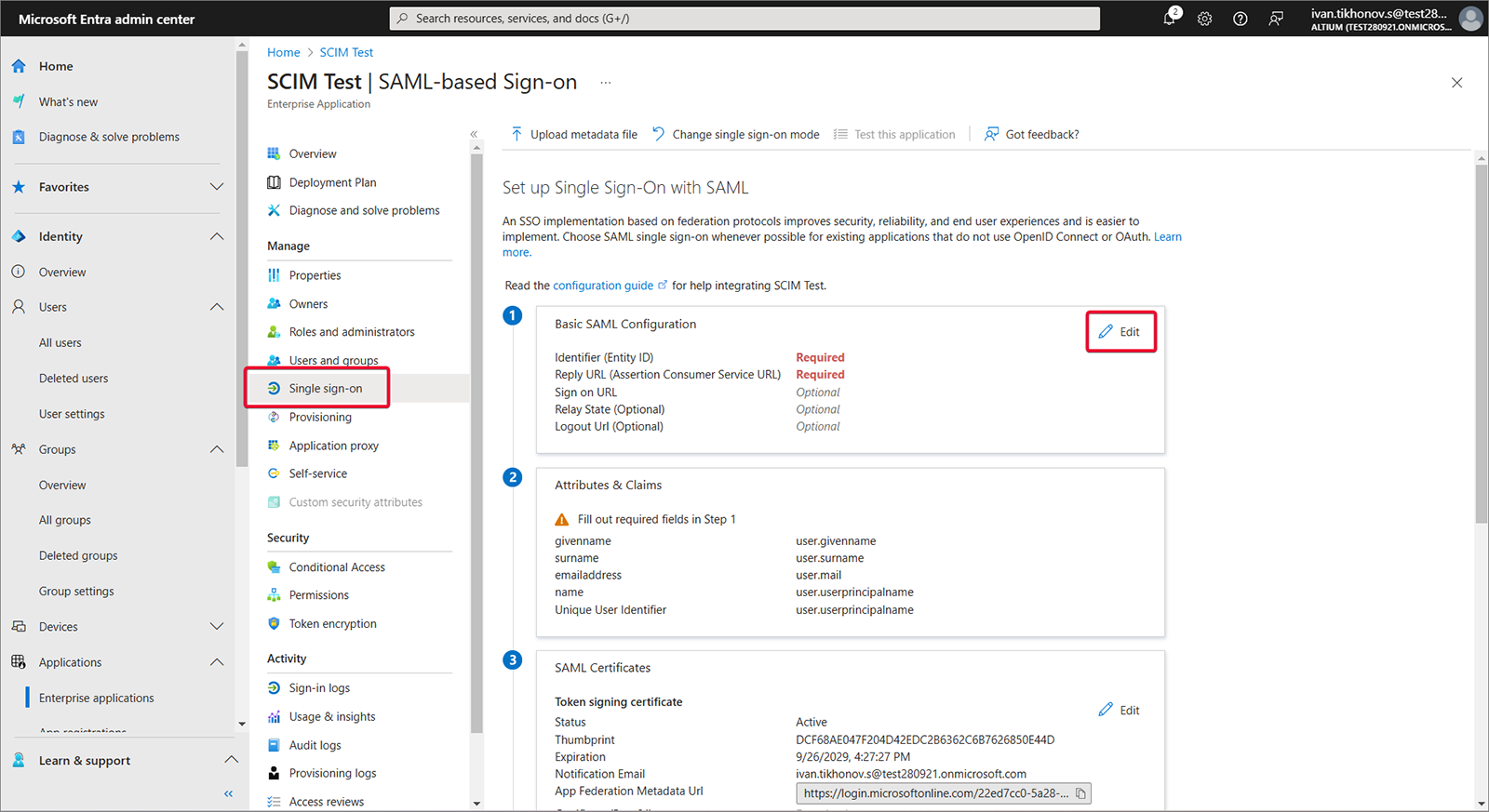
-
Enterprise Server のブラウザーインターフェースの Admin – Settings – Authentication ページから Entity ID と Single Sign-On URL をコピー( )します。コピーした文字列を、Microsoft Entra アプリの SAML Configuration 領域にある Entity ID および Assertion Consumer Service URL フィールドに貼り付けます。これらのフィールドの Default チェックボックスがオンになっていることを確認し、設定を保存します。
)します。コピーした文字列を、Microsoft Entra アプリの SAML Configuration 領域にある Entity ID および Assertion Consumer Service URL フィールドに貼り付けます。これらのフィールドの Default チェックボックスがオンになっていることを確認し、設定を保存します。

-
作成した Federation Metadata XML をダウンロードします。
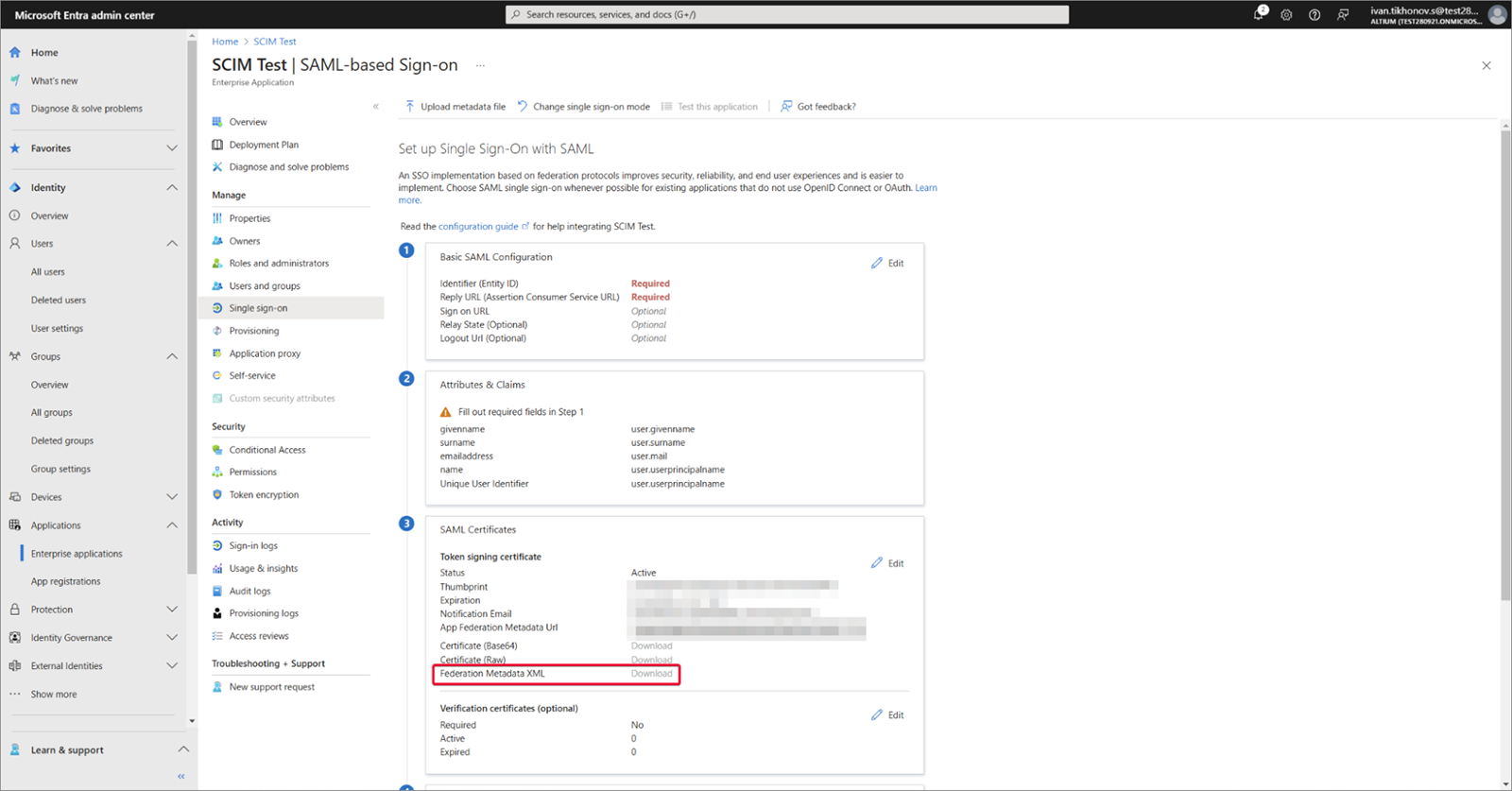
-
Federation Metadata XML を Enterprise Server のブラウザーインターフェースの Admin – Settings – Authentication ページにアップロードし、SAML 連携接続をテストします。上記を参照。
以下の折りたたみセクションを展開すると、Identity Provider として JumpCloud を連携する手順例を確認できます。
Integration with JumpCloud
-
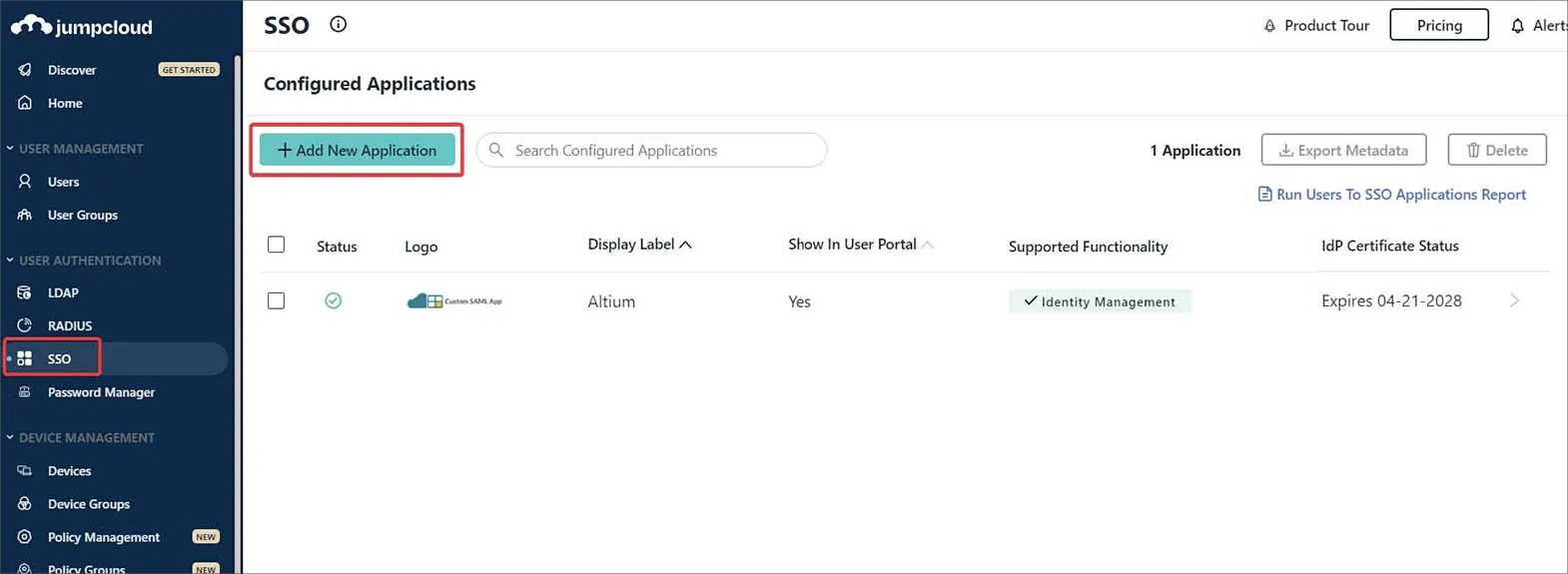
JumpCloud のインターフェースで、ナビゲーションツリーから SSO を選択し、次に SSO ページの Add New Application ボタンをクリックします。
-
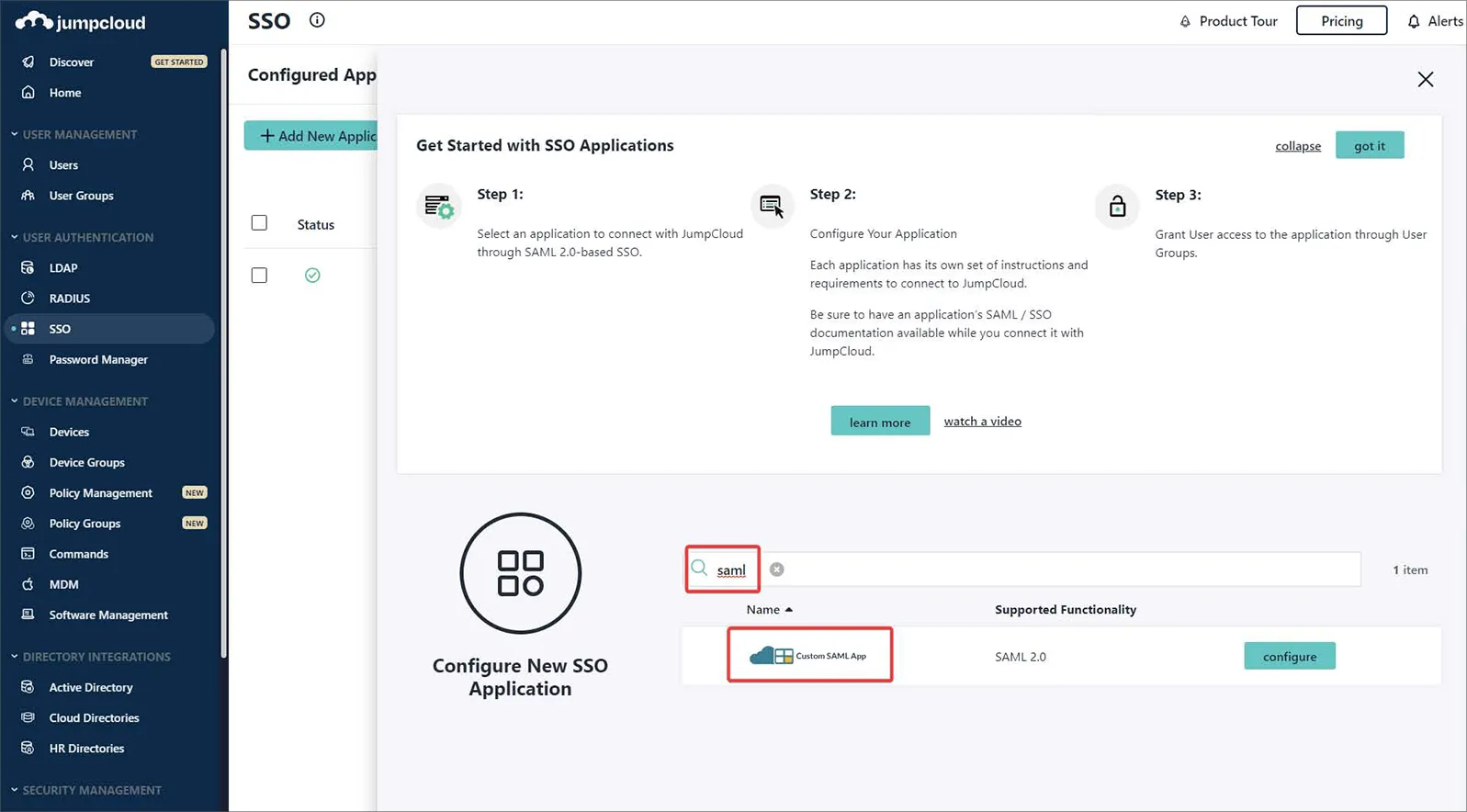
設定ウィンドウの Search に「saml」と入力して Custom SAML App を見つけ、インストールします。
-
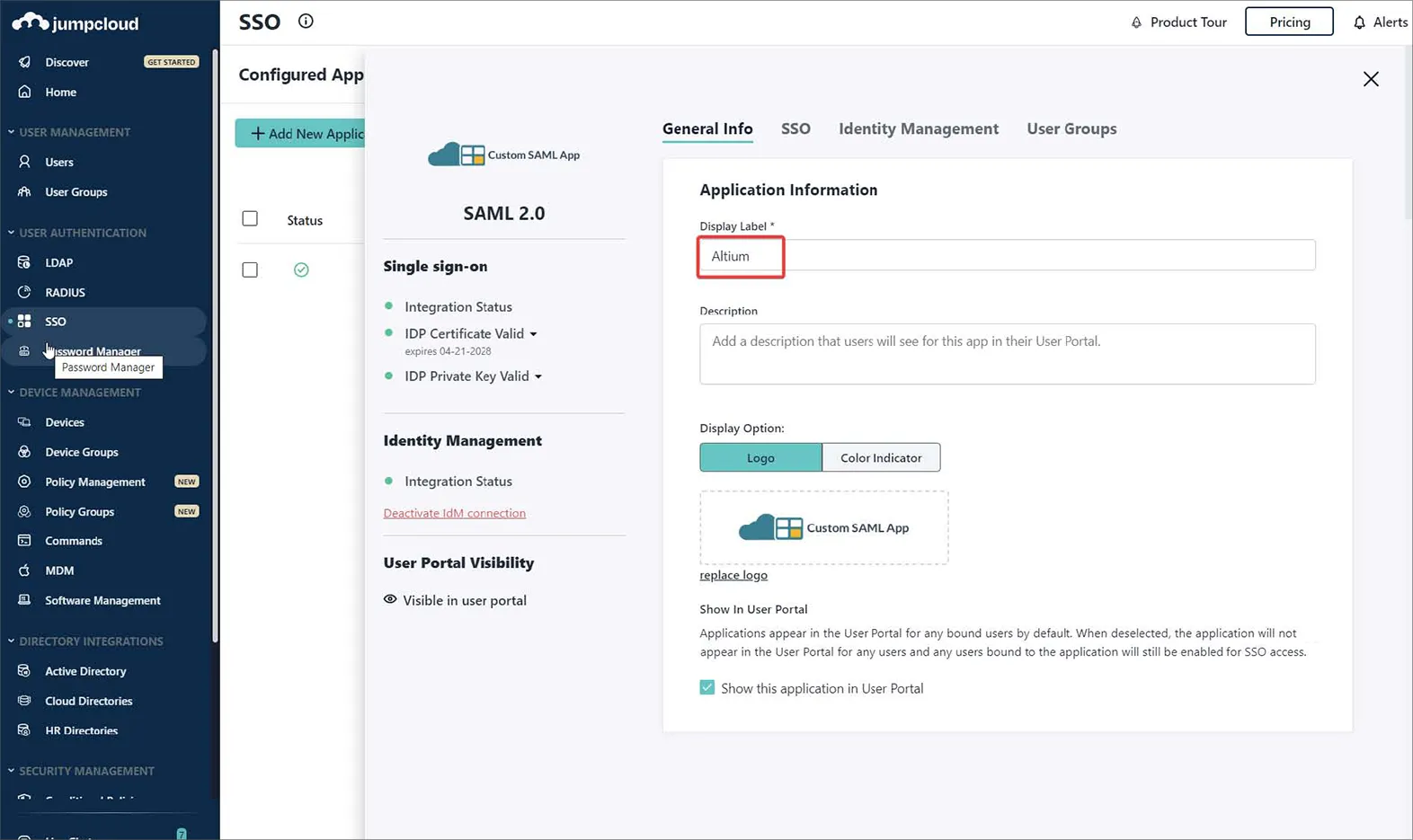
Custom SAML App のインスタンスに名前を付けます。この例ではラベルは Altium です。
-
JumpCloud の設定インターフェースで SSO タブに切り替え、表示されているとおりに Enterprise Server のブラウザーインターフェースの Admin – Settings – Authentication ページから Entity/URL 設定を入力します。

-
JumpCloud のエンドポイント IDP URL を入力し、Declare Redirect Endpoint オプションを有効にします。
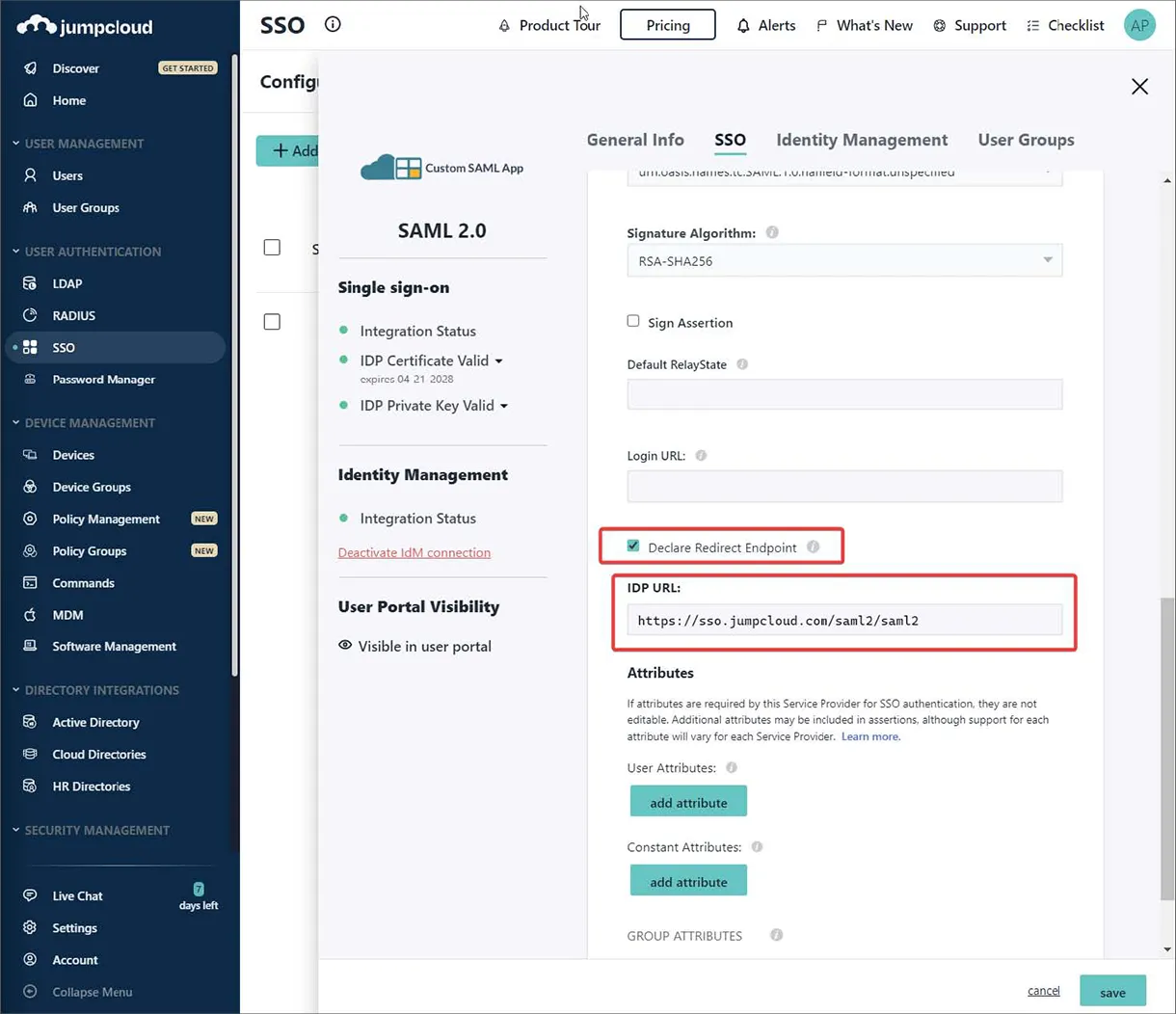
-
Export Metadata オプションを使用して、生成された SAML メタデータ XML ファイルをダウンロードします。
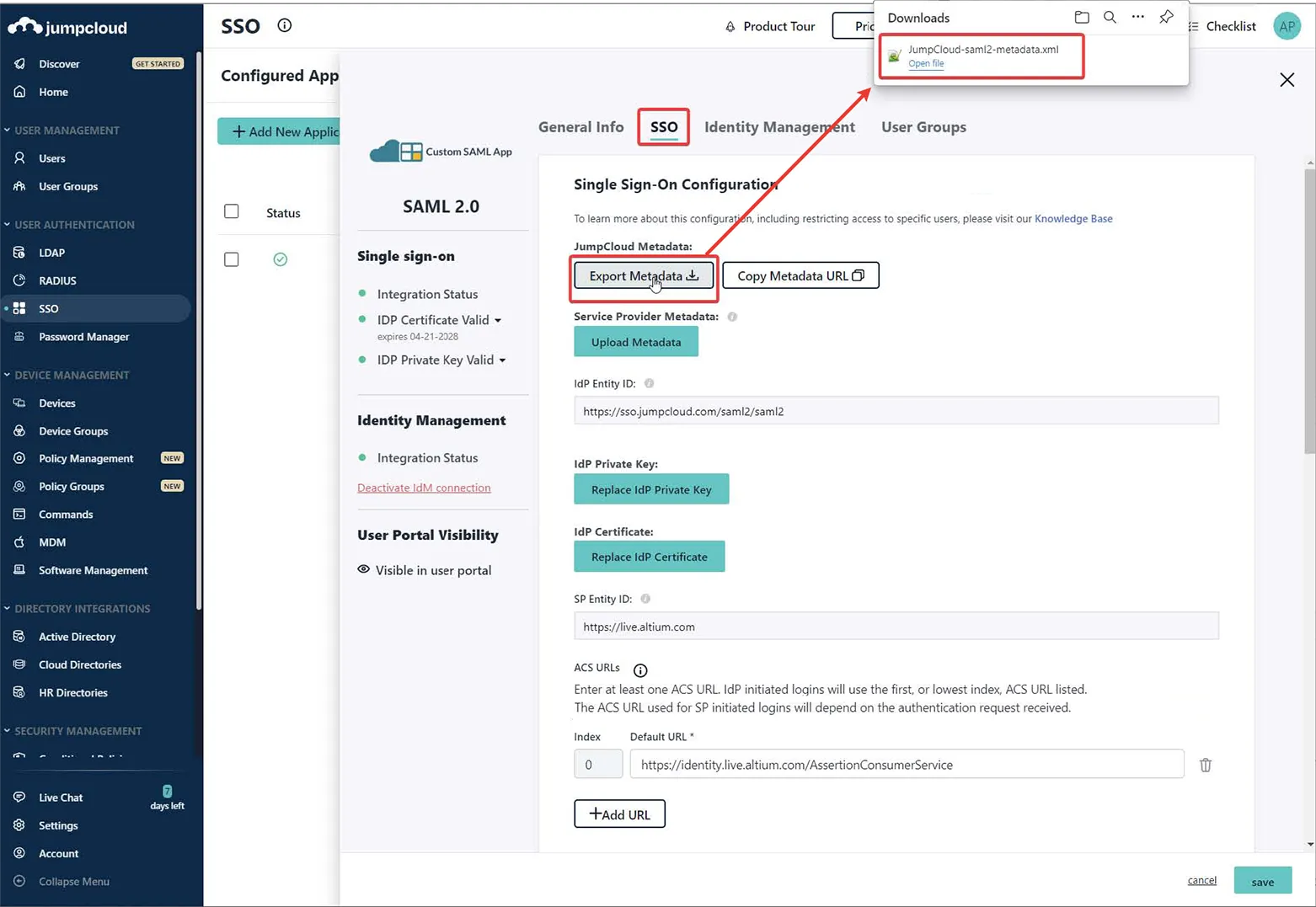
-
メタデータ XML ファイルを Enterprise Server のブラウザインターフェースの Admin – Settings – Authentication ページにアップロードし、その後 SAML 統合接続をテストします – 上記参照。
以下の折りたたみセクションを展開すると、ID プロバイダーとして Microsoft Administrative Domain Federated Services (AD FS) を使用する統合プロセスの手順例を確認できます。
Integration with Microsoft AD FS
AD FS インスタンスへの管理者アクセス権が必要です。
-
AD FS Management アプリケーション(通常は Start → Windows Administrative Tools → AD FS Management)を開きます。
-
Relying Party Trusts に移動し、Add Relying Party Trust... オプション (1) をクリックします。
-
ポップアップウィンドウで Claims aware (2) を選択していることを確認し、Start (3) をクリックします。
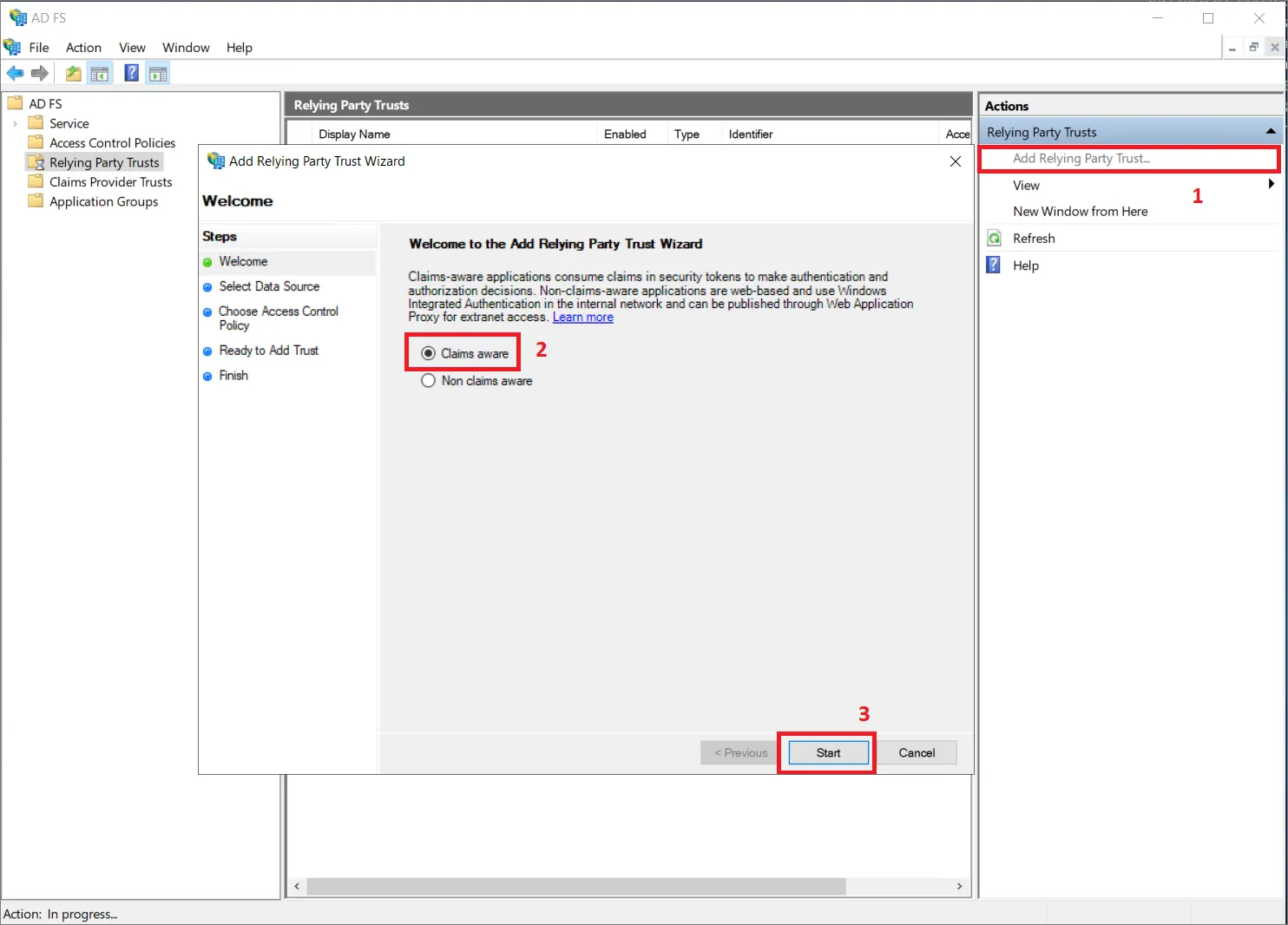
-
Select Data Source ステップで Enter data about the relying party manually (1) を選択し、Next (2) をクリックします。
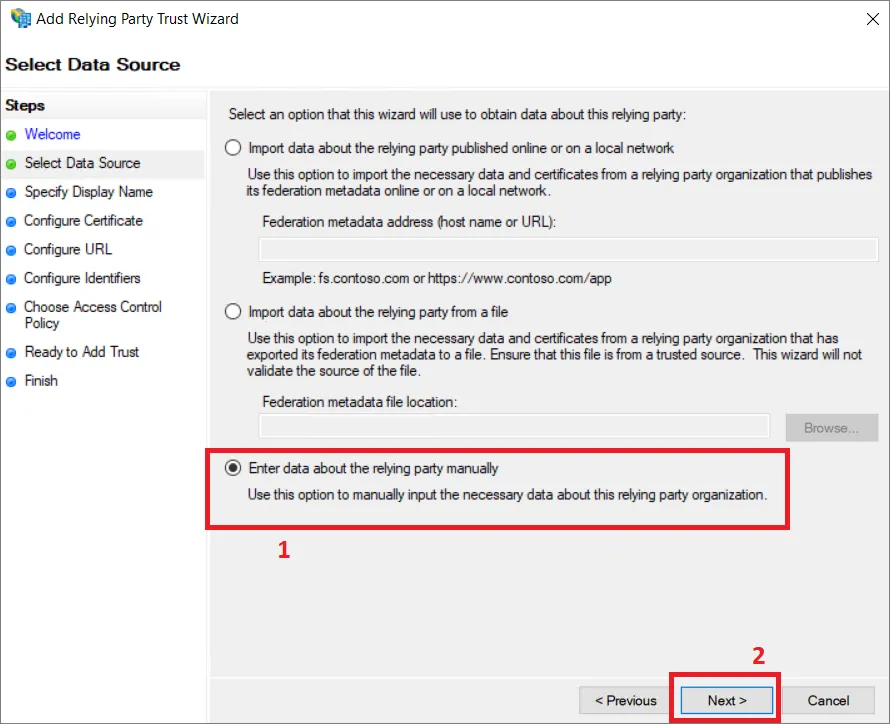
-
信頼(trust)の表示名を指定します。この例では表示名に AltiumLive を使用します。
-
セキュリティ構成によっては、任意のトークン暗号化証明書を指定できます。本ガイドでは使用しません。
-
Configure URL ステップで Enable support for the SAML 2.0 WebSSO protocol オプション (1) を選択していることを確認し、Enterprise Server のブラウザインターフェースの Admin – Settings – Authentication ページからコピーした Single Sign-On URL を Relying party SAML 2.0 SSO service URL: フィールド (2) に入力します。Next (3) をクリックします。

-
Configure Identifiers ステップで、この信頼の識別子を入力フィールド (1) に指定します。識別子は、Enterprise Server のブラウザインターフェースの Admin – Settings – Authentication ページの Altium Metadata Configuration 領域にある Entity ID エントリから取得する必要があります。Add ボタン (2) をクリックしていることを確認します。

結果は次のようになります。Next をクリックします。

-
セキュリティ構成によっては、次のステップで任意のアクセス制御ポリシーを選択できます。この例では追加ポリシーは選択せず、Permit everyone オプションで続行します。
-
構成を確認し、Next を選択します。
-
信頼のセットアップ中は、すべての設定が利用できるわけではありません。SHA-1 をセキュア ハッシュ アルゴリズムとして使用できるようにするには、追加したばかりの Relying Party Trust の名前を右クリックし、Properties を選択します。
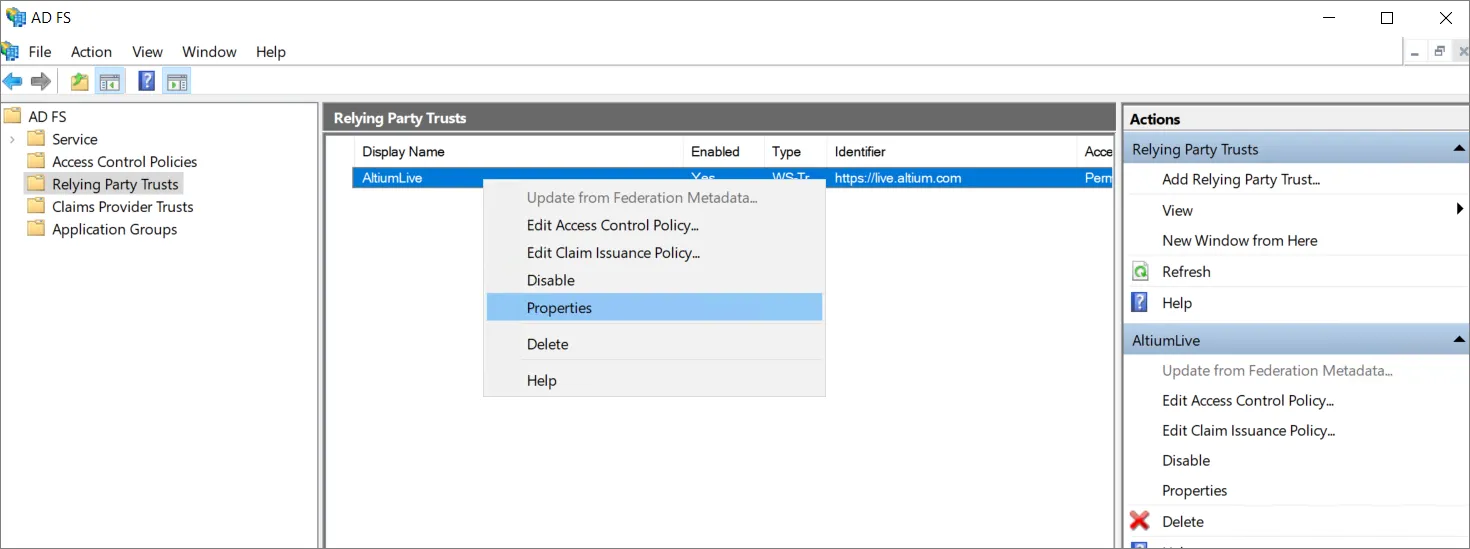
-
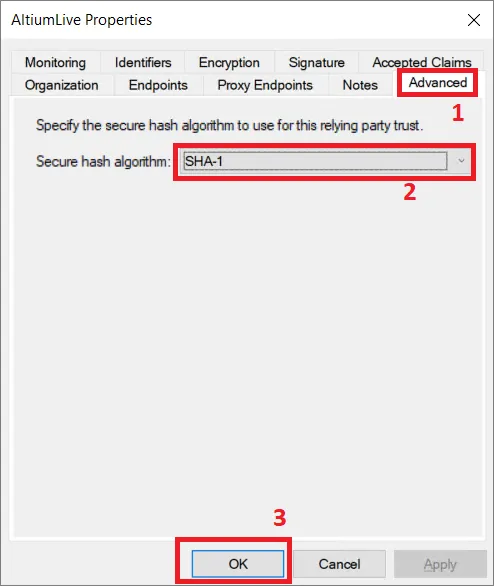
プロパティウィンドウで Advanced タブ (1) を選択し、セキュア ハッシュ アルゴリズムとして SHA-1 (2) を設定します。変更を保存するには OK をクリックします。
-
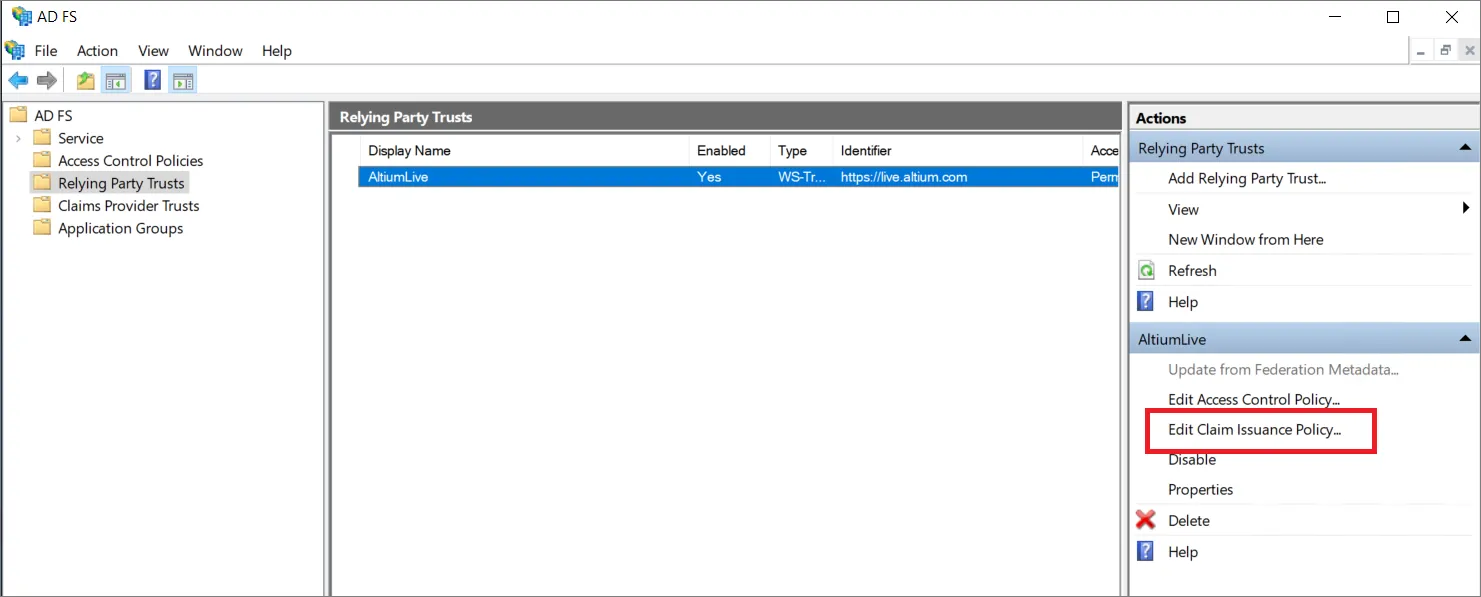
AD FS 管理ウィンドウに戻り、追加した Relaying Party Trust を選択して Edit Claim Issuance Policy... オプションを選びます。
-
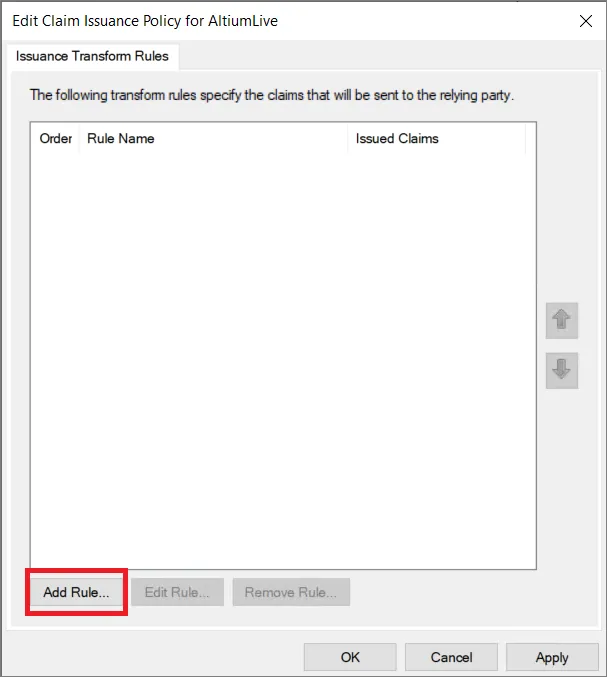
Edit Claim Issuance Policy ウィンドウで Add Rule...
-
Choose Rule Type ウィザードのステップで Send LDAP Attributes as Claims が選択されていることを確認し、Next をクリックします。
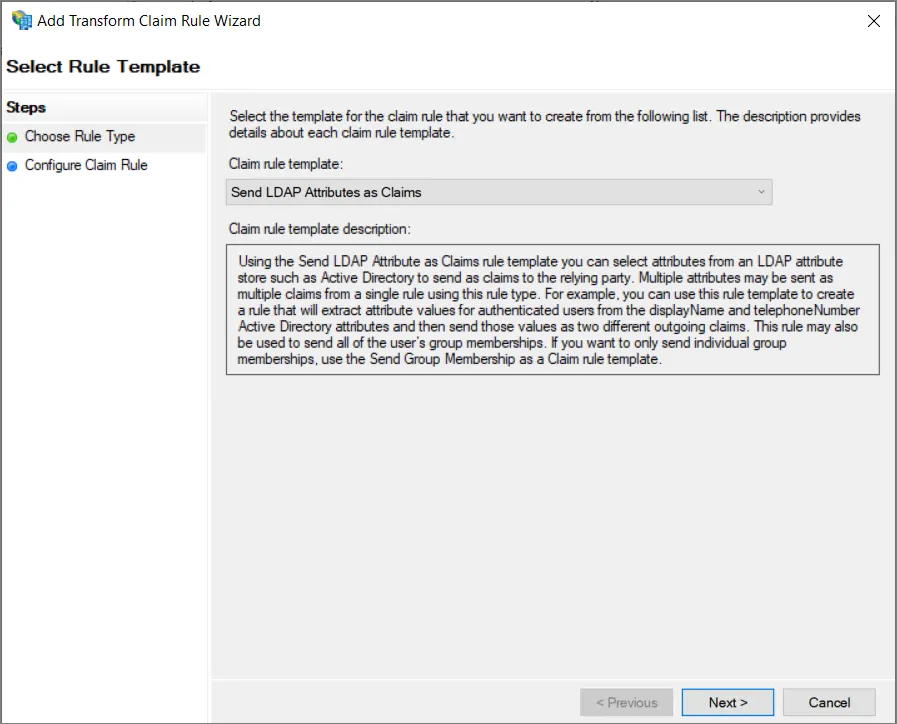
-
Claim rule name (1) を指定し、 Attribute store として Active Directory (2) を選択し、Enterprise Server ユーザーのユーザー名を含む ID から LDAP Attribute (3) を選択します。この属性は Outgoing Claim Type (3) の Name ID にマッピングする必要があります。Finish (4) をクリックします。
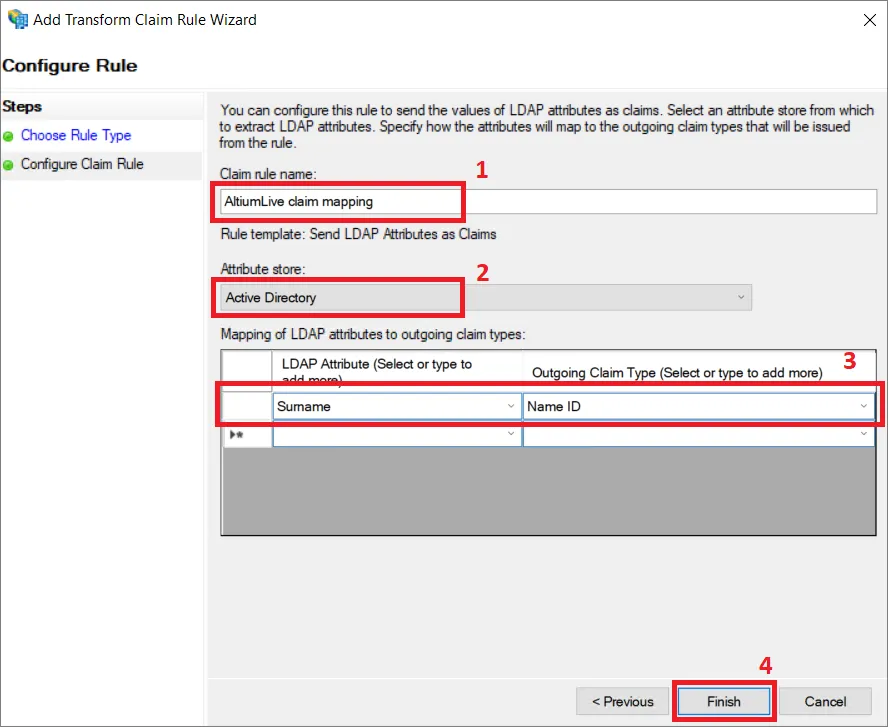
Important Note:この例では、必要な値を含むように Surname または Last name をマッピングしています。構成は環境によって異なる場合があります。
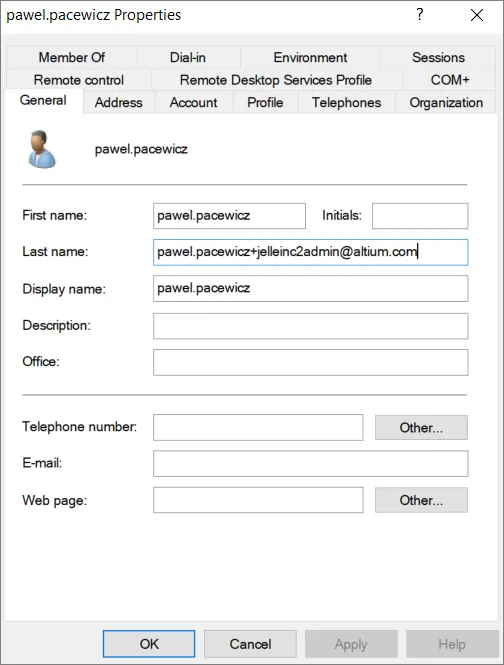
-
OK をクリックして、クレーム発行ポリシーが保存されていることを確認します。
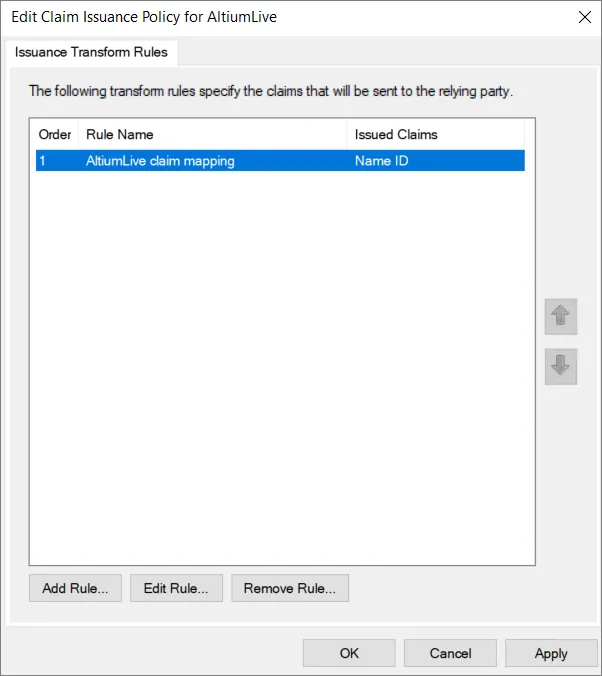
-
適切なサーバーから FederationMetadata.xml ファイルをダウンロードします。
-
メタデータ XML ファイルを Enterprise Server のブラウザインターフェースの Admin – Settings – Authentication ページにアップロードし、その後 SAML 統合接続をテストします – 上記参照。
以下の折りたたみセクションを展開すると、ID プロバイダーとして AWS IAM Identity Center を使用する統合プロセスの手順例を確認できます:
Integration with AWS IAM Identity Center
-
IAM Identity Center に移動し、カスタム SAML 2.0 アプリケーション(Add Application)を追加します。
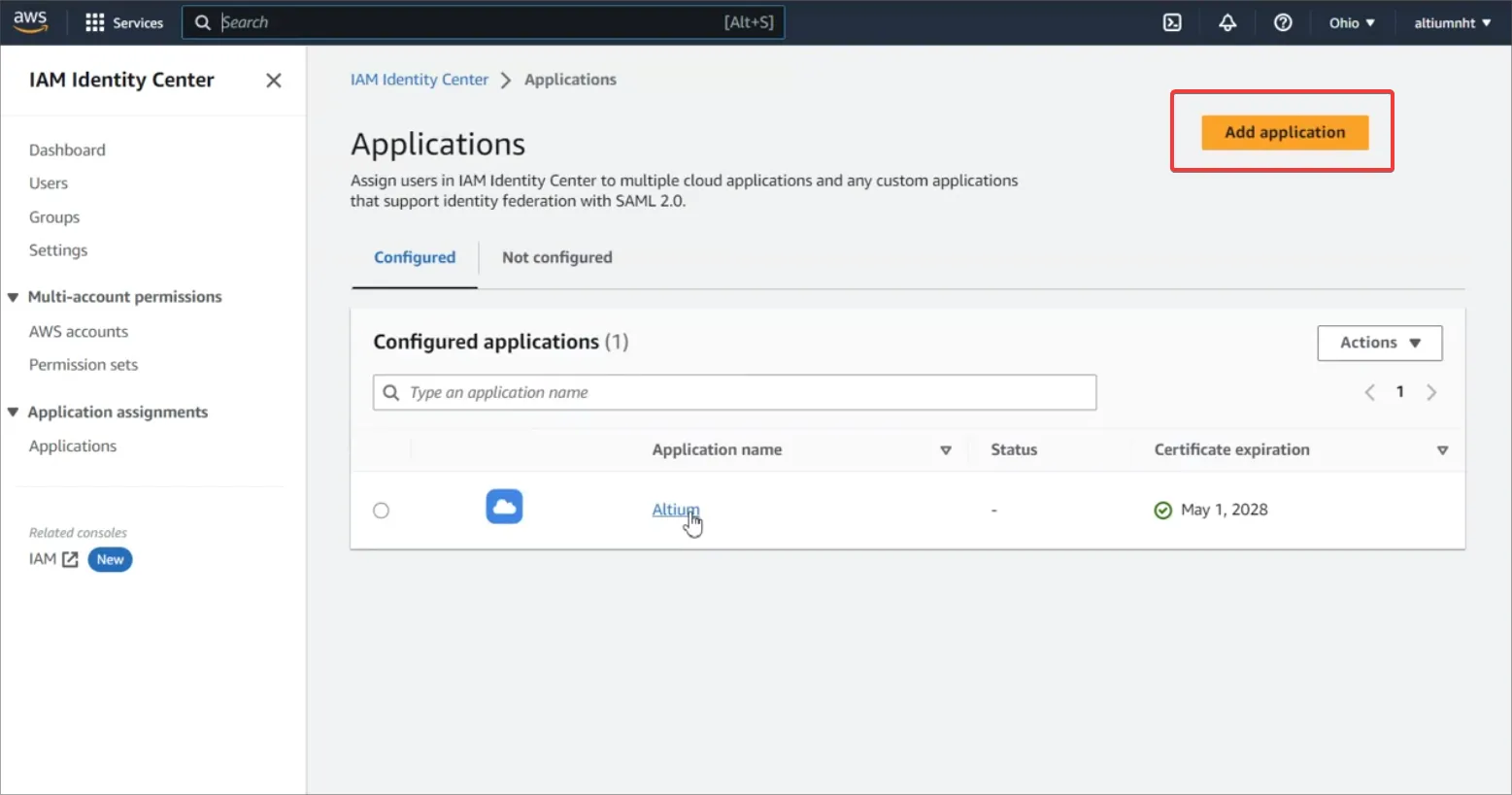
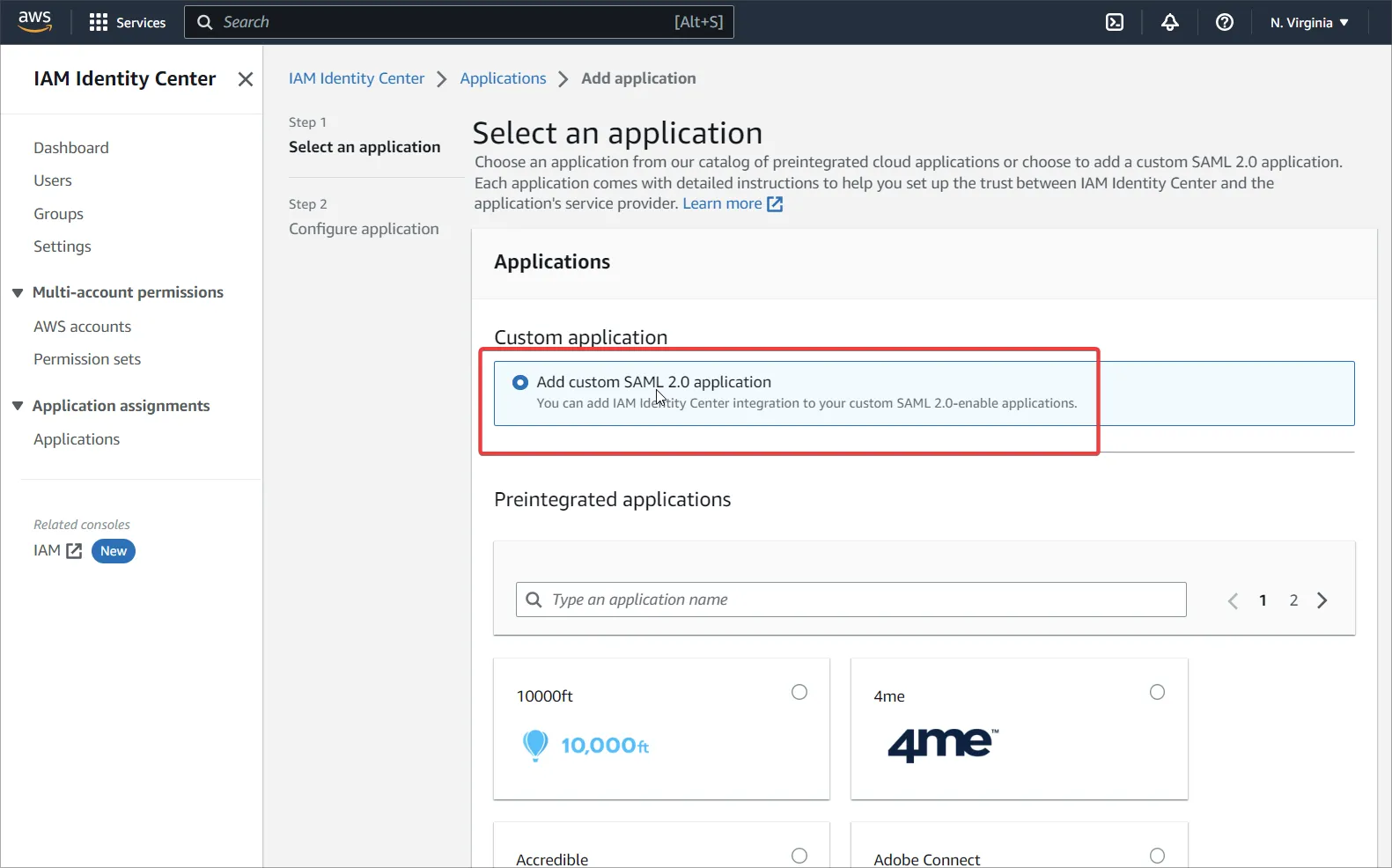
-
Altium SSO ページの AWS メタデータ URL 設定を入力します。Submit で設定を確定します。

-
IAM Identity Center metadata 領域からメタデータファイルをダウンロードします。
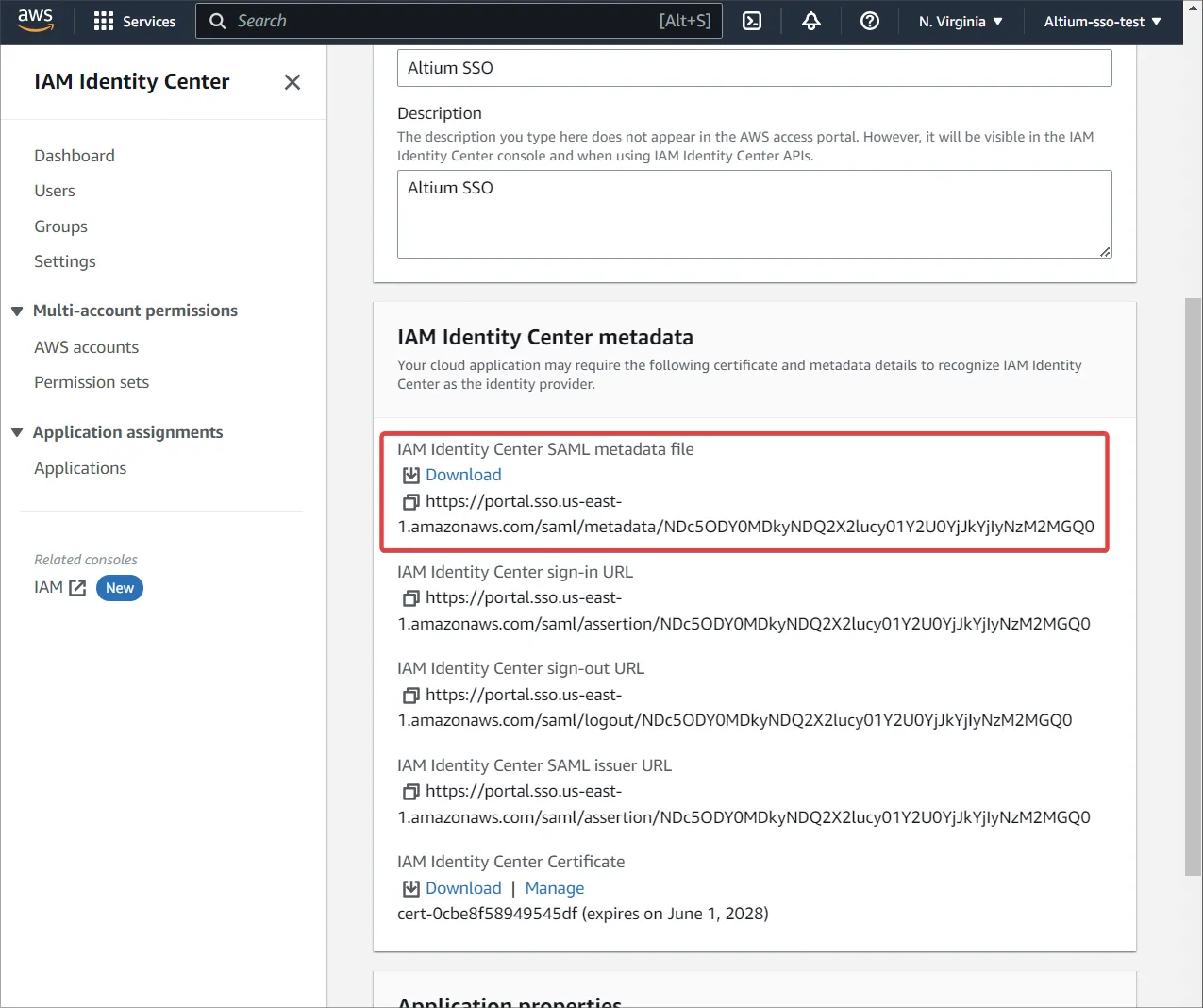
-
Edit attribute mappings に移動します。
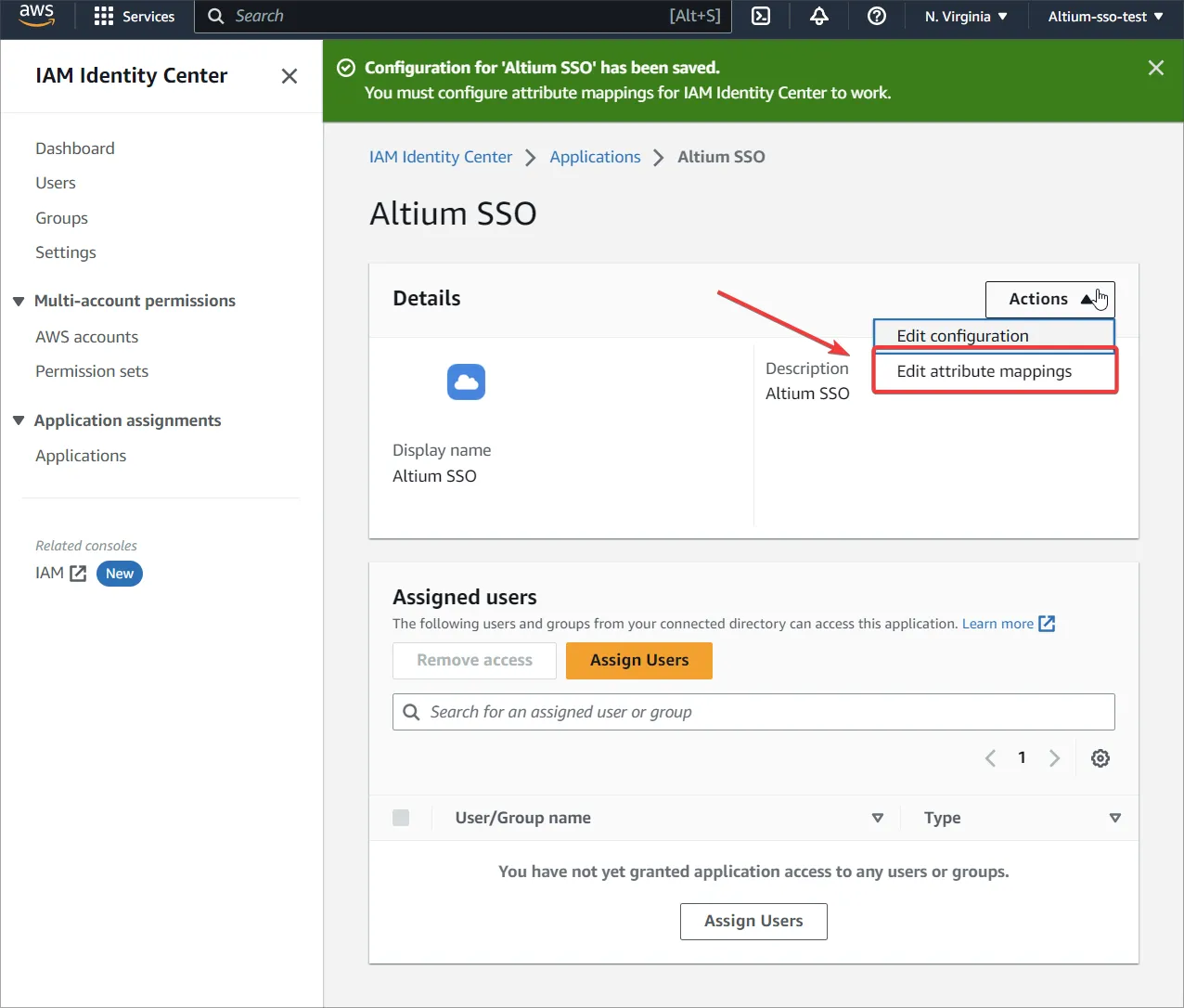
-
Enterprise Server ユーザーのユーザー名を含む属性を指定し、Format には unspecified を選択します。
-
AWS で新規ユーザーを作成し、作成したユーザーまたはグループにアプリケーションを割り当てます。
-
Altium 側と IAM 側の両方に同一のユーザーが存在することを確認します。
-
メタデータ XML ファイルを Enterprise Server のブラウザインターフェースの Admin – Settings – Authentication ページにアップロードし、その後 SAML 統合接続をテストします – 上記参照。
OAuth / OIDC シングルサインオン
Enterprise Server の SSO 機能は、OAuth / OIDC 標準を使用して構成することもできます。ブラウザインターフェースの Admin – Settings – Authentication ページにある SSO ドロップダウンで OAuth / OIDC オプションを選択すると、選択した IdP から提供されるデータを入力できるようになります。

SSO は、 ボタンで実行する統合テストを行うまで有効になりません。このテストにより、SSO のアイデンティティ処理と、貴社の SSO サインインが検証されます。構成のテストが成功したら、
ボタンで実行する統合テストを行うまで有効になりません。このテストにより、SSO のアイデンティティ処理と、貴社の SSO サインインが検証されます。構成のテストが成功したら、 ボタン(
ボタン( )をクリックして設定を保存し、Enterprise Server に適用します。
)をクリックして設定を保存し、Enterprise Server に適用します。
その後、手動または構成変更に伴って SSO が無効化された場合は、 ボタンが利用可能になり、テストプロセスを再実行できます。
ボタンが利用可能になり、テストプロセスを再実行できます。
Entra ID を使用する場合、OAuth エンドポイントには 2 つの API バージョンがある点に注意してください:
これらのいずれかのバリアントから、正しいエンドポイント一式(token/authorize/userinfo)を取得する必要があります。混在させると、Enterprise Server から Entra ID への接続確立を試みた際にエラーになります。